Network Security Monitoring
What Is a “Golden SAML” Attack and Why Should You Be Concerned?
October 18, 2021
4 minutes

This post was contributed to the DOT Security blog by Laura Schwartzwald, Cybersecurity Analyst. Schwartzwald has been in the cybersecurity space for several years and has a demonstrated history of working in computer and network security analysis with security firm Trustwave before moving to DOT Security.
Does your organization use SSO (single sign-on) with multi-factor authentication (MFA) and believe that you are safe from attacks?
If you are using SAML 2.0 protocol as an SSO mechanism with Active Directory Federation Services (AD FS), then you could be vulnerable to a “Golden SAML” attack.
The concept of a “Golden SAML” attack was discovered back in 2017 by CyberArk, an identity security and access management company.
Signup for our newsletter!!
Up until December 2020, the “Golden SAML” attack was only a concept—now it’s been seen in the wild as an elaborate supply-chain attack in the SolarWinds Orion compromise.
In this post, you will learn about SAML authentication, what a “Golden SAML” attack is, why you should be concerned, and what actions to take to mitigate potential risks against attack.
What Is SAML?
Security Assertion Markup Language (SAML) is an open standard that enables authentication between an identity provider (idP) and a service provider (sP) to allow users to access services.
The identity provider (IDP) authenticates the user and then passes an authentication access token to the service provider (sP), allowing the service provider (sP) to operate without having to authenticate the user on its end.
An identity provider would be a service like Microsoft Active Directory Federation Services (AD FS), while a service provider is a service that the user is trying to access (i.e., Outlook 365).
In layman’s terms, you can use one set of credentials to log onto many different websites (Single Sign-On).
What Is a “Golden SAML” attack?
For the “Golden SAML” attack to be successful, an attacker needs to have control over an Active Directory Federation Services (AD FS) user account at a minimum, if not domain admin access.
The takeover of an AD FS user account can be done by using a tool like Mimikatz, an open-source credential dumping tool.
From there the attacker can sign in as the forged user to obtain access to the token-signing certificate and private key.
With the private key and token-signing certificate, the adversary can then create a forged SAML response object, which is an important component of the SAML authentication process in that an identity provider (idP) receives a SAML authentication request from the service producer (sP). This is the attempt from the user to gain access.
In a normal exchange, the identity provider would receive that request and authenticate the user creating that SAML response.
The response is then sent back to the service provider that is signed and encrypted with the user’s private key.
However, in a “Golden SAML” attack, the attacker already has the key that signs the SAML response, thus bypassing the authentication request from the service provider (sP).
