Cybersecurity Consulting
Red Team vs Blue Team: How to Test Your Cybersecurity Posture
August 30, 2022
8 Minutes
Red team vs blue team is a common exercise in cybersecurity designed to test a business’ defenses against cybercriminals, but what’s really the difference between the two teams? And how does this exercise help business secure themselves against modern cyberthreats?
Learn more below about both the red team and the blue team and how their battles can help you improve your business’ cybersecurity posture.
Sign up for our newsletter!
Red Team vs. Blue Team in Cybersecurity
Both the red team and the blue team work in penetration testing, meaning they work to test cybersecurity defenses by attempting to overcome security controls and working to secure them.
The difference between the red team vs the blue team lies in which side they take during a penetration test. The red team acts as the offensive side, attempting to beat security controls and penetrate a system. The blue team acts as the defensive side, working to protect businesses from attackers using their organizational knowledge, understanding of critical assets, and expertise in security controls.
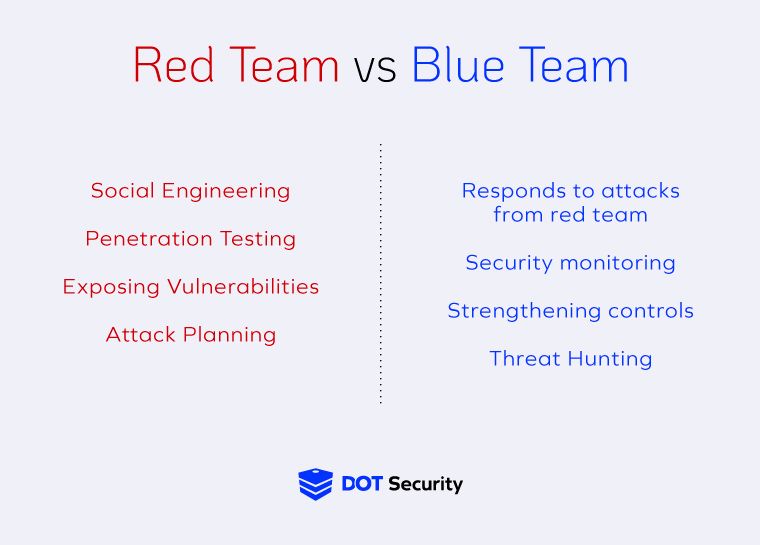
What is a Red Team in Cybersecurity?
In cybersecurity, the red team’s job is to test the effectiveness of established cybersecurity controls. A red team consists of ethical hackers who use the same tactics as a cybercriminal to attempt to penetrate a network, identifying weaknesses along the way.
These simulated attacks help businesses and cybersecurity experts to identify critical assets, build a strategy around them, and to test whether or not they’re working as intended. Afterward, the red team uses its combined expertise to make recommendations to businesses on how to strengthen their overall cybersecurity posture.
The weaknesses the red team is seeking to expose can be related to hardware, software, protocols, processes, and even people. There are many things that can be exposed as weaknesses by hackers and it’s the red team’s job to make sure all avenues are accounted for to keep businesses secure.

How Does a Red Team Test a Business’ Cybersecurity?
Contrary to Hollywood and popular belief, the red team isn’t frantically clacking their keyboards and analyzing lines of vertical code. In reality, most of their work is done beforehand doing research into a business’ defenses, planning attacks, deploying social engineering tactics, and attempting to poke and prod to find ways to get in.
This is because this is how a cybercriminal’s mind works. They plan, perform reconnaissance, do their research, and become accustomed to your security system before launching major attacks.
They’re typically looking to obtain key information that can help them decide how they’ll go about their attacks, including:
- A business’ operating system
- Identifying network hardware (servers, firewalls, routers, etc.)
- Learning physical security controls
All this information comes together to help them develop and build a network map to help them understand how it works, where traffic goes, what software is used to filter that traffic, and more. In turn, helps to identify vulnerabilities and choose a target for an attack.
Once these vulnerabilities are identified, a red team acts and tries to actively exploit them to gain access to a business’ network. Once inside, the red team member will attempt to escalate the attack, steal information, and see how far they can go. This helps to test cybersecurity systems designed for identifying attacks as they occur and reacting appropriately.

What is a Blue Team in Cybersecurity?
On the flip side of the coin, the blue team is a team of cybersecurity experts that works to secure an organization and protect its critical assets. This is done by getting an understanding of that business inside and out to understand where vulnerabilities may lie and what security protocols, software, and other tools might be necessary to secure them.
