Identity And Access Management
Infographic: 6 Red Flags to Recognize and Avoid Phishing Scams!
February 04, 2025
7 minute read

Phishing scams are an increasingly common aspect of daily life, and these malicious emails are likely sitting in the spam folder of your email account right now, waiting to be opened.
The volume of phishing attacks doubled between the first and second half of 2024. This showcases just how much global phishing activity there is and how accessible a phishing cyberattack can be. As they become a more prevalent issue for companies, there are certain signs to look out for that clearly indicate when a message is legitimate or when it’s a phishing scam.
Sign up for our newsletter!
The infographic below on how to spot a phishing email will cover the six indicators that a message may actually be an attack.
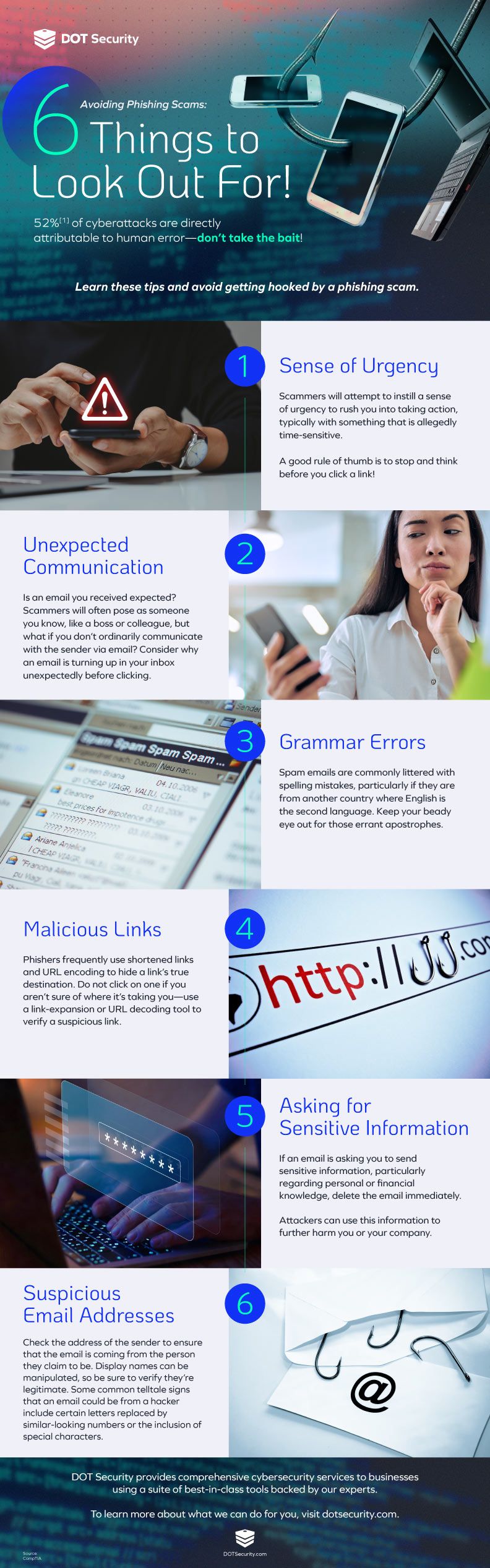
Phishing Awareness from the Infographic
- Sense of urgency
- Unexpected communication
- Grammar errors
- Malicious links
- Asking for sensitive information
- Suspicious email addresses
1. Sense of Urgency
Scammers will attempt to instill a sense of urgency to rush you into taking action, typically with something that is allegedly time-sensitive. By threatening a negative consequence, attackers can hasten your response, preventing you from catching inconsistencies in the email.
A good rule of thumb is to stop and think before you click a link! Anyone contacting you via email rarely requires a response that quickly.
2. Unexpected Communication
Is an email you received expected? Scammers will often pose as someone you know, like a boss or colleague, but what if you don’t ordinarily communicate with the sender via email? Or even if you do, why are they sending this message today?
Consider why an email is turning up in your inbox unexpectedly before clicking. If the email appears to come from someone you know, reach out to them through an alternative route, such as in person or via phone call, to check.
3. Grammatical Errors
Spam emails are commonly littered with spelling mistakes, particularly if they are from another country where English is the second language. Keep your eye out for those errant apostrophes or incorrect verbiage, as many companies use spell-checking tools to ensure professionalism.
One or two mistakes can be human, but too many may indicate something worse than an unnoticed spelling error.
4. Malicious Links
Phishers frequently use shortened links and URL encoding to hide a link’s true destination. Do not click on one if you aren’t sure of where it’s taking you—use a link-expansion or URL decoding tool to verify a suspicious link.
Keep in mind that just visiting a malicious site, even if you don’t actively click to download anything, can be enough to get malware on your computer.
5. Asking for Sensitive Information
If an email asks you to send sensitive information, particularly regarding personal or financial knowledge, delete the email immediately. Hackers can create fake login pages that resemble the real, original ones. They also may use emails to request payment.
Attackers can use this information to further harm you or your company, and legitimate sources should have other, more secure, ways to access this data.
6. Suspicious Email Addresses
Check the address of the sender to ensure that the email is coming from the person they claim to be. Display names can be manipulated, so be sure to verify they’re legitimate.
Some common telltale signs that an email could be from a hacker include certain letters replaced by similar-looking numbers (like “0” for “o”) or the inclusion of special characters.
How AI Has Accelerated Phishing Attacks
AI has had a profound impact on the way businesses operate, from consumer communication to data analytics. But these aren’t the only groups leveraging the advanced technology. Hackers and black market dealers use AI to create phishing attacks that are more targeted, convincing, and difficult to detect.
Cybercriminals now harness AI to craft highly personalized phishing messages by analyzing massive amounts of publicly available data from social media, professional networks, and online activity. These AI-generated emails and messages mimic the tone, style, and content of legitimate communications, increasing the likelihood of success.
Further, AI-driven phishing campaigns can dynamically adapt to their targets. Machine learning algorithms assess the efficacy of initial attempts and refine strategies in real-time, adjusting content or timing to exploit vulnerabilities.
On top of this, phishing kits powered by AI also enable attackers to bypass traditional security measures, such as spam filters, by creating ever-evolving email formats and using natural language processing to evade detection. Not only are the phishing attacks themselves more sophisticated, but they’re more accessible. With AI, even a novice hacker can whip up complex phishing attacks with ease.
This combination of sophistication, accessibility, and scalability has elevated phishing to a new level of efficacy, posing significant challenges for individuals and organizations alike.
Wrapping Up on Recognizing and Avoiding Phishing Scams
When it comes to staying safe online, either in the workplace or as an individual user, recognizing and avoiding phishing scams is crucial. As AI continues to rapidly advance, bringing sophisticated tools to the fingertips of novice hackers, and we see the volume of phishing attacks on the rise year over year, it’s more important than ever to be cybersecurity conscious.
Businesses and individuals should start by doing what they can, installing an antivirus and a firewall, using a password manager, and most importantly, learning the tell-tale signs of a phishing email so you can be sure to avoid them all together.
Phishing isn’t the only type of social engineering scheme or cybersecurity attack that your business needs to protect itself from. Look through DOT Security’s Common Vulnerabilities in Cybersecurity & How to Stop Them checklist to learn more about the modern threats in the cybersecurity space.
