Network Security Monitoring
Everything You Need to Know About Automated Pentesting
February 13, 2025
9 minute read

Consider looking at a list of cities from across the world, but instead of being listed by name, they’re in a spreadsheet listed by longitude and latitude coordinates. While it’s technically the same information, the list of coordinates is much harder to understand. Similarly, automated pentesting takes raw vulnerability data and transposes it into easily understandable and actionable insights.
Automated penetration testing takes vulnerability tests to the next level, by providing security professionals with a lot more context, and much more pointed insights with patch suggestions based on their impact to risk reduction.
Sign up for our newsletter!
With advanced features, better insights, and illustrative diagrams, automated pentesting is going to play a huge role in the future of network security.
Subscribe to the DOT Security blog to learn about the latest tech in the cybersecurity space, stay on top of the headlines, and insight into the current best practices.
What Is Penetration Testing?
Penetration testing, also known as ethical hacking, involves hiring a team of security professionals who intentionally try to break into your network. In this process, skilled experts simulate real-world cyberattacks on computer systems, networks, or web applications to expose vulnerabilities. Think of it as a fire drill for your IT infrastructure.
By intentionally probing for weaknesses, organizations can discover where their defenses might fail and patch those gaps before an actual breach occurs.
During a penetration test, professionals blend both automated tools and hands-on techniques to mimic the tactics that cybercriminals use. They start by gathering intelligence on the target system—identifying open ports, outdated software, or misconfigurations—and then try to exploit these vulnerabilities just as a threat actor would.
This might involve attempting to bypass security controls, injecting malicious code, or even tricking systems into revealing sensitive information. Every step is carefully documented, providing a detailed map of potential attack paths and a clear understanding of the risks involved.
Once the simulated attack is complete, the testers compile a comprehensive report that outlines every vulnerability discovered, rates their potential impact, and suggests actionable remedies. This final report is not only a list of problems but also a strategic guide that helps organizations strengthen their cybersecurity measures.
How Does Automated Pentesting Work?
Automated penetration testing leverages sophisticated software tools to mimic the actions of an attacker at lightning speed. Rather than manually probing every system component, these tools systematically scan networks, applications, and databases, rapidly identifying vulnerabilities using pre-defined rules and an ever-evolving library of attack patterns.
Think of it as a tireless digital sentinel that continually monitors your infrastructure, hunting for weak spots before they can be exploited by cybercriminals.
At the heart of automated pentesting is a suite of specialized algorithms that simulate a variety of attack techniques. These tools run an array of tests—from basic port scans and configuration checks to advanced exploit attempts—ensuring that even subtle security gaps are brought to light.
As they work, they aggregate and analyze vast amounts of data, categorizing issues by severity and potential impact. This automated process not only speeds up vulnerability detection but also minimizes human error, ensuring a consistent and thorough security assessment.
One of the most compelling advantages of automated pentesting is its seamless integration with modern development workflows. In agile environments, where code changes rapidly and updates occur continuously, these tools can be embedded directly into the software development lifecycle.
This means that every new deployment is automatically scrutinized for vulnerabilities, providing real-time feedback and allowing teams to address security issues as they arise. Ultimately, automated pentesting transforms vulnerability management into an ongoing, proactive process, enabling organizations to stay one step ahead in the cybersecurity space.
Attack Path Discovery and Visualization
One of the advanced features that makes automated pentesting such an exciting step in the cybersecurity evolution is how the software transforms raw vulnerability data into dynamic visual maps that illustrate how an attacker might navigate through a network. By scanning systems, these tools identify weak spots and use algorithms to chart potential paths an intruder could exploit.
The resulting visualizations often take the form of graphs or flowcharts, where nodes represent individual systems or vulnerabilities and the connecting lines indicate how these can be chained together into a full-scale attack route.
