Cybersecurity Consulting
7 Challenges in Cybersecurity for Business
September 22, 2022
5 Minutes

The challenges in cybersecurity for business grow in complexity on a regular basis. Bad actors continue to develop malware and conduct phishing campaigns, employees lack the right training, and compliance laws can be confusing.
However, with the right program that takes into account your business needs, resources, and respective industry, cybersecurity can be a tool at your disposal rather than a problem to be solved.
Sign up for our newsletter!
We'll discuss some of the current challenges in cybersecurity for business and deliver some insight that can help organizations stay secure.
Biggest Challenges in Cybersecurity for Businesses
1. Lack of Employee Awareness
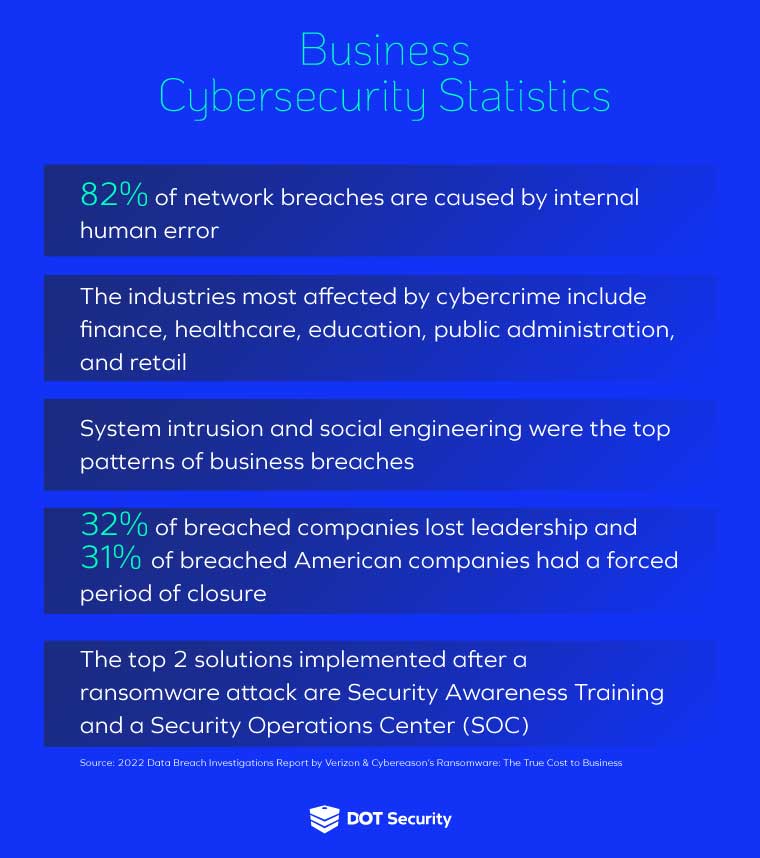
Human error causes the overwhelming majority of network breaches in companies. With 82% of breaches involving the human element, it is imperative for all businesses to train their employees and increase their cybersecurity literacy.
Employee lack of cyber awareness can lead to workers clicking phishing emails, using weak passwords, sharing personal information on social media, and giving out company information to unconfirmed sources.
To minimize the risk of human error in your organization, consider developing a cybersecurity training program that uses real scenarios your employees might encounter, active exercises that will help them retain their knowledge, and regular updates so their cyber literacy is up to date.
Communicate to your employees the benefits of keeping your organization secure. Ensuring everyone in the company understands the need to protect personal and customer data, to adhere to compliance standards, and to ensure business continuity will help your employees champion cybersecurity.
2. Ever-Evolving Cyber Threats
Manufacturers continuously develop upgrades for devices and software, while companies increase their security as tools evolve. However, malicious actors also work to develop new strategies and to share their knowledge with each other.
In 2022 alone, ransomware saw a growth of 13%, which is a higher increase than the last five years combined.
Attacks against businesses increase because hackers realized that stealing and ransoming companies’ data is much more profitable than targeting single individuals who may not have the resources to pay to retrieve their stolen data.
It is a challenge for cybersecurity professionals to stay up to date with the ever-evolving cyber threat landscape, let alone for business leaders who are focused on serving their clients and running their organizations.
Following cybercrime news sites to learn about current trends can help. Partnering with a cybersecurity provider can give leaders even more peace of mind, since stakeholders can rely on experts while they focus on managing and growing their business.
3. No Disaster Recovery Plan
Although SMBs are at higher risk of being targeted by bad actors, having a disaster recovery plan in place can make the difference between bouncing back or being unable to recover.
