Compliance Services
CMMC Overview: Compliance Basics for Contractors
November 15, 2022
5 Minutes

Cybercrime has skyrocketed since the beginning of 2020. For important sectors such as the US critical infrastructure, cyberattacks have doubled over the last year. It is no wonder, then, that the Department of Defense (DoD) has created a compliance program to ensure sensitive government information is protected.
This program, known currently as CMMC 2.0, has several practice guidelines and level requirements depending on the data your business handles. The US Department of Defense created the CMMC to ensure any organizations working with it will implement the highest cybersecurity standards to protect sensitive data.
Sign up for our newsletter!
But, how does CMMC affect contractors? Check out the resources below to learn more about this government compliance program and why it’s important.
If your organization needs to get CMMC certified, but you want to know if you are prepared, download our Checklist: How to Prepare for a CMMC Assessment.
CMMC: Compliance for Government Contractors
The Cybersecurity Maturity Model Certification (CMMC 2.0) program is a compliance framework set up by the Department of Defense (DoD). It is meant to ensure all contractors have certain data safety practices in place.

Any contractors wishing to work with the DoD will be required to comply with CMMC 2.0. Depending on the type of contract you wish to earn and the kind of data your organization will handle, you will be expected to comply with one of three CMMC 2.0 levels.
The Department of Defense released the CMMC 2.0 model in November of 2021. However, the DoD announced that it expects to issue final regulations by March of 2023. So CMMC requirements could appear in solicitations and contracts as early as the spring of 2023.
To see an in-depth definition of CMMC and read about who is required to comply, check out the blog What is CMMC Compliance?
Why Is It Important for Contractors to Begin the Process of Achieving CMMC Compliance?
For one, the process to achieve CMMC compliance takes a long time. At a recent conference titled CMMC Day, the Department of Defense announced that it plans to issue final CMMC rules by March 2023. In fact, CMMC director Stacy Bostjanick explained her team members “are working as fast as we possibly can so we can get the ecosystem kicked into gear.”
If the timeline proposed by the Department of Defense does not change, and requirements appear in solicitations as early as Spring of 2023, it is important to be prepared to undergo the assessment process. Therefore, contractors should consider reviewing their compliance standing with a cybersecurity expert.
To learn about the CMMC requirements, its different compliance levels, and what they entail check out the blog Explaining the Department of Defense’s (DoD) CMMC Requirements.
Another reason why CMMC compliance is necessary is that the program was created to protect sensitive government information from external enemies or nation states that could use this data to jeopardize the safety of our critical infrastructure or weaken national security.
But, what kind of information does the CMMC protect?
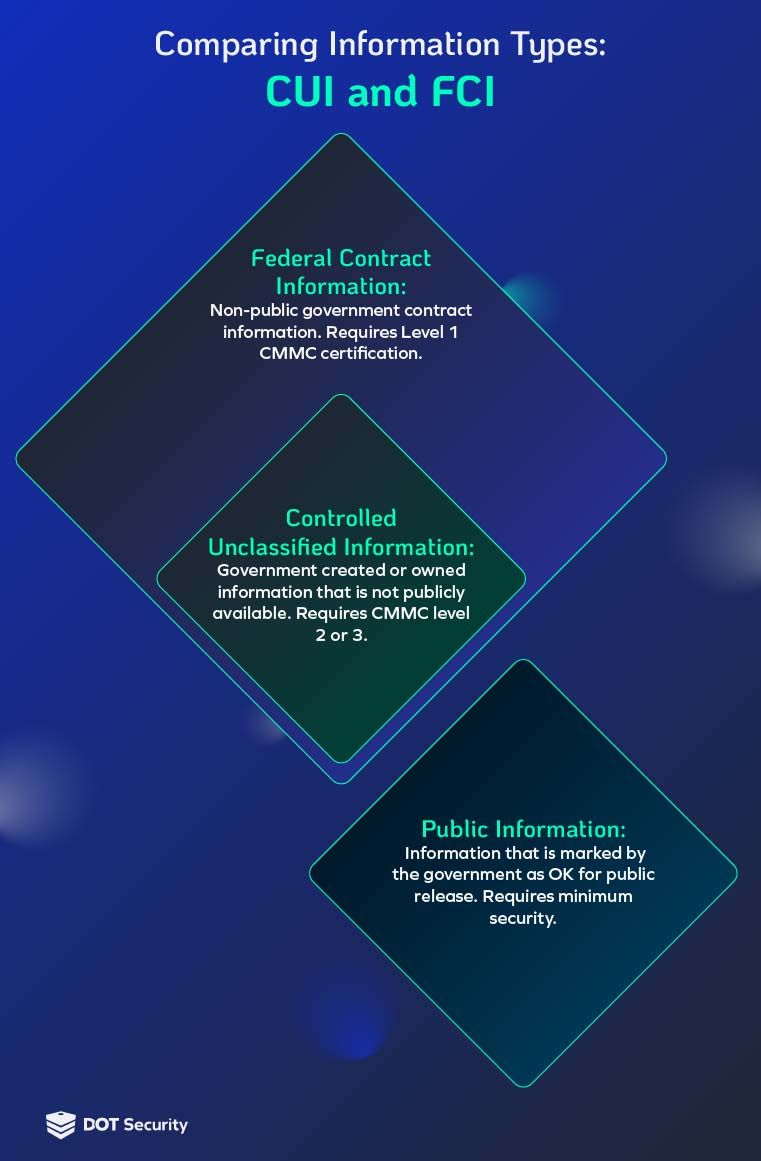
Controlled Unclassified Information (CUI)
Controlled unclassified information or CUI is highly sensitive government information that requires safeguarding and may be subject to dissemination controls.
Although this information has not been classified, the government requires any contractors to protect CUI from unauthorized access or release.
