Endpoint Protection
Understanding USB Device Security and How to Protect Against Threats
February 02, 2022
3 minutes

This post was contributed by David Konstant, Associate Penetration Tester for DOT Security. Konstant holds a bachelor’s degree in Cybersecurity and Information Assurance and is deeply committed to knowledge sharing to protect people from cyber criminals.
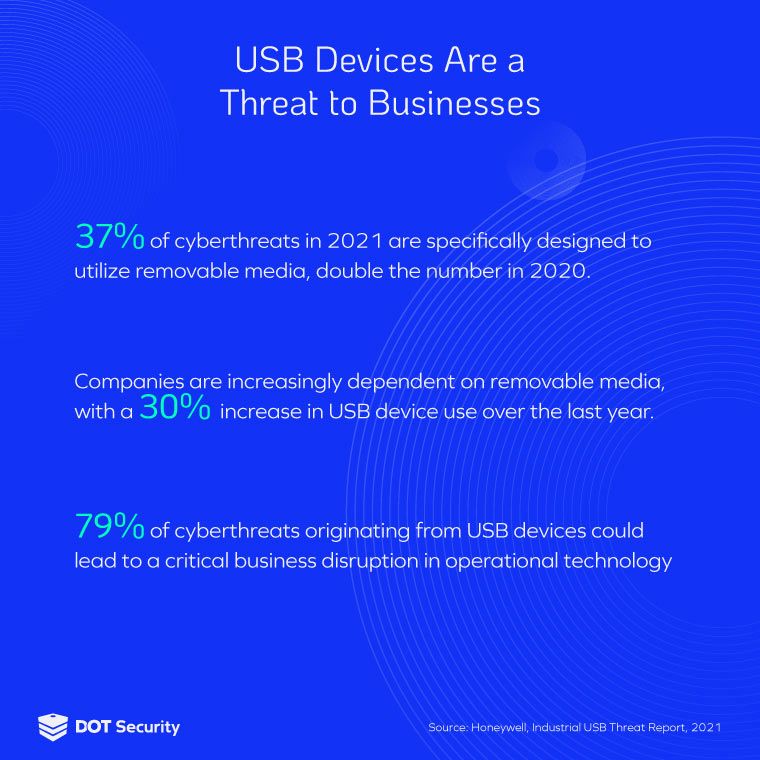
Prevention of falling victim to phishing has been a significant focus of security training in the last few years, but it is not the only attack vector that cyber criminals utilize.
Sign up for our newsletter!
In fact, some of the most famous and dangerous attacks have occurred as a result of plugging in a simple USB device.
USB attacks have been making headlines for many years—from the famed Stuxnet worm that caused serious damage to Iran’s nuclear program in 2010 to more recent ransomware attacks perpetrated by the financially motivated Russian cybercriminal group FIN7.
While USB attacks can be exceptionally effective in the wrong hands, there are a number of ways to protect yourself and your organization from breaches.
Dangers posed by USB devices
In 2017, Ben-Gurion University’s Cyber Security Research center identified 29 different types of USB-based computer attacks.
As you may expect, these attacks range widely in complexity and methods.
Examples include USB devices that inject scripts to perform malicious activities like downloading malware, recording and sending keystrokes back to attackers, and providing backdoor access to systems that are otherwise protected.
As reported in January 2022, the FBI warned US companies that the FIN7 group had been sending packages via the United States Postal Service (USPS) and United Parcel Service (UPS) containing USB devices that registered as a keyboard when plugged in, but actually installed malware that can lead to ransomware attacks.
Other recent attacks involved similarly mailed USB devices along with fake gift cards, thank you notes, and other ways to trick people into plugging in devices.
Because these devices appear as harmless devices like keyboards, they can go undetected for months or years while collecting data, proving backdoor access to air-gapped systems, and more.
How to Protect Your Organization
Protection against USB-based attacks can be broken down into three categories: USB device restriction via technical controls, managed detection and response (MDR) agents, and security awareness training (SAT).
Restricting USB devices can be done by either creating blacklists or whitelists like traditional lists for content filtering.
One way to do this is via Microsoft Windows Group Policy to set a list of approved USB devices by their hardware ID and not allowing access to any other USB device.
Many MDR agents also allow administrators to create such rules.
In addition to being able to whitelist or blacklist specific USB devices, MDR solutions are a powerful tool to protect against USB attacks.
These solutions combine analytics, threat hunting, and trained staff to monitor and correlate logs and events to determine if there is an existing threat.
If a USB device gets plugged in and bypasses USB restriction controls by spoofing the hardware ID, the next best line of defense is an MDR solution that can identify and stop the actual activity that the attacker wishes to carry out.
These solutions provide significantly superior protection compared to traditional antivirus software and are a necessity for enterprise-level security.
Finally, companies should provide security awareness training to staff so that employees can identify cyber security threats and avoid plugging in unknown USB devices.
Employees should be trained to turn in any suspicious devices to trained staff for safe handling and analysis.
It is the job of everyone in an organization to understand these threats and stop them in their tracks.
Takeaways
Social engineering attacks take advantage of human nature, like the desire to help others and curiosity.
Cybercrime is big business, and several advanced persistent threat (APT) actors rely on social engineering to get an initial foothold into their target systems.
By combining education, USB device restrictions, and advanced tools that are monitored by trained staff, we can all do our part to prevent the next ransomware attack and major data breach.
If your organization needs a plan for cybersecurity and you don’t know where to start, consider having a risk assessment performed by DOT Security, who will take a deep dive into your network and determine what your gaps are and how to address them. For more information, visit our Why DOT? page and learn how we can be the last MSSP you will ever need.
