Cybersecurity Consulting
Infographic: A Quick Guide to Risk Management In Cybersecurity
January 29, 2022
4 minutes

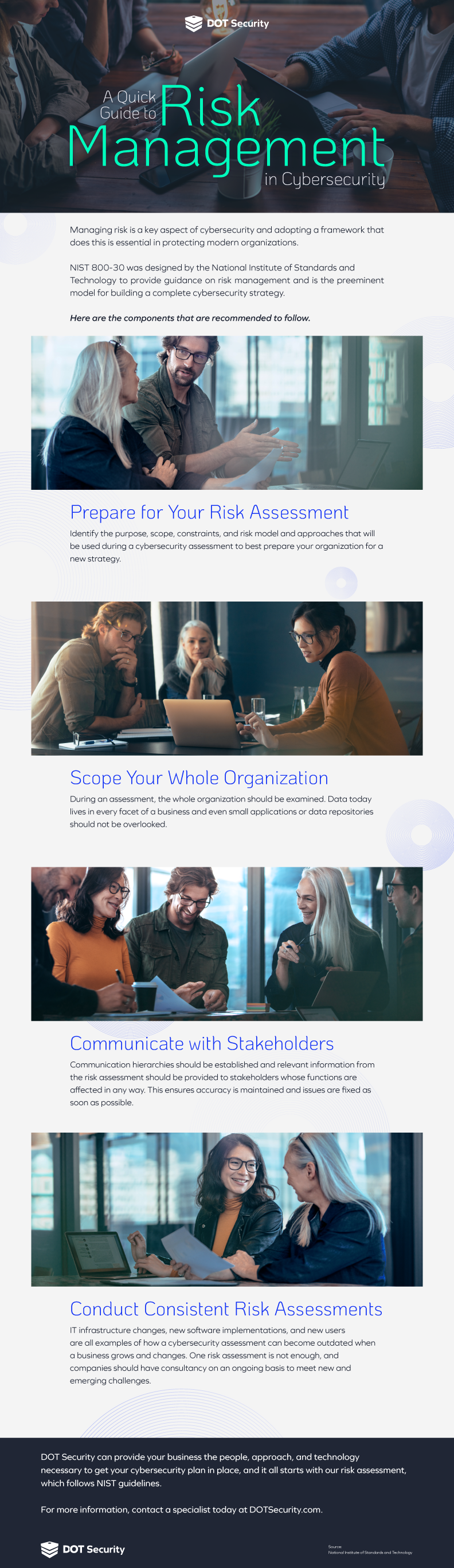
Risk management is a core aspect of cybersecurity in a modern organization and it’s crucial that decision-makers take the necessary steps to ensure threats posed to their business networks are kept to a minimum.
This infographic breaks down the key factors involved in NIST 800-30, which was created to offer advice to SMBs on how to avoid being the victim of a cyberattack.
Sign up for our newsletter!
Take a look!
What’s Involved In a Cybersecurity Risk Assessment?
Step 1: Planning
The planning stage of an IT security risk assessment is crucial in identifying a business’ obligations, expectations, and key personnel responsible for ensuring the project goes smoothly.
This means putting in place a process that clearly defines the project and how communication will be dealt with. At this stage, designating key stakeholders and liaisons is needed in order to move forward.
Auditors will need to be provided with scoping information for business networks, in addition to third-party systems held under the network. These requirements will be communicated by the auditing team.
They will then draw up a project plan which will include a schedule for the audit.
Step 2: Execution
Now we get into the meat of it.
The execution phase is where the risk audit team will begin conducting testing and scanning in order to build a picture of the security status of the company.
This is typically broken up into two distinct areas: vulnerability scanning and penetration testing, in addition to the optional gap analysis which can also be performed.
Vulnerability Scanning
Vulnerability scanning is the first port of call in establishing what a business’ weaknesses and strengths are.
When cyberattackers target businesses, their attack vectors virtually always follow the path of least resistance.
In other words, if your internal or external network has weaknesses that are picked up during vulnerability scanning, they’re likely to be the primary offenders in the event of an attack.
During the risk audit, your internal network will be scanned to see if there are any issues with your system that might aid a hacker attempting to move laterally through your network once they’ve gained access.
In this process, the scan will map out your network and determine what exactly the soft underbelly of the business is and potential avenues of attack.
Penetration Testing
The risk audit team will now put into action penetration testing, which seeks to ethically and safely gain entry to your network by exploiting vulnerabilities.
This will be conducted by a white hat hacker, a security professional who will play the role of a hacker attempting to break into the business network to get a further understanding of where the biggest weaknesses are.
Penetration testing is always conducted safely, so organizations don’t have to worry about any of their data becoming inadvertently compromised.
Once the testing is complete, the white hat professional will report back with their findings.
This is an invaluable part of IT security management and risk assessment and gives businesses an insight into how hackers behave and the methods they use specific to their business when attempting to breach the company’s data.
Gap Analysis (optional)
A gap analysis isn’t strictly speaking a step of the risk audit process, but for many businesses today this aspect is vital.
Organizations that operate in highly regulated industries, like healthcare, education, and finance, have to abide by existing and new rules regarding data security.
A gap analysis will assess a business’ compliance standards, their policies as regards data handling and safeguarding, and the extent to which these policies are being enforced.
When a business has a gap analysis performed, it’s a lot easier for them to have a clear picture of where they stand with their compliance and exactly what they need to do if they’re lacking the correct policies.
While a gap analysis is most useful for organizations operating in industries with strict data governance rules, it’s important to note that universal standards are being increasingly sought-after and adopted at the state and federal levels.
In California, for example, CCPA is in effect for everyone, while New York has its SHIELD Act, which went into effect in March 2020.
Businesses are identifying that data security and compliance are heading in the direction of stricter regulation and preparing themselves early.
We also saw this when GDPR came into being, with US-based companies adopting its compliance rules to set themselves up for US laws that are starting to come into place today.
Final Step: Analysis and Reporting
Finally, we have the final stage of the cybersecurity risk assessment.
The risk audit will report on each stage of the audit—the business’ needs, vulnerabilities, weaknesses from a white hat perspective, and compliance policies.
Findings, technical observations, immediate remediation for pressing issues, and long-term recommendations will be made that can ensure the business is secured.
Once these next steps have been presented and discussed, the business can then adopt a security program that addresses any issues that have been discovered.
Are you in need of cybersecurity services but don’t know where to start? Consider having a risk assessment done by DOT Security. Get in touch to get started today!