This team strengthens a business’ security posture by building a strong strategy by implementing new technology (firewalls, software, etc.), instituting security awareness education and training, monitoring a network, and introducing security protocols organization-wide.
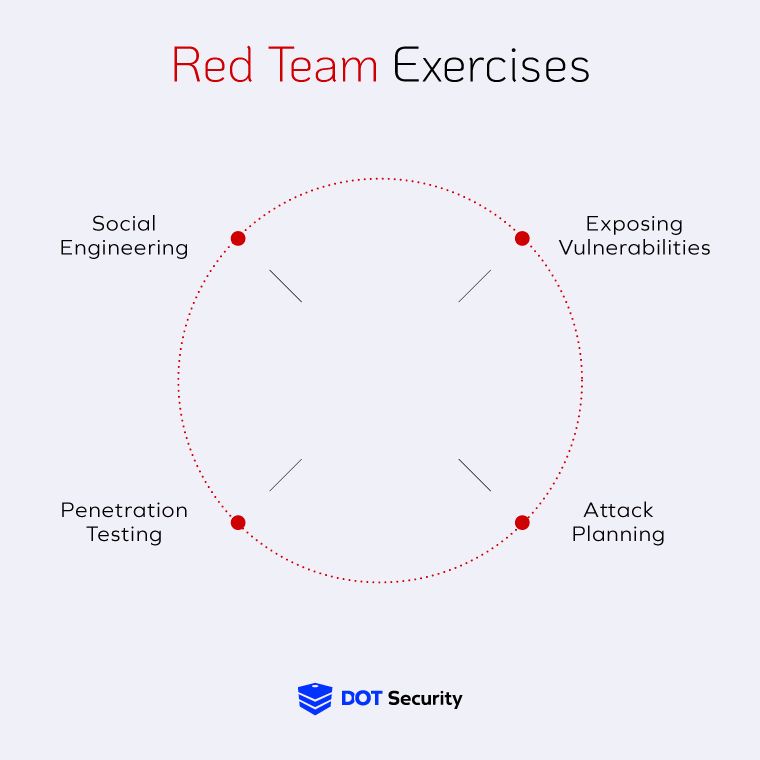
How Does a Blue Team Improve a Business’ Cybersecurity Posture?
The blue team’s job is to get a business ready for an attack by building a strong organizational cybersecurity posture. This helps them avoid attacks through proactive measures like firewalls, filters, and security awareness training, as well as recoveryand identification tools to quickly spot attacks and recover from them when they do occur.
This is done in a variety of ways because cybersecurity is such a complicated beast. That’s why it all begins with a risk assessment to help the security team understand where your critical assets lie, what your biggest vulnerabilities might be, and how to secure everything with the cybersecurity tools available. This can be anything from introducing stronger password management policies to consistent awareness training to installing new antivirus software.
How Red and Blue Teams Work Together
This is the most important part of the entire exercise. After the blue team has set up defenses and the red team has tried to topple them, the two teams come together to share notes, collaborate, and prepare recommendations as to how a business’ cybersecurity systems can be improved.
Additionally, over time, each team can help the other stay sharp by being aware of new vulnerabilities, new types of cyberattacks, the latest security technology, and everything else that can help businesses stay secure from evolving threats.
All of this information, combined with the results of the simulated attack, gives a cybersecurity team the insights it needs to improve upon established defenses.
Why Businesses Need Red and Blue Teams
Without a red team and blue team, you never truly know if your cybersecurity posture is good enough. Will it withstand certain attacks? Are there gaps in your defenses that cybercriminals can easily exploit? Are there aspects of security you haven’t even considered?
You don’t want to find out about your biggest cybersecurity weakness because a cybercriminal took advantage of it to penetrate your network, steal information, and cripple your systems. With the help of a team of penetration testers like the red and blue teams, you can test your defenses, discover your weak spots, and fix them before bad actors do.
How Do Business Get Red and Blue Teams?
Businesses without dedicated cybersecurity teams most likely don’t have access to full-fledged teams of penetration testers and cybersecurity consultants. Meaning these simulated attacks aren’t taking place and you’re left wondering if your defenses are enough.
The easiest way to obtain this expertise is through a partnership with a managed security services provider (MSSP) like DOT Security. At DOT Security, we have teams filled with experts that can help you build a strong security posture and prepare you for anything that the cyber world can throw at you.
Learn more about what it’s like working with a provider like DOT Security and how we can help you shore up your defenses with the help of our red and blue teams.
