Identity And Access Management
5 Common Cybersecurity Mistakes | DOT Security at Impact Optimize
September 09, 2022
5 Minutes

Penetration testers at DOT Security have many tales of how easy it was to hack into company networks by exploiting common cybersecurity mistakes employees make. The pen testers found these vulnerabilities when assessing how cyber secure various organizations were.
They shared some of their experiences at Impact Optimize, a business technology summit that DOT Security proudly sponsored the summer of 2022.
Sign up for our newsletter!
During their engagements, the penetration testers found easy ways to enter a network that should not have existed. They looked for the easy wins first to then strengthen the networks layers from the bottom up.
Here are some of the most common cybersecurity mistakes DOT Security pen testers found when they analyzed how protected businesses truly are.
1. Leaving Default Configurations on Your Endpoints
Most devices are set up with a manufacturer's default configurations. These configurations can often lead to compromise since they are well documented on the Internet. Bad actors can easily find them with a simple Google search. Often, it is one of the things they look for first.
For instance, one of the default configurations our penetration testers found often in business networks is the Link-Local Multicast Name Resolution (LLMNR). In windows and other operating systems, this configuration allows a server to pretend to be what a user is looking for.
In simpler terms, if used by a malicious actor, this configuration would allow them to pose as a trusted server, and it will send a user’s credentials to it. Thus, it can be used to harvest access credentials to be used or sold later.
Check with your IT department or cybersecurity expert to ensure such settings are disabled.
"These configurations can often lead to compromise since they are well documented on the Internet."
2. Not Changing Devices' Default Passwords
The next common cybersecurity mistake our penetration testers discussed was leaving default passwords on company devices.
They have found multiple devices with default passwords, such as printers, security cameras, switches, network-attached storage (NAS) devices, etc.
Printers, for example, are often left with default passwords such as "admin." Our penetration testers noted that some of these printers use the default password to grant domain rights.
Bad actors can not just use printers to print random documents, they can also use them to steal sensitive data.
Hackers can connect your printer to a botnet, which can be used to steal your data and carry out ransomware attacks, through which they request ransom money to decrypt and return exfiltrated data.
Related Blog: What Do Cybersecurity Analysts Do?
3. Using Weak Passwords
Weak passwords are an easily avoidable error that can lead to not only a user account getting hacked, but to a whole company network getting breached.
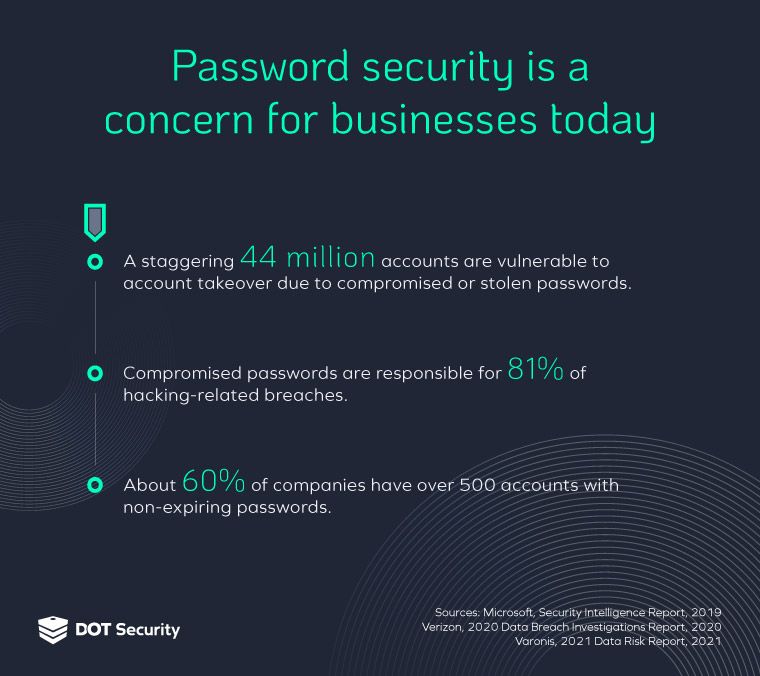
Too many employees used easily guessable passwords, DOT penetration testers observed. Passwords with names of the seasons, recent presidents' names, the company's name, and keyboard patterns such as QWERTY were some of the most common ones.
Password reuse was another common failure by employees. Malicious actors can use passwords from another site that has been hacked and expand their influence across user accounts.
Brute force attacks—where attackers use automation to to try different combinations of keys to guess passwords—are very common.
To avoid this, company leaders should encourage password hygiene among users. Using longer passwords or passphrases, changing passwords often, and not reusing passwords for different sites are great ways to keep a company secure.
4. Sharing Personal Information on Social Media
82% of business breaches involved the human element, according to the DBIR (Data Breach Investigations Report by Verizon).
Which means bad actors are taking advantage of simple employee mistakes to hack businesses. One tactic that uses these errors is spear phishing, in which a customized email is sent to targeted individuals. The email is personalized to appear as if someone who knows the recipient wrote it.
Our penetration testers fooled company employees, for example by writing an email from a pretend dealership with the same car model and make as the recipient. How did they get this information? In one of the recipient's social media page.
Train your employees to be aware of what should and shouldn't be shared online to others, especially if their Facebook, Instagram, Twitter, and others are visible to the general public.
Malicious actors run many types of social engineering campaigns on social media to get personal information from users. For example, seemingly innocent prompts such as "Your futuristic name is your middle name plus your car's brand," or "Let's see who gave their first pet their cutest name," are designed to get information that can allow someone to break into your account.
Hackers can also use this information you share to create elaborate phishing campaigns.
Related Blog: Cyber Kill Chain: A Guide to Advanced Targeted Attacks
5. Lacking Phishing Awareness
If the employees where DOT Security penetration testers had been aware of common phishing red flags, they would have been less likely to click on the fabricated email campaign mentioned above. Fortunately, that specific campaign was run only to test their cybersecurity habits.
Sony studios, however, was actually breached by bad actors who used phishing and spear phishing email campaigns to get access into the media giant's network. Small business leaders should also be aware, since bad actors often target small to medium-sized businesses.
To avoid clicking on links or downloading any documents from a phishing email campaign, double check who is the sender. Although the name may match, ensure the domain name is what you expected. Hovering over any links to confirm where they lead to can also help you avoid clicking malicious links.
Employees should be aware of these types of tricks hackers use. If not sure, they should be supported by a well-staffed IT department or a cybersecurity provider.
Related Blog: 5 Identity and Access Management Best Practices
In Conclusion
DOT Security penetration testers spoke about the most common cybersecurity mistakes they see users make when they assess a company's network.
Human error, which is the biggest cause of network breaches, led to easily avoidable vulnerabilities such as default settings left unchanged, using easily-cracked passwords, sharing personal information on social media, and not having phishing awareness.
Training your employees, or using a cybersecurity partner who can help you develop and deploy a cybersecurity program for your business can minimize the security gaps that bad actors use to breach networks.
Securing your organization can close vulnerabilities that could allow malicious actors to breach into your network. Ensure your company network is secure by reviewing our Cybersecurity Checklist: How Covered is Your Business?
