Network Security Monitoring
Infographic: Cybersecurity Attack Vectors: What to Watch Out For!
October 15, 2021
6 minutes

The infographic in this blog post will demonstrate to you the key information security attack vectors that cause breaches in organizations today.
Some of these may be surprises and some terms you may never have heard of before—but all vectors are a danger to the modern business.
Signup for our newsletter!!
We’ll be going through all the terms used in the infographic and explaining what each of them mean and what it means for businesses in general when it comes to ensuring their companies are properly secured.
Take a look!
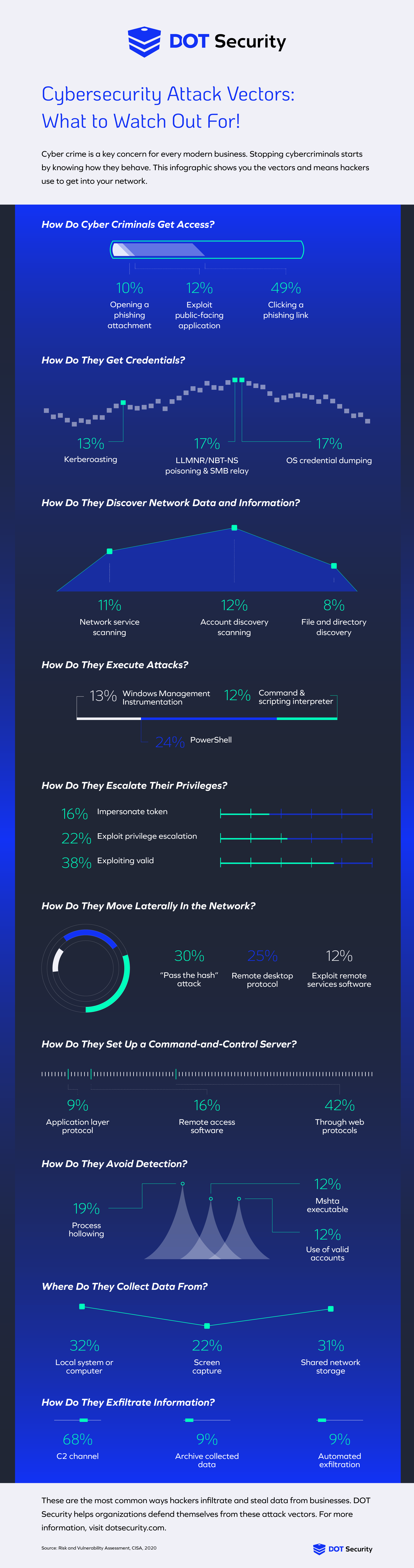
Concerns About Information Security Attack Vectors
For several years, now, cyberattacks on organizations, particularly small and midsized businesses (SMBs), have been on the rise.
This has been largely due to a few factors that have led cybercriminals to determine SMBs to be key targets.
Firstly, businesses today hold more data and information (about customers and the business itself) than they ever have before.
75% of SMBs operating in US critical infrastructure have experienced at least one breach in their history.
For a hacker, data means opportunity, and so, the more data available to compromise, the most attractive a company is in the eyes of a criminal.
Secondly, information security attack vectors have grown in their scope and there is today a broad array of ways into an organization’s network.
The rise of Internet of Things technology has provided companies with more flexibility and efficiency than they’ve had previously, but has simultaneously opened up a far wider range of potential avenues of attack for malicious actors.
Thirdly, and perhaps most importantly, is the fact that many businesses have failed to catch up with the radical change that is being brought about by the technological revolution.
Cybersecurity insurers saw a 336% rise in claims from 2019 through 2020.
In other words, many businesses are investing heavily in new technologies, but many are also neglecting to implement cybersecurity precautions to keep them from harm, whether because they don’t realize they are a potential victim or don’t believe they will be attacked (often because they think they’re too small to be attacked).
Neither is true.
The reality of business cybersecurity today is that the environment is more dangerous than ever, and organizations must adopt the right expertise and solutions in order to avoid being on the wrong end of a data breach.
Information Security Attack Vectors and COVID
We should also make note that the onset of the COVID pandemic has led to a sharp increase in the volume and severity of attacks on SMBs.
This is because of several reasons but primarily was as a result of workplaces turning to remote work en masse and without the adequate protections necessary to enforce a quality security program on employees working from outside typical office networks.
This has given hackers a prime opportunity to target work-from-home employees who are not being afforded security by their companies, and with remote work here to stay, this will remain something businesses will have to consider long into the future.
If businesses are uncertain about where they stand with regard to their cybersecurity practices, policies, and solutions, it’s a good idea to have a managed security service provider conduct a cybersecurity risk assessment to determine what they need to do next to shore up their security capabilities.
