Network Security Monitoring
How to Prevent Advanced Persistent Threats with Specialized Detection
March 12, 2024
7 minute read

Advanced Persistent Threats (APTs) are sophisticated and prolonged cyberattacks launched by highly skilled adversaries, often state-sponsored or organized crime groups, with the intent to stealthily breach a target's network, maintain long-term access, and siphon sensitive information without detection.
Cyberattacks have become extremely sophisticated, leaving many organizations wondering how to prevent things like advanced persistent threat attacks that can be difficult to detect and in turn, remediate.
Sign up for our newsletter!
They may dwell in a network for days or even months, using advanced, next-generation hacking techniques.
As such, specialized persistence detection uses a powerful combination of sophisticated defense technology and human expertise to combat hackers leveraging ATP attacks.
These hunters look for anomalies across the network, suspicious behavior, and unusual data patterns, then respond to neutralize threats and mitigate damage.
The following sections walk through the different steps of an advanced persistent threat attack and which tools you can use to prevent one.
Modern businesses need modern cybersecurity solutions to protect their network and the data that’s stored within. Find out how your cybersecurity posture measures up in DOT Security’s Cybersecurity Checklist: How Covered Is Your Business?
What is an Advanced Persistent Threat (APT)?
To reiterate, an advanced persistent threat attack is a long-term cyberattack in which a hacker or bad actor gains access to a network and continuously hides and siphons data while remaining undetected.
These intruders bypass traditional preventative measures such as anti-malware and firewalls. They dwell in a network for days or even months, using sophisticated hacking techniques to analyze the environment, move laterally, and look for the desired information.
Attackers often leave multiple back doors open, so that they can maintain access despite interruptions such as restarts or changed credentials. This is why these attacks are advanced and persistent.
Keep in mind that due to the nature of APTs, it is not possible to completely prevent all threats. Just like despite having a fire alarm, an escape program, and a local fire station, a fire can happen, the human element of APT attacks also makes them unpredictable.
Reasons Behind Advanced Persistent Threats (APT)
The main purpose of APT attacks is monetary gain.
APT attacks affect mainly larger organizations and businesses because targeting individuals often leads to wasted resources and no monetary gains for cybercriminals.
A more lucrative method is infiltrating and moving across a business network because the more information stolen and the greater the number of machines affected, the more likely bad actors are to receive payment.
Targeting intellectual property, regulated data, or customer personal data gives cybercriminals stronger methods to bargain for payment.
The Anatomy of Advanced Persistent Threats
There is a process for how criminals execute APT attacks. From intrusion to exploitation, the graph below summarizes the MITRE ATT&CK Framework to some of its most salient parts, beginning with Reconnaissance and ending with Impact.
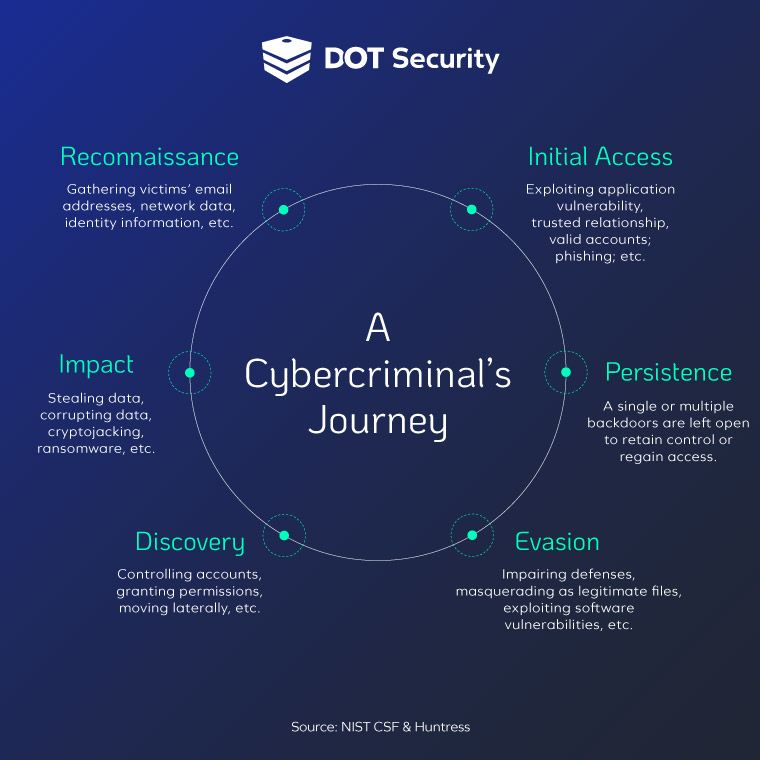
Read on below to see how specialized persistence detection acts during the Persistence stage to discover and neutralize attackers.
