Identity And Access Management
What Is Multi-Factor Authentication and What Are Some Examples?
September 26, 2024
8 minute read

Multi-factor authentication (MFA) is a security process that helps organizations improve their identity and access management strategies. More specifically, MFA is a tool that creates an additional layer of protection around credentials, forcing users to prove that they really are who they say they are, even if they already know an account's username and password.
There are a few different forms of multi-factor authentication technology and each takes a unique approach to user authentication.
Sign up for our newsletter!
MFA kind of acts like an invite-only exclusive party. Even if you show up with a valid ID, if you can’t present the formal invitation, you won’t be allowed inside. This is the basic premise behind multi-factor authentication as it creates a series of validation checkpoints that all have to be met to proceed.
The following sections dive further into multi-factor authentication, exploring the various tactics different MFA technologies employ and the security benefits organizations reap from implementing MFA as a part of their password management policy.
Social engineering scams are one of the most common ways in which employee credentials become compromised. Learn how you and your staff can avoid phishing attacks in DOT Security’s infographic, 6 Things to Look Out for to Avoid Phishing Scams.
What Is Multi-Factor Authentication?
MFA is a security method that requires a user to verify their identity through two or more methods when logging into an account. By creating additional verification layers, MFA technology helps prevent unauthorized user access to company systems even if employee credentials are compromised.
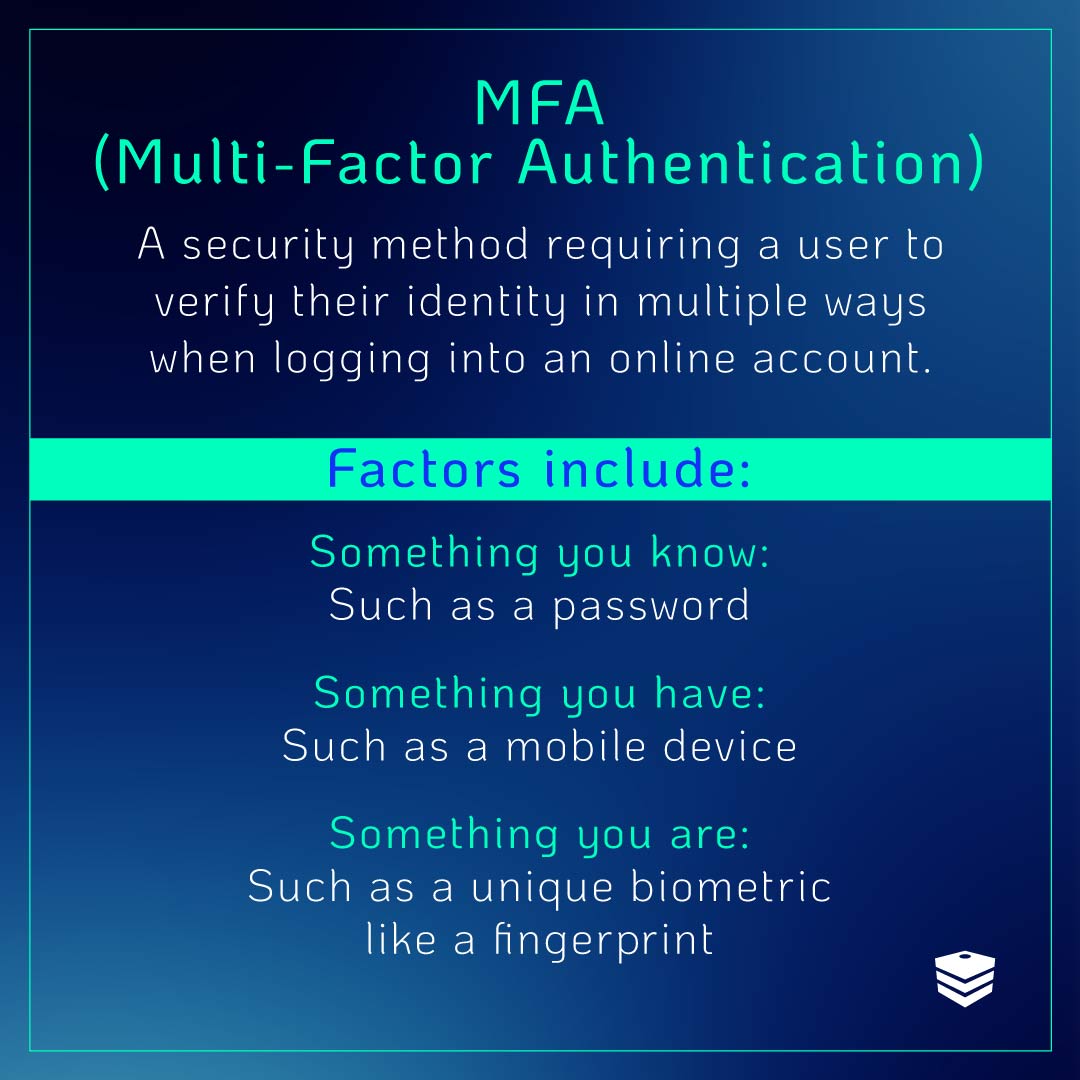
The various secondary authentication methods that popular MFAs use include:
- Something you know: Such as a one-time password or PIN
- Something you have: Such as a smartphone, physical badge, or USB key
- Something you are: Such as your fingerprint, your voice, or another unique biometric
Because MFA technology forces users to go through a second identity verification process, a malicious actor using compromised user credentials will still be locked out of the network if they can’t provide the additional verification needed.
For example, after inserting the credentials, the bad actor would still need to input a security code, connect an encrypted USB key, or scan a fingerprint. In failing to provide the required information, they would be locked out of the compromised account, and the breach would be halted.
It’s worth noting that with advances in technology, text message or SMS-based MFA authentication has become much less secure than other forms like biometrics or physical encrypted USB keys.
How to Implement MFA, With Examples
