Edge Security
How to Maintain Security When Employees Work Remotely
March 21, 2023
8 minutes

Research suggests that the more remote employees a company has, the higher the average cost of a data breach is. This emphasizes the need to understand how to maintain security when employees work remotely.
With the rise in remote work, how can businesses juggle new devices, unsecured network connections, and remote access to critical data while staying secure?
Sign up for our newsletter!
If you'd first like to read about what it takes to implement a plan to secure a remote workforce, check out 7 Ways to Build a Security Policy for Remote Workers.
Why Remote Work Poses New Cybersecurity Challenges
Though it has many advantages like increasing productivity and improving workers' mental health, remote work has posed a unique challenge for businesses when it comes to cybersecurity.
All forms of cyberattacks increased as remote work became more common for a few reasons:
- Cybercriminals wanted to take advantage of people’s uncertainty amid the pandemic.
- Businesses and people were not equipped with the tools or knowledge needed to counter them.
- While demand for cybersecurity professionals increased, the talent gap in this sector has not been filled.

When the pandemic began, meetings were virtual, company data was being accessed in multiple places, employees were using their own devices at home or on the go using unsecured Wi-Fi networks, and cybercriminals quickly recognized the opportunity afoot and began using innovative new threats designed to take advantage of these new vulnerabilities.
Yet organizations need a few tips on how to maintain security when employees work remotely:
Tips for Maintaining Security for Remote Workers
While cybercriminals continue to develop ways to infiltrate networks, cybersecurity experts are also adept at developing new security practices to help secure a remote workforces.
Here are some tips to help your business’ remote workers stay secure:
1. Ensure Strong Passwords, Password Management, and Multi-Factor Authentication
One of the easiest yet most effective ways to protect your organization is to enforce MFA (multi-factor authentication). MFA is a multi-step user verification method that ensures users are who they say they are. MFA examples include authenticator apps or fingerprint scanning on devices.
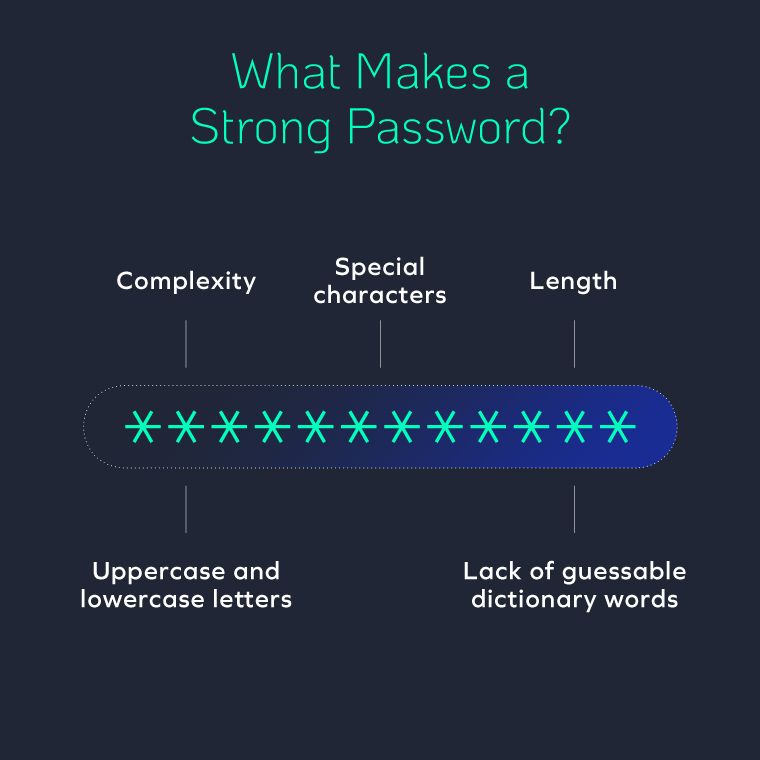
Passwords are another line of defense that protects against wrongful access that can occur if a password is lost, guessed, or stolen. Businesses need to implement strong password policies that include:
Password management includes secure tools that allow employees to store their passwords in one place and share them safely with colleagues.
Password standards are a set of policies employees should use when making passwords that define how often they should be changed, their length, and the complexity required. Oftentimes, password management tools come with a password generator that can create long and complex passwords that are instantly stored for future use.
2. Employee Cybersecurity Training
A core tenet of a strong cybersecurity culture is awareness training. This is something that most businesses do, to an extent, but remote work requires a new form of knowledge that may not be being taught in the course and trainings that businesses are requiring now.
44% of businesses said they did not provide training to their staff on the threats of working remotely. How can someone be prepared to identify and stop threats if they don’t know what they’re looking for?
3. Device Security and Access Management
Unless provided with a business-owned alternative, remote employees will be relying on their own devices to work, access data, send information, log in to business networks, and communicate with internal and external teams and partners.
So, it’s important for businesses to implement a device management plan that can track company devices and other devices that are used to access a network. This way you always know who is accessing data and with what device.
A big part of this is utilizing access management policies like the principle of least privilege to manage and track who has access to what information, ensuring that only people who need data have the ability to get to it.
4. Edge Security
With remote workers and a lot of additional devices connecting to your network, it’s important to keep your network secure. That’s where edge security comes in.
Equipping your business with modern edge security solutions like firewalls, antivirus software, internal systems protection, and integrated unified threat management (UTM) keeps your network protected no matter where someone attempts to access it from or the type of device the use.
5. VPNs
A VPN (virtual private network) creates a secure, encrypted connection between remote devices and an organization’s network. This can help protect businesses from dangers that arise when remote workers use unsecured Wi-Fi networksor poorly configured network equipment.
The easiest way to implement this in your business is to supply your teams with laptops or desktops with pre-configured VPN software. If done this way, VPNs will show up as network options from the moment the device is configured. VPNs can also be used in a browser-based fashion which makes it easier to use from different devices but you must rely on people remembering every time.
6. Use Encryption When Sending Data
Sending and receiving data can be dangerous, especially when you have people working remotely, on different networks, using their own devices. To keep data secure as it’s being stored and shared, businesses can use encryption.
Related Blog: What You Need to Know About Key Management in Network Security
Encryption is a way to translate common language into an unreadable code and only people with access keys can translate the information back. This means if data is stolen, it’s unusable which protects business information, trade secrets, and personal information from customers and employees.
7. Have a Response Plan in Place
When disaster strikes, it’s important that businesses have a plan to recover their data and get critical business systems back up and running as soon as possible. Successful breaches can cause data loss, reputational harm, and costly downtime.
A disaster response plan ensures everyone knows what to do when an event occurs, replacing chaos with an organized response can limit the damage. Without a plan, data breaches cost businesses an average of $4.24 million and $1.07 million more when related to remote work, according to a study by IBM.
Related: What Steps Make Up a Data Backup Disaster Recovery Plan?
These kinds of plans are made up of a few steps, including determining critical infrastructure, setting recovery timelines, assigning responsibilities, and determining appropriate backup periods.
In Conclusion
Remote work has thrown a new wrinkle into business cybersecurity, but businesses have the power to stay protected against modern remote threats if they take the time to implement the necessary best practices and tools.
To answer the question, how to maintain security when employees work remotely? Businesses should build a response plan, use encryption tools and VPNs, implement password management, and stay on top of access controls.
Though it can be complex, it’s worth it to mitigate the threats of a security breach and avoid downtime, data loss, and the other negatives associated with cyberattacks on businesses.
Now that you know what you need for remote work cybersecurity, it's time to build a policy that implements it. Check out DOT Security's blog, 7 Ways to Build a Security Policy for Remote Workers, to learn how.