Get in touch with the DOT Security team and kickstart your cybersecurity strategy.
Breaking Down the Terms
Now, let’s get into breaking down the terms in the infographic!
The following will list out all the cybersecurity-related phrases and explain them to give more context to the infographic.
How Do Cybercriminals Get Access?
Phishing
Phishing refers to a type of cyberattack that relies on social engineering. Hackers will send emails to the intended target that are designed to trick them into thinking it’s a real message from a legitimate source. The aim of phishing is typically to get the user to click and follow a link or download an attachment from the email.
Exploit
An “exploit” is when a hacker has identified a flaw in a piece of software unknown to developers that can be taken advantage of. Exploits are used to do things like gaining unauthorized access to the back-end of a system.
How Do They Get Credentials?
Kerberoasting
Kerberoasting is one of the most common ways hackers get their hands on passwords. They target Active Directory (AD) services, which most companies rely on for their user management, and use brute-force attacks to get a Kerberos hash and translate it to a clear-text password. This password can then be used to login to AD and create a new user profile, which they will then use to access the system and roam free in the network.
LLMNR/NBT-NS poisoning
These terms refer to Microsoft Windows components that are used to identify a host. LLMNR is based on the Domain Name System (DNS) format, while NBT-NS identifies users by their NetBIOS name.
In short, these methods are used for machines to communicate with one another. When the DNS server doesn’t respond to a network request by a machine (for example, looking for a printer), it will “ask” other machines on the network; at which point a bad actor can take advantage by offering their machine up as the desired endpoint. The victim’s credential hash is then sent to the attacker, who can then break the hash and gain access.
OS credential dumping
In an effort to reduce the need for users to type in passwords too often, operating systems store them in their memory. If attackers have even low-level system access, they can use an executable to get a credential “dump” from the system memory, which can then be decrypted into a clear-text password.
How Do They Execute Attacks?
Windows Management Instrumentation
WMI attacks use this application, designed to provide a standardized environment for local and remote access, to interact with network machines for discovery purposes and moving laterally within a system.
PowerShell
PowerShell is a scripting tool that can offer a substantial level of access to a machine’s inner workings, like Windows APIs. PowerShell can also be run remotely by users. Attackers use PowerShell to bypass firewalls and run PowerShell scripts that allow them administrative control over endpoints.
How Do They Discover Network Data and Information?
Network service scanning
This refers to the use of port scanning or probing to identify services used on a network and which ports on it are filtered, open, or closed.
Accounts Discovery scanning
Accounts Discovery can be used to identify users and their access privileges, helping malicious actors determine their prime targets.
File and directory discovery
This is used by hackers to identify certain information they’re looking for within a system and can be additionally used to discover whether they have fully infected a target machine.
How Do They Escalate Their Privileges?
Impersonate token
Hackers can make and impersonate tokens (which allow users access to directories) to escalate their account privileges and navigate past typical access controls.
Exploit privilege escalation
Privilege escalation exploits refer to when hackers take advantage of an application or operating system vulnerability to give themselves increased access to network resources that would otherwise not allow access.
Exploiting valid accounts
Hackers can target and exploit valid accounts, such as those belonging to a user with advanced access privileges, and use this to navigate a network with relative ease.
How Do They Move Laterally In the Network?
“Pass the hash” attack
Pass the hash attacks allow hackers to have lateral movement within a network. It works by taking advantage of the NTLM authentication protocol, which relies on password hashes rather than a clear-text password. If the hacker gains access to the hash, there’s no need for them to decrypt it, they can simply use the hash to authenticate.
Remote desktop protocol
Hackers can gain access to networks by accessing unsecured endpoint ports on user computers and then using remote access to deliver malware to the main network. This has become especially common with remote workers.
What Is a Command-and-control Server?
A command-and-control server is a server from which an attacker will send commands to an infected machine within a network. These can live and be sent through the application layer protocol, via remote access software, or through web protocols.
How Do They Avoid Detection?
Process hollowing
The is a process whereby hackers will hide their malware within a legitimate process so it is not discovered.
Mshta executable
The Mshta executable is a Windows-native binary that is used to execute HTML files, including VBScript and Jscript. Because Mshta is a legitimate Windows executable, malware can be pushed with it while not leaving much of a malicious footprint.
Use of valid accounts
Using valid accounts that won’t be flagged by the network means hackers can move around the system while appearing as a totally legitimate user.
How Do They Exfiltrate Information?
C2 channel
The C2 channel connects to the attacker’s command-and-control server, allowing them to feed information from infected machines back to them.
Archive collected data
Cybercriminals will often encrypt and compress data before retrieving it so as to hide what they’re doing and minimize their footprint.
Automated exfiltration
After collecting data, bad actors can use automated programs to retrieve the data and transfer sensitive network information to their command-and-control server.