Let’s take a look at how organizations implement multi-factor authentication successfully based on the three verification methods listed above.
Something You Know
One of the most common forms of multi-factor authentication is referred to as ”something you know.” This is often a one-time password or PIN that’s sent to your personal device via text message or authenticator app.
This is important to note because according to Patrick Layton, Executive Director of the Board at DOT Security, authentication details delivered via text are much less secure than if delivered through an encrypted multi-factor authentication app.
Here are some of the ways MFA works with a something-you-know approach:
-
A One-Time PIN: A personal identification number (PIN) is a popular authentication tactic. Just like you use a pre-determined PIN at the ATM to make a withdrawal, one MFA tactic is to deliver the user a unique one-time PIN through their personal device.
-
A One-Time Password: Similar to sending you a unique PIN, some MFA services will deliver fully loaded one-time passwords to further authenticate users.
-
The Answer to a Security Question: Some accounts allow users to set up security questions for authentication as well. Commonly used questions include your mother's maiden name or the elementary school you attended. While this can add a layer of protection to your accounts, they are best used in concert with other MFA tactics as hackers can often find personal information.
If you’re going to rely on ”something you know” MFA tactics, make sure you’re using an MFA application rather than a text delivery system.
Something You Have
While something you know refers to knowledge-based authentication tactics, something you have requires that you physically possess the authenticator.
A few examples of something you have include:
-
A Security Badge: In the same way that most office buildings give out access cards so that staff can get into the building and operate the elevator, an MFA that makes use of a security badge will ask that you scan your badge after entering your username and password. This is a strong authentication tactic because it makes it impossible to virtually break into accounts.
-
An Encrypted USB Key: An encrypted USB key is an MFA tool that also requires physical possession of the USB drive. After entering credentials, users with an encrypted USB key will need to connect the key to their computer, which will then unlock the appropriate accounts. Once again, because this is a physical key, this type of MFA tactic is very hard to breach virtually.
While physical security badges and encrypted USB keys do offer users advanced security, this isn’t the easiest of the MFA tactics to implement company-wide. This is because employees would be responsible for keeping track of the physical piece, which could be lost or stolen.
However, physical MFA solutions are a great option for employees with high levels of security clearance.