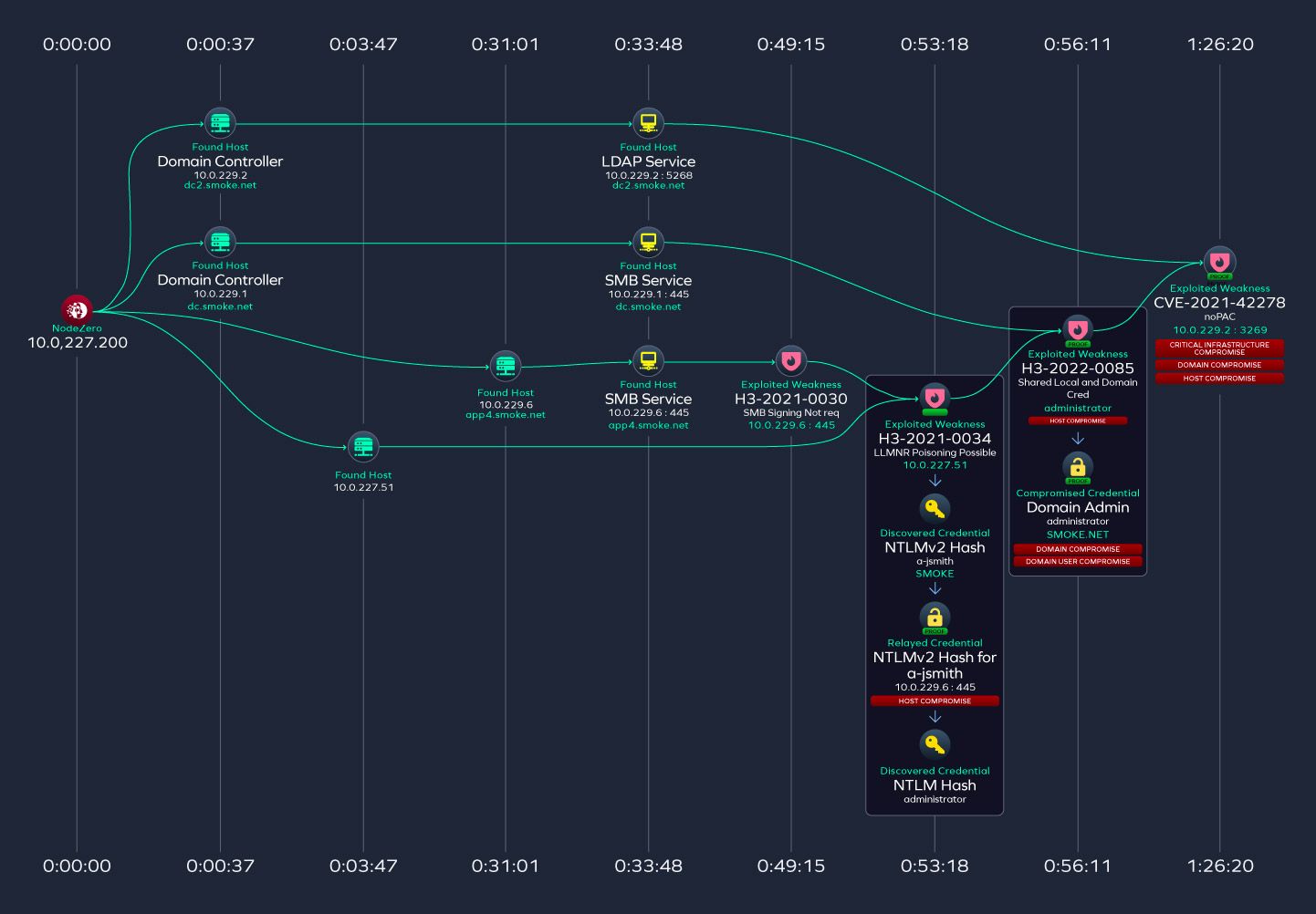
This visualization simplifies complex technical data, making it accessible not only to cybersecurity experts but also to non-technical stakeholders such as management or compliance officers. By seeing a graphical layout of potential threats, decision-makers can quickly grasp where their defenses are most vulnerable and prioritize remediation efforts.
It also aids in understanding the potential cascading effects of a single vulnerability, highlighting how an initial breach can lead to more severe compromises if left unchecked.
Additionally, the visual attack path mapping serves as a strategic tool in ongoing cybersecurity planning. It enables organizations to simulate attack scenarios, evaluate the impact of fixing certain vulnerabilities, and predict how an attacker might move through interconnected systems.
This proactive insight supports more informed decisions regarding resource allocation, targeted security enhancements, and overall risk management.
Exploitation Escalation
Automated pentesting software isn’t just about scanning for vulnerabilities—it’s a dynamic tool that continually updates risk assessments by tracking active exploits in the wild. By integrating real-time threat intelligence feeds, the software monitors the cybersecurity landscape for signs of malicious activity targeting known vulnerabilities.
When a particular flaw is observed being actively exploited, its severity rating is automatically adjusted to reflect the immediate danger, pushing it up the priority list and ensuring that the risk level isn’t just based on static scores but on actual, evolving threats.
This blend of automated scanning and live threat tracking transforms vulnerability management into a more agile and responsive process. By continually adjusting severity ratings to mirror current exploit trends, organizations gain a sharper insight into where they are most vulnerable, and what security gaps need to be filled first.
Simpler Data, Better Insights
Automated pentesting offers a lot of the same insights that a more traditional vulnerability scan does, but goes a step further to contextualize that data, bring in a narrative, and compare it to real-world exploitations. The result is a sorted list of vulnerabilities with their associated volume of attack paths, meaning organizations can achieve massive risk reduction addressing their top vulnerabilities.
The clarity of the data provided by automated pentesting reports is a huge advantage when compared to vulnerability testing due to the sheer volume or data, out of context, that a vulnerability scan generates. In other words, while you can find the same insights in a vulnerability scan report that you get from an automated penetration test, they’re much harder to discover due to the sea of raw data.
Between clear and actionable insights listed out by highest impact to risk reduction, and attack path visualizations – the adoption of automated pentesting in the cybersecurity space marks a major evolution in how we go about understanding network security risks.
Easy Prioritization
Automated pentesting transforms raw vulnerability data into a clear, prioritized roadmap for security teams. By simulating real-world attack scenarios, these tools not only identify weaknesses but also evaluate the practical risk each flaw poses. The result is a ranked list that highlights which vulnerabilities could potentially open the door to the most damaging exploits.
With detailed insights—ranging from severity scores to contextual attack paths—security experts can quickly see which issues demand immediate attention and which ones can be scheduled for later remediation.
This dynamic, prioritized output makes decision-making straightforward. Instead of sifting through endless lists of vulnerabilities, security professionals receive an actionable guide that pinpoints the critical areas of concern. The prioritized recommendations help in allocating resources efficiently, ensuring that the most dangerous vulnerabilities are addressed first.
Wrapping Up on Automated Pentesting
The power of automated pentesting is in transforming raw, scattered data on network vulnerabilities into an intuitive guide that provides actionable insights with substantial impact to risk reduction. The contextualization of the data, alongside powerful features like attack path visualizations, make automated pentesting a huge step forward in the cybersecurity space.
Combining automated penetration testing with other cybersecurity mechanisms that protect your network is the best way to establish a proactive and constantly evolving strategy.
Get updates on the latest technologies, news stories, and industry best practices by subscribing to the DOT Security blog today.
