Secure Data Protection
The Need for Cloud Security in the Aerospace & Defense Industry
May 25, 2022
6 minutes

With more reliance on cloud computing than ever before, organizations in the aerospace and defense industry must realize the importance of having cloud security to protect themselves from threats that pop up when using the cloud.
Learn more about the necessity for cloud security below and see some real-world examples of how it’s being implemented today by aerospace businesses.
Sign up for our newsletter!
The Many Uses of Cloud Technology in Aerospace and Defense
Cloud computing has become a mainstay in the aerospace and defense industry and is being used by contractors, subcontractors, manufacturers, and the government itself. The industry has begun to lean heavily on this cloud technology to do many business-critical tasks, such as:
- Collecting, transferring, storing, and organizing data from mobile devices, remote workers, multiple locations, IoT devices, aircraft in flight, and more
- Eliminating data silos and opening access to information organization-wide
- Automating maintenance and repair workflows to keep flights and equipment running smoothly
- Utilizing virtual applications in day-to-day operations
- Connecting devices (mobile phones, tablets, laptops, IoT devices, etc.)
- Managing supply chain operations
Cloud technology has its hands in many pies within an aerospace and defense organization’s daily operations, but relying so heavily on it for so many things can create natural vulnerabilities that could leave organizations with brutal downtime or stolen data that can jeopardize operations across the board.
Outlining the Need for Cloud Security
With so many important things relying on it—and so much data moving through it—securing cloud operations has become of paramount importance, especially when handling sensitive information.
Because of the amount of valuable data being processed by aerospace companies, cyberattacks are on the rise, and the need for security is rising with it.
To avoid downtime, maintain smooth operations, and stay secure, aerospace and defense organizations are investing in cloud platforms that provide high-level security that adds an additional layer of protection for their data.
Examples of Cloud Security in Aerospace and Defense
Here are a few examples of areas where cloud security can help aerospace organizations protect their most important operating data:
Protecting Flight Data
A lot of useful data is collected from aircraft flights that are used in a variety of ways from tracking flights midair, and measuring the performance of parts, to communications between the crew and the ground. This information needs to be secured to protect trade secrets from getting into competitors’ hands or bad actors to obtain important flight information.
To protect it, businesses need cloud security tools to protect the sensors and devices that send data, as well as the servers that collect and organize it. This is done by securing traffic moving in both directions using firewalls to filter traffic and by limiting who can use access points where data can be obtained. This includes training staff members on how to avoid phishing attacks with the goal of stealing login credentials.
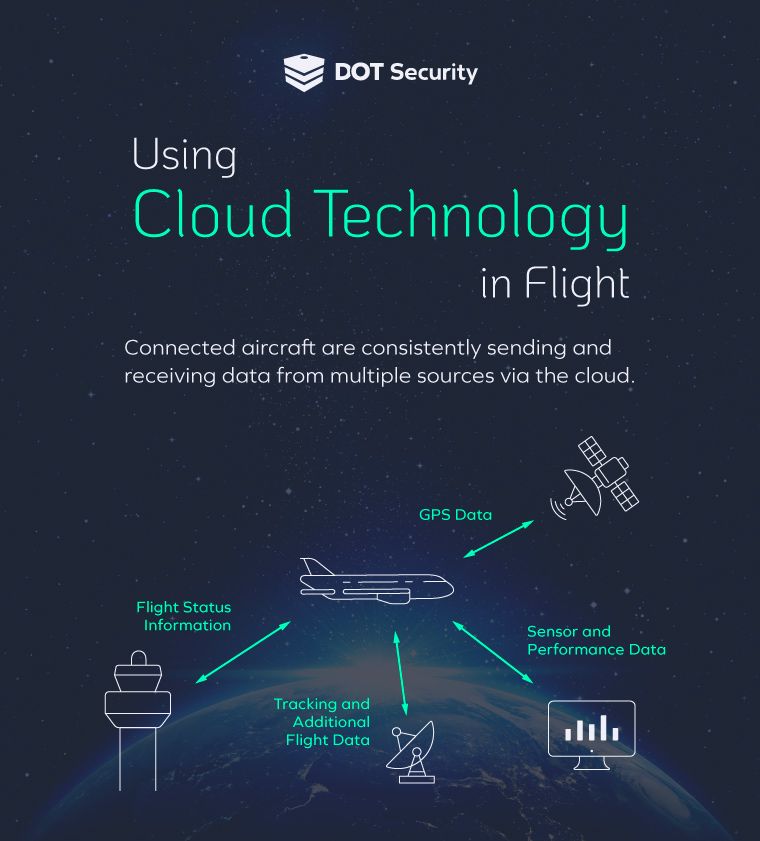
An additional layer of security utilized by cloud services is data backup which can help businesses get back up and running quickly without losing valuable data that might have been leaked or lost.
Securing Remote Devices
One side effect of using cloud technology is that it sometimes requires the use of many devices to collect data from so many different sources, especially when monitoring part performance of different parts of a plane, for example.
Part of cloud security is ensuring these devices can’t be abused and used to steal information or access the network.
Security for Sensitive Information
As mentioned above involving flight information, a lot of sensitive info can be passed along via the cloud, especially when working with the Department of Defense which requires a certain level of security when handling their data.
Having the cloud security tools in place to protect this data as its transferred, stored, and accessed helps protect it and ensure that data leaks don’t damage a business’ reputation and inhibit its ability to obtain more contracts and jobs in the future.
Many cloud providers offer secure cloud configurations for government and defense work. All of these cloud configurations meet or exceed the requirements mandated by FedRAMP (Federal Risk and Authorization Management Program). Controlled access, proper levels of encryption, provider employee background checks, and data jurisdiction among other security controls are used by these authorized cloud service providers.
In Conclusion
The importance of cloud security in aerospace and defense cannot be understated. Protect your critical flight data, trade secrets, communications, and sensitive information by implementing the proper cloud security protocols.
Cloud security is a critical part of a layered cybersecurity approach. But it’s not the only part. Use this new checklist to explore what it takes for businesses to be completely covered when it comes to cybersecurity and see how covered your business is now and how covered it can be in the future with the help of security experts. Download the checklist now.
