Network Security Monitoring
What is Network Security Policy Management?
November 11, 2021
5 minutes

With more people working remotely and more devices connecting to business IT networks, there’s a significant increase in attack vectors that can be taken advantage of by cybercriminals.
That’s why it’s more important than ever to have a concrete network security policy in place so that the organization is secure, in compliance, and prepared for the changing cybersecurity environment.
Network security is one part of a whole cybersecurity strategy that is made up of many different parts that each act collectively to increase your security and decrease the chance of your network being penetrated by those with malicious intentions—most often ransomware, spyware, or some other kind of malware.
Sign up for our newsletter!
Protect your data, your employees, and your business by implementing an effective, custom network security policy.
What is Network Security Policy Management?
Network security policy management refers to the process of managing a formal policy or document that outlines an organization’s processes and guidelines to enforce and manage the security of its computer network. Typical network security policy documents will outline:
• The rules and procedures users must follow to access the network • A network management plan • The implementation strategy of cybersecurity procedures • Roles and privileges to identify authorized users and to grant access control to certain systems and information
As mentioned above, a network security policy is just one part of a whole cybersecurity strategy.
Its role within that strategy is to secure an organization’s network through procedures, processes, and best practices.
Management of a network security policy means consistently referencing and updating the policy to ensure it’s still being correctly followed and that its contents are always up to date with the latest cybersecurity trends and strategies.
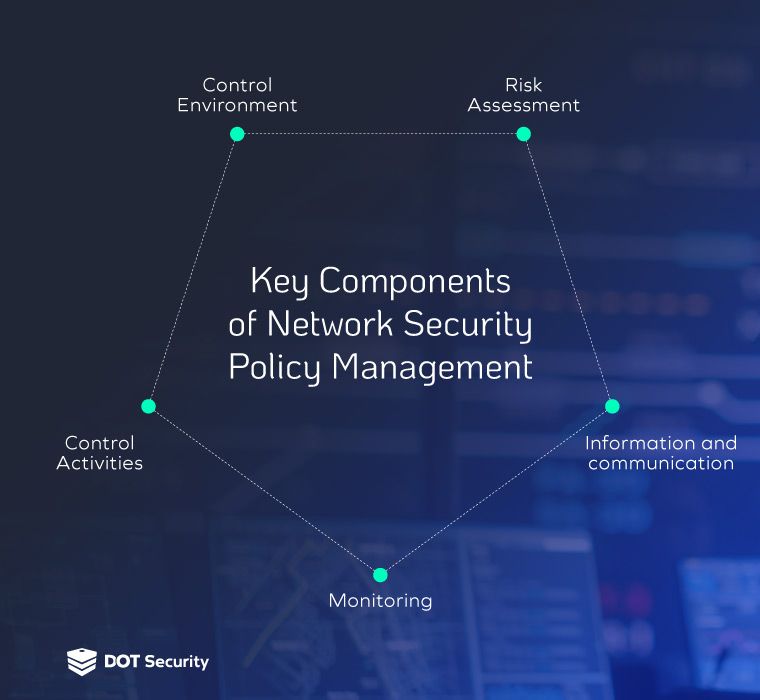
Why is Network Security Policy Management Necessary?
Protecting your customers, employees, and your business is crucial which is why it’s important to have effective network security policy management that delivers strong processes and procedures that keeps your business protected and always on the cutting edge of security.
Unfortunately, many businesses simply don’t have the resources to maintain the appropriate amount of security policy management that’s necessary for complete security coverage.
The costs of maintaining a full internal cybersecurity team are too high for many, though demand for newer solutions (such as threat hunting technologies) and security professionals is higher than ever.
That’s why so many choose to partner with managed security services providers (MSSPs) who have the required staff and expertise to develop and implement network security policies and bring a wealth of experience doing so with many businesses in every industry .
Modern cybercriminals use sophisticated methods to penetrate your network. If you don’t have modern defense solutions to counteract them, the business is at risk.
What Kind of Protocols Can You Expect in a Network Security Policy?
Here’s a quick rundown of some of the most common and most useful network security policies that businesses put into action to protect the integrity of their networks:
Account Management: This policy creates a standard for account creation, management, use, and removal.
Clean Desk: Create policies to make sure sensitive information and data is not accidentally exposed to people walking past workstations.
E-mail: Establish rules detailing how employees can use company emails.
Security Incident Management: Detail the procedures for how people should report and respond to incidents relating to information systems.
Log Management: Explain how your company should manage and organize information logs and reports.
Network Security and VPN Acceptable Use: Define the policy standards for people connecting to the company network from other locations using VPNs to prevent unauthorized use.
Bring Your Own Device (BYOD) Agreement: Define the procedures and restrictions for end users who need to use their own devices connected to the company network.
Passwords and Passphrases: Create a policy that establishes the standards for password/passphrase creation for business accounts.
Patch Management: Establish a policy for the distribution of updates and patches to software on company equipment.
Server Security: Choose the standards for server configuration and management.
Systems Monitoring and Auditing: Decide how to use monitoring and auditing to check for inappropriate activities within an information system.
Vulnerability Assessment: Establish a policy that outlines the standards of occasional vulnerability assessments for the business.
Workstation Configuration Security: Outline the security protocols for employee workstation equipment to ensure all devices are securely configured.
Telecommuting: For remote workforces, this policy defines telecommuting policies for remotely accessing the network.
Benefits of Network Security Policy Management
There are plenty of benefits associated with the implementation of a network security policy, the most obvious of which is enhanced security. But it has plenty of other benefits, too:
• Ease of Use for Stakeholders: The people who have access to your network will benefit from clearly defined processes that make it easier to access necessary data. • Consistency Across Your Company: A consistent security policy that’s followed company-wide will help you maintain compliance with regulations and laws. • Save Time: Establishes processes for things like updates and patches will decrease the downtime required to implement them. • Lower Costs: Good policy management lowers the costs of security thanks to scalability and using fewer resources by centralizing management.
How Can an MSSP Help with Network Security Policy Management?
An MSSP has the tools, expertise, and staff that allows them to perform a true deep dive into a business’ processes and to create and implement a comprehensive network security policy that provides the protocols listed above.
A Risk Audit from DOT Security takes a look up and down your organization to uncover anything worrying that needs to be addressed when developing a policy for network security.
Without a risk audit, there’s no way to know what your business needs to shore up its network security.
Bottom Line
A network security policy establishes the standard procedures that should be followed throughout your organization in order to have network security that protects your entire organization from breaches.
A risk audit from DOT Security can help you discover what exactly your policy needs and how you can best implement it company-wide.
Learn more about network security or the DOT Security risk audit today or contact us to speak with a network security expert.