Something You Are
Finally, something you are in MFA refers to the use of unique biometric information to authenticate user identities. Common examples include:
-
Fingerprints: Since every person has a unique fingerprint pattern, this is a strong method of authentication typically used in smart devices like smartphones and modern laptops. It’s extremely difficult to recreate someone’s fingerprint pattern perfectly, and it therefore offers a strong layer of security to your authentication processes.
-
Facial Recognition Software: Another popular biometric for devices is facial recognition. Some users opt out of facial recognition authentication due to personal privacy concerns, but it remains a legitimate option for authentication tactics.
-
Retina Scans: Getting into more advanced security protocols and MFA tactics, retina scans are yet another form of biometric authentication that is arguably one of the most secure options. Retina scanners are typically used in military bases, at nuclear reactors, and in other high-security scenarios.
While there are privacy concerns around using biometric markers as authentication tactics, they remain one of the most secure ways that users can protect their accounts.
Why Use Multi-Factor Authentication?
Implementing MFA technology as a part of your password management policy will secure your network, protect employees, and keep malicious actors out of your systems.
Here are a few key security advantages that stem from implementing an MFA policy within your organization.
1. Secured Accounts
More than 99% of cyberattacks attempting to hijack accounts can be prevented with the use of MFA, according to Microsoft. Indeed, by adding a single additional layer of verification, you've made it that much harder for malicious actors to access protected accounts even with compromised credentials.
As mentioned earlier, even if a threat actor gets their hand on employee credentials, if they aren’t able to provide the necessary information they’ll be locked out of the account and denied access.
2. Company, Staff, and Customer Data Protection
Laws and regulations created to protect consumers’ personal information, such as the California Consumer Privacy Act (CCPA) or Health Insurance Portability and Accountability Act (HIPAA), require organizations to implement MFA technology to safeguard that data.
CCPA, for instance, requires administrators and employees to take advantage of MFA as a security measure to prevent the theft of sensitive information.
Organizations that suffer a data breach will also have to show the corresponding authorities what measures, such as MFA or network segmentation, were in place to protect customer data.
3. Mobility and Scalability
Whether your workforce operates remotely or your company has grown and is onboarding new employees, MFA will ensure that company devices, accounts, and data are secure.
Although MFA takes more time than a single-factor authentication method, it greatly reduces the risk of accounts being breached and information stolen, regardless of where your employees are or how many of them you bring on board.
Employee cybersecurity training is also an important part of implementing MFA in your organization so that your staff understands why they need to go through with it and the role they play as individuals in company security.
The Role of MFA in a Comprehensive Cybersecurity Strategy
A comprehensive cybersecurity strategy requires additional measures beyond MFA. Strong password policies, regular software updates, and network security tools like firewalls and intrusion detection systems are essential for defending against various threats. These components work together to safeguard systems from external attacks and vulnerabilities.
In addition, regular security assessments and vulnerability scans are vital for identifying and addressing potential weaknesses before they can be exploited. Staying informed about the latest threats and continuously evaluating security measures helps organizations adapt to evolving risks and maintain a robust defense.
Encryption and incident response planning also play crucial roles. Encryption ensures that sensitive data remains protected, even if compromised, while a well-defined incident response plan helps organizations manage and recover from security breaches.
Combining MFA with these strategies ensures a well-rounded approach to cybersecurity.
Final Thoughts on Multi-Factor Authentication
Multi-factor authentication is a crucial element of identity and access management services, serving as a formidable defense against cyberattacks aiming to compromise accounts.
With three different approaches to MFA tactics, businesses can customize their authentication approach based on their goals and available resources. Additionally, the benefits of implementing a quality MFA will far outweigh the potential risks associated with under-protected accounts, such as data loss or compromised credentials.
However, to fully leverage the benefits of MFA technology, it is essential to educate and train employees on cybersecurity, ensuring a comprehensive understanding of their role in the overall security of the company.
Unfortunately, employees still represent the largest cyber risk for most organizations. Learn how to help your employees avoid social engineering scams like phishing emails in DOT Security’s infographic, 6 Things to Look Out for to Avoid Phishing Scams.
