Secure Data Protection
Supply Chain Cybersecurity: Why the Rise In Attacks?
February 23, 2022
5 minutes

Attacks on business supply chains have raised concerns about their ability to navigate disruption as far as supply chain cybersecurity is concerned—what influence does this have on companies today?
Supply chain cybersecurity is in greater focus today than perhaps it’s ever been—particularly as attacks and cybercriminals more frequently target organizations that participate in critical infrastructure supply chains.
Sign up for our newsletter!
In this blog, we’ll be taking a look at the rise in cyberattacks on supply chains and what the landscape for securing this vital infrastructure will look like in future.
Background
It shouldn’t come as too much of a surprise that when it comes to cybersecurity, concerns over supply chains are greater than for other aspects of business, as they can have an enormous knock-on effect to other organizations in the supply chain ecosystem.
Supply chain attacks rose by 42% in the first quarter of 2021 in the US, impacting up to seven million people, according to research.
As attackers look to suppliers and SMBs as viable targets of attack, it’s incumbent on businesses to ensure they have the necessary protections and protocols to ensure their defense is adequate against emerging threats.
In 2021, cyberattacks on supply chains were anticipated to multiply four times over 2020, an astonishing rise that should send alarm bells ringing in the ears of organizations all across the country.
What Is a Supply Chain?
A supply chain refers to the ecosystem of businesses and processes that are necessary to create, manufacture, and distribute a product.
Organizations operating in a supply chain often share data with one another, meaning security is essential in maintaining information integrity—and conversely, in the event of a breach, sensitive data from businesses across the chain can be compromised.
Why Is Supply Chain Cybersecurity Lacking?
Many companies that operate in supply chains have some cybersecurity protections—it’s often the case that organizations have some kind of legacy application like an antivirus for their network.
The problem is, maintaining a modern and effective cybersecurity posture today involves many elements that are often unaccounted for by businesses.
Consider, for example, the weakness of many in validating security among third-party apps. 66% of report incidents regarding supply chain attacks showed a proclivity among hackers to focus on suppliers’ code for apps.
In short, attackers increasingly look to compromise software applications, which then have a trickle-down effect to users (companies using the software) which can then expose valuable data from which they can profit.
In this example, organizations that are not properly securing their third-party app data are at a clear disadvantage, and this is one of the reasons it’s so important for businesses to invest in a comprehensive security tech solutions stack.
Of 58% of supply chain attacks assessed, the most targeted data sets contained information relating to customer data, including personally identifiable information (PII) and intellectual property.
In two-thirds of supply chain attacks analyzed, suppliers did not know or failed to report on how they were compromised.
To sum up, when supply chain attacks occur, many of the victims are unable to prevent them, unable to remove them from their systems, and unable to understand why they were compromised.
This should be extremely concerning to any organizations that do not have strong visibility and protection of their supply chains.
What Should You Expect In a Cybersecurity Tech Stack?
With all that being said, let’s look at the solutions the are necessary to include in an ideal cybersecurity tech stack.
These solutions allow organizations to effectively monitor and protect their data so that the possibility of being breached is minimized.
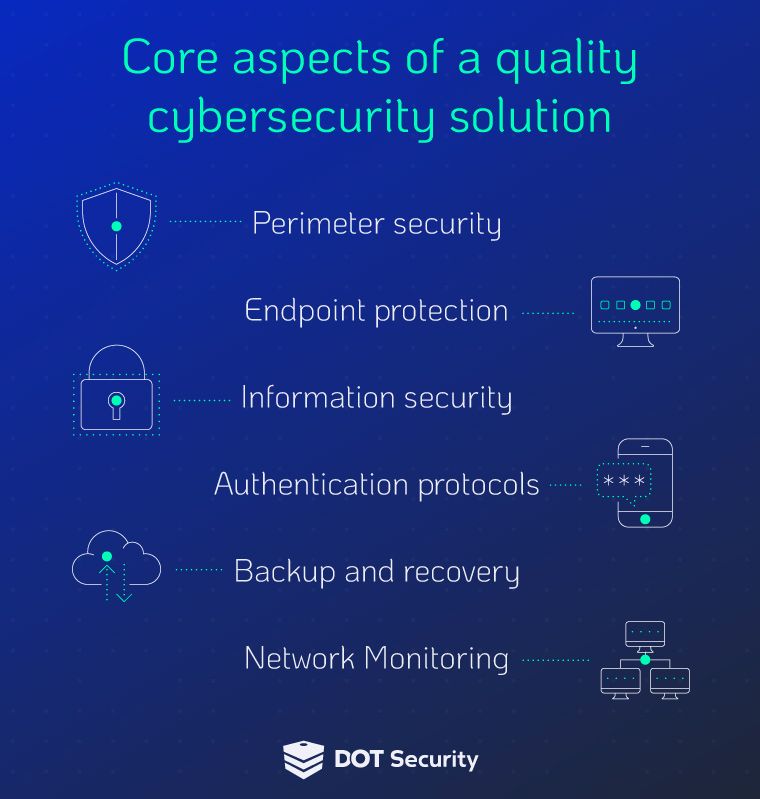
Perimeter security
Perimeter security solutions protect data between a private internal network and an external public-facing network.
Unified threat management is a comprehensive solution that will include a lot of tech that you’re likely already familiar with. Antivirus; firewall; intrusion detection; spam filtering; content filtering; and in some cases, VPN support for encrypted communications.
A web application firewall, or WAF, is similar, but focuses on data traveling between the end user and the cloud app they’re using.
Because so many businesses today store, handle, and access data in the cloud on third-party solutions, WAFs have become important tools to supplement cybersecurity strategies.
Endpoint protection
Managed detection and response (MDR) is an endpoint protection service that detects, prevents, and responds to attacks across all vectors.
As opposed to searching for the characteristics of malware—which can be hidden or changed to something unrecognizable—as a traditional protection service would, MDR monitors the processes of every endpoint, recognizing deviations from the norm and responding.
Then there’s persistence detection. “Persistence” refers to a modern hacking process, whereby cybercriminals gain access to your systems and wait for the opportune moment to strike by lingering silently in the background undetected.
Information security
Information security is all about access and stopping inadvertent data loss. Data loss prevention (DLP), for example, is about preventing data leakage, which refers to the unauthorized transfer of data from inside your organization to outside.
DLP aims to rectify this issue by establishing clear standards for your data through labeling and categorizing. This means determining where certain data should be stored, who has access to it, and where it can be shared.
Authentication protocols
Multifactor authentication (MFA), which requires the use of a secondary device or method to authenticate a user, has proven especially useful in preventing breaches, and solutions that cater to this are capable of protecting every app or software service you use; in addition to meeting modern compliance standards.
Backup and disaster recovery
Backup and disaster recovery (BDR) services are aimed at making sure that any vulnerable information in your business, whether it’s data stored on internal servers, external cloud data, or website data, is backed up and can be restored instantly.
Today, this will typically be done through image-based backups on cloud servers, which have the added benefit of being able to restore applications and partitions as well as files.
Network monitoring
Monitoring tools provide total visibility into your network and find vulnerabilities.
These tools include vulnerability scanning, security information and event management (SIEM), and network detection and response (NDR).
Vulnerability scanners use machine learning to automatically assess risks associated with functions and processes across your hybrid network—whether in the cloud or internally.
Bottom Line
Supply chain cybersecurity is a topic of major concern among organizations today, and it’s important for those who are lagging in their cybersecurity maturity to have a risk assessment conducted to understand what their gaps are and how to remedy them.
If you’d like to know more about how you can put a plan in place for cybersecurity for the future, contact DOT Security today.