The clause 32 CFR Part 2002 defines CUI as “information the government creates or possesses, or that an entity creates or possesses for or on behalf of the government, that a law, regulation or [government policy] requires or permits an agency to handle using safeguarding or dissemination controls.”
As an example, let’s say a contractor working on a critical infrastructure facility, such as an energy production facility, shared information such as the way the energy is transported or generated without following proper CMMC guidelines.
This could potentially endanger the safety of the critical energy infrastructure and cause a major energy crisis in the US. Not only would the facility be affected, but also any other areas that were dependent on that energy supply.
Federal contract information (FCI)
Federal contract information, or FCI, is information not marked as public or for public release and is provided by or generated for the U.S. government under contract.
In simpler terms, this is information and documentation exchanged with the government that is related to a government contract. If you are a contractor in the Defense Industrial Base, you handle FCI.
The original definition of FCI by the Federal Acquisition Regulation (FAR) clause FAR 52.204-21 is "any communication or representation of knowledge such as facts, data, or opinions, in any medium or form, including textual, numerical, graphic, cartographic, narrative, or audiovisual.”
As an example, let’s say a contractor has been granted a contract with the DoD. They then exchange emails or correspondence with the DoD about their contract. If not safeguarded, this information could be leaked and made public. Therefore, these email exchanges would be considered FCI and protected by the CMMC.
To learn about other types of compliance regulations that may affect your business, check out the blog 11 Things You Need to Know about Cybersecurity Compliance.
Why is Data Security Important for Contractors?
Data security ensures that sensitive information does not fall into the wrong hands or gets used for unlawful or harmful purposes. Data breaches have caused great damage in the US, not only financially but also by endangering critical infrastructure and national security.
The ransomware attack on the Colonial Pipeline, for instance, caused operations in this oil pipeline to cease for a number of days.
The Colonial Pipeline, which runs from Texas travelling north all the way to New Jersey, is considered critical infrastructure since it generates about 45% of the East Coast fuel supply. This attack, caused by an exposed password, could have been avoided if the correct security protocols had been in place.
Data security is crucial not only to protect critical infrastructure, but also to ensure your business operations do not get interrupted by downtime, supply disruptions, or closure, at worst.
To learn more about the importance of safeguarding data, check out the blog What is Data Security and Why is it Important?
Takeaways
- CMMC requirements could appear in contracts with the Department of Defense as early as the Spring of 2023. Contractors who wish to earn a contract with the DoD should begin the CMMC certification process.
- The CMMC was created to protect sensitive government information. If disseminated to non-involved parties, national security and critical infrastructure could be endangered.
- The two types of data CMMC protects are CUI and FCI.
- Contractors should ensure they have the proper protocols in place to protect data, ensure business continuity, and safeguard government information.
To learn about what you need as a contractor to prepare for a CMMC assessment and whether your organization has implemented the security practices to pass, use our downloadable Checklist: How to Prepare for a CMMC Assessment.