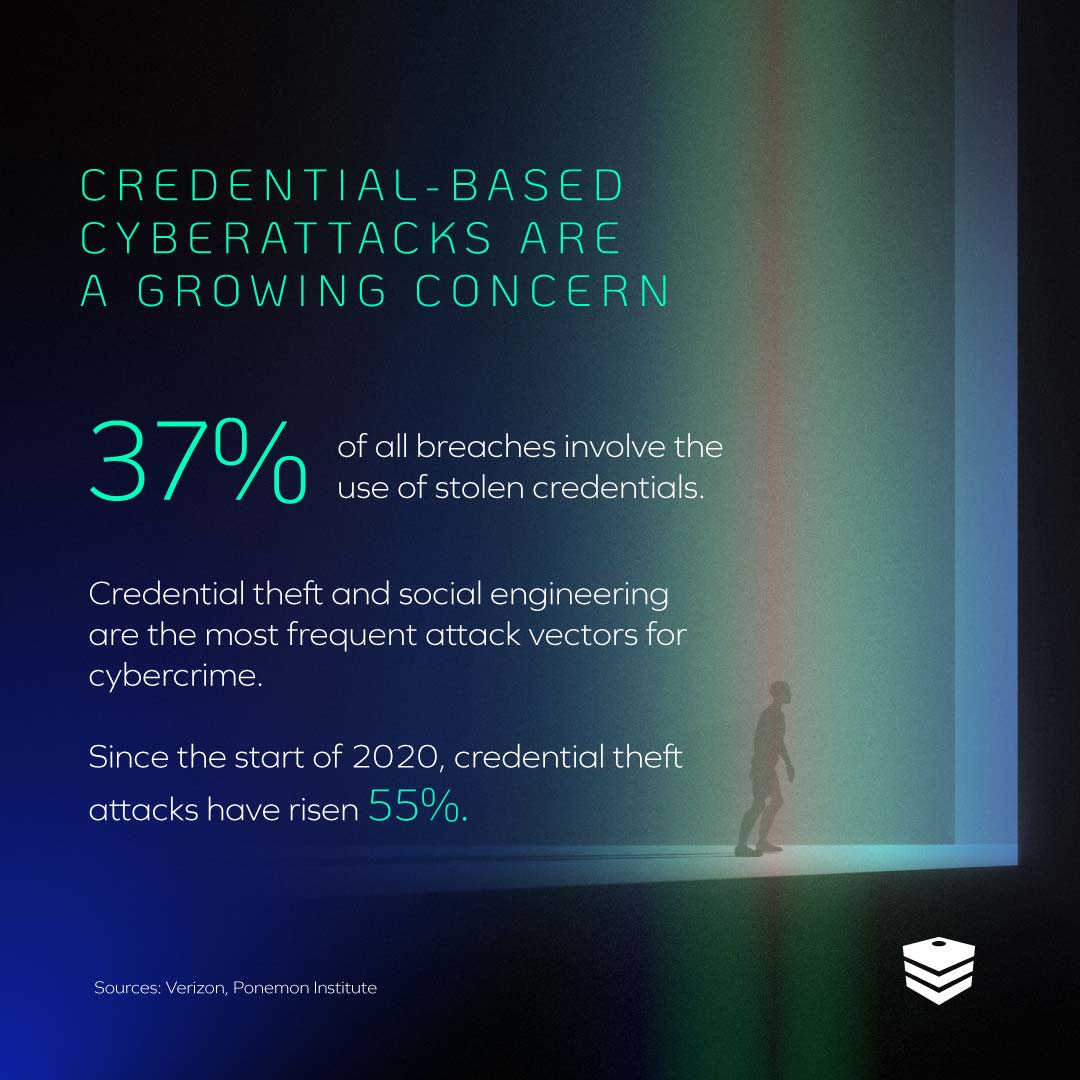
Why Should You Be Concerned?
Detection
Detection of a Golden SAML attack can be difficult and can go unnoticed due to the stealthy nature of this type of attack.
In addition, many organizations are not aware of this attack vector and do not monitor for SAML authentication.
Flexibility
An attacker can impersonate any identity and gain access to assets and services across an enterprise that is a part of the federation, making SAML attacks particularly dangerous.
Bypass Multi-Factor Authentication
With traditional MFA, the users obtain a valid SAML token after they’ve authenticated with their two factors.
Using Golden SAML, the attacker does not need to go through that process instead they bypass it by using the stolen certificate to forge an identity.
The attacker doesn’t even have to know the user’s password or their additional authentication methods.
Persistency
This attack vector allows the adversary to gain a foothold into your environment and move laterally through services for long periods of time without being noticed.
How Can Golden SAML Attacks Be Mitigated?
Since Golden SAML attacks are difficult to detect, you will want to implement some of these mitigation tips:
- By default, the token signing certificate is valid for one year. Changing the token signing certificate more frequently will help to re-establish trust across the entire federation.
- Follow your federation Identity Provider (idP) vendor’s best practices, for example here is a link to Microsoft’s best practices for Active Directory Federation Services.
- Search for Windows Event ID 1007 in the Windows ADFS server logs to look for certificate exports. Certificate exports are rarely seen for legitimate purposes and can be an indicator that an adversary carried out a Golden SAML attack
- Implement an Endpoint Detection and Response (EDR) solution and a Hardware Security Module (HSM) to store your token signing certificates. By keeping your token signing certificates in an HSM, it will make it more difficult for attackers to steal data and information.
Final Thoughts
Now you should have a good high-level understanding of what SAML authentication is, and how an attacker can carry out a Golden SAML attack.
The persistent nature of a Golden SAML attack and the difficulty of detecting them, coupled with the widespread use of single sign-on (SSO) and Active Directory Federation Services (AD FS) in enterprises today makes it an ideal attack vector for cybercriminals.
The attacker can bypass traditional security measures while escalating their privileges to move laterally throughout your network with impunity.
It is important to have defense in depth or additional layers of security in your organization in order to properly defend against attacks like these.
Attack vectors like the Golden SAML approach that bypass user authentication and authorization mechanisms are considered major threats to modern organizations and measures should be taken by all businesses to ensure hackers have no easy way into a company network.