How to Prevent Advanced Persistent Threat Attacks
There are measures you can take to protect your business’s valuable data and prevent advanced persistent threats. At a foundational level, any organization should begin by implementing the National Institute of Standards and Technology (NIST) Cybersecurity Framework.
In short, the NIST cybersecurity network asks you to identify, protect, detect, respond, and recover your assets. Let’s take a look at each of these steps.
1. Identify
“The data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization’s risk strategy.” -NIST CSF
The identify stage is two-fold:
- You cannot protect the assets that you have not identified. Take stock of the important assets of your company, such as devices, data, accounts, applications, and vendors.
- Your organization will also need to identify risks, vulnerabilities, and any compliance standards they need to follow.
By doing both of these things, you can focus your resources on protecting what’s valuable and not waste them on safeguarding every single asset.
2. Protect
The function of protect is to set up defenses around the assets you have identified above. For this, you will need identity and access management, employee cybersecurity training, applying protective technologies, maintenance, and data security.
Some basic tools to achieve protection are firewalls, antivirus software, installing patches and upgrades, email security, and data encryption.
Consider also implementing security around your physical access, such as managing key access in your building and securing any physical devices to prevent hacking or theft.
3. Detect
“Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.” - NIST CSF
This step demands alertness to timely note and identify a cybersecurity event. A cybersecurity event is not necessarily an attack, but it refers to any event that may have an impact on an organization’s operations.
For example, noting failed login attempts, new account creation, new endpoints or software, etc. These events could alert you to an attempted cyberattack so that you can take the appropriate action.
4. Respond
“The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.” - NIST CSF
This step attempts to contain the damage from a cyberattack as much as possible. It involves response planning, communication, mitigation, and improvement.
Ensuring your security team members know their roles in resolving a cyberattack allows the response step to be done efficiently. Also if an incident happens, looking back and studying it can help your cybersecurity team respond more effectively in the future.
5. Recover
“Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.” - NIST CSF
Does your business have backups for important assets and data? These are paramount in case of data theft since the criminals would have less to leverage against you. Establish also a priority hierarchy for data, devices, and accounts in case recovery is necessary.
Ongoing backup tests and cybersecurity exercises to prepare your team for a cyberattack should also be performed.
Specialized Persistence Detection
As you can see, hackers use sophisticated, covert, and persistent techniques to breach into a network.
Traditional prevention software can identify and protect against known malware, however, when people are involved, the best response is, understandably, a team of human threat hunters.
Human threat hunters can detect anomalies that a computer might let through. To illustrate this, imagine hackers masking malware to look like an accepted file. To anti-malware software, the file would have the characteristics, size, and even content of a usual safe file.
However, when you add the human factor, people would be able to see the anomalies that would otherwise make it through into a network.
Of course, it is necessary to rely in prevention software, but once an intrusion has taken place, it is up to humans to offensively hunt and intercept any bad actors lurking in the background.
Specialized persistence detection uses a team of cybersecurity personnel who analyze and look for things out of the ordinary to detect an intrusion and alert users.
If a break in is detected, specialized persistence detection gives users an alert and report of the activity, also an easy-to-use “Remediation” and “Approve” buttons to quickly act to remediate threats before assets are exploited.
Wrapping Up on Advanced Persistent Threat Defense
Advanced persistent threat attacks are complex and long-term cyberattacks in which a hacker enters and lurks in a network to learn about its environment, establish a foothold, and execute criminal activity.
To prevent APT attacks, use the NIST cybersecurity framework and develop a program which takes into account your organization’s priorities and resources.
Software is very good at catching known threats, but when the human element is involved, the best answer is a team of human threat hunters who can offensively catch bad actors in a network.
While some business solutions are as easy as set-and-forget, cybersecurity is an ever-evolving industry that is constantly shifting. With that in mind, check out DOT Security’s Cybersecurity Checklist: How Covered is Your Business? To get an idea of how strong your cybersecurity posture is currently.