For instance, out of 1,263 surveyed businesses, 66% suffered significant revenue loss as a result of a ransomware attack. Additionally, more than half of organizations in the United States suffered from a damaged brand and 31% reported a forced business closure.

These numbers may sound alarming. However, most businesses are able to recover after a ransomware attack if they had a detailed disaster recovery plan in place.
Consider consulting with a cybersecurity professional or provider to begin your disaster recovery strategy.
4. Wide Skill Gap
The current talent shortage creates many of the challenges in cybersecurity for business. Companies who want to invest in an in-house cybersecurity team will struggle finding professionals to fulfill all their security needs.
Like many industries facing talent shortages currently, the number of unfilled cybersecurity jobs grew by 350% from 2013 to 2021. It is expected to continue growing at a similar rate.
If your organization is determined to fund an in-house cybersecurity team, consider hiring new and young talent. New professionals enter the market every year, especially as demand increases. Company leaders are often not keen on hiring new talent due to expectations of experience and skill. However, mentors within the company can train new employees to fill up the skill gap faster.
Otherwise, outsourcing talent from a cybersecurity provider will take care of all your cybersecurity and compliance needs. This removes the need to create, fund, and maintain an in-house department.
Related Blog: How to Stay Updated on Cybersecurity
5. Poor Cloud Management
Companies that invest in cloud solutions for their organization might struggle with the phenomenon known as cloud sprawl, if their cloud systems are not properly managed.
In essence, cloud sprawl happens when an organization has numerous cloud solutions, but they are all mismanaged, disjointed, and run inefficiently.
This would be akin to keeping sports equipment in different storage rooms, but none of it is strategically or thematically organized. People would spend too much time trying to find the resources they need. They might buy new equipment to not waste time finding it. If something went missing, it would be hard to track down at which point it disappeared.
The same applies when more cloud systems get added without proper management. When data is unorganized and proliferating in different cloud solutions, it is harder for a team to track down which user has access to what data. More internal errors can happen that can lead to data breaches or proprietary data loss.
Cloud solutions are a great tool for businesses. But they also need the proper management to leverage all the benefits and opportunities that they present. Consider appointing your IT staff to maintain your cloud solutions or consulting with a cybersecurity expert to establish the best cloud structure for your business.
6. Remote or Hybrid Workplace Threats
Most businesses saw a complete change in the way employees perform work in the last few years. Some organizations have remote work policies while others have established hybrid programs.
36.2 million workers or 22% of Americans will be working remotely by the year 2025.
Your business and employees can safely maintain their remote or hybrid workspace by making cybersecurity a priority. Both organizational leaders and employees should undergo cybersecurity training to understand the goals of keeping your company's data safe.
Consider also creating a device inventory, asking your staff to use MFA (multiple-factor authentication) when using company accounts, and requiring everyone in the organization to reset their passwords regularly.
Another solution for companies with remote workers is remote monitoring and management (RMM). RMM is a solution that leverages different technologies to monitor multiple networks and can be tailored for your specific needs.
Related Blog: 7 Ways to Build a Security Policy for Remote Workers
7. Lack of Compliance
Data compliance requirements can be a disorienting topic for business leaders, especially since compliance laws are continuously being created or updated.
Businesses that fail to follow their respective compliance requirements can face large fees or litigation. Healthcare companies failing to adhere to HIPAA compliance standards, for example, can incur fines of $100 to $50,000 per violation. Fees can add up per record and business reputation can suffer.
Consider seeking advice from an attorney familiar with your industry or with a cybersecurity consultant so that your organization has a complete compliance program and keeps its unblemished reputation.
Related Blog: What are the Consequences of a HIPAA Violation?
Bottom Line
The cyber landscape is often changing, which can make it difficult for business leaders to establish a thorough cybersecurity program in their organizations. With growing threats, changing compliance laws, and the widening skill gap, businesses have a substantial challenge keeping their data and devices safe.
Cybersecurity doesn't have to be another stressor for business leaders. With the right program that is customized for your specific needs, uses the tools you need without unnecessary additions, and follows the required compliance, executives can focus on leading their business, free of worry.
Speaking with your current IT department leaders or consulting with a cybersecurity professional can be the first step in developing a thorough security program for your business. When your security bases are covered, your organization can easily continue serving its customers and growing.
Continue your cybersecurity journey by checking if your business has the basic strategies to safeguard its data and devices. Download our Cybersecurity Checklist: How Covered is Your Business? to learn more.
