Network Security Monitoring
What to Know About Ransomware Protection and Recovery
April 05, 2022
6 minutes

Contributed by David Konstant, Associate Cybersecurity Engineer, DOT Security
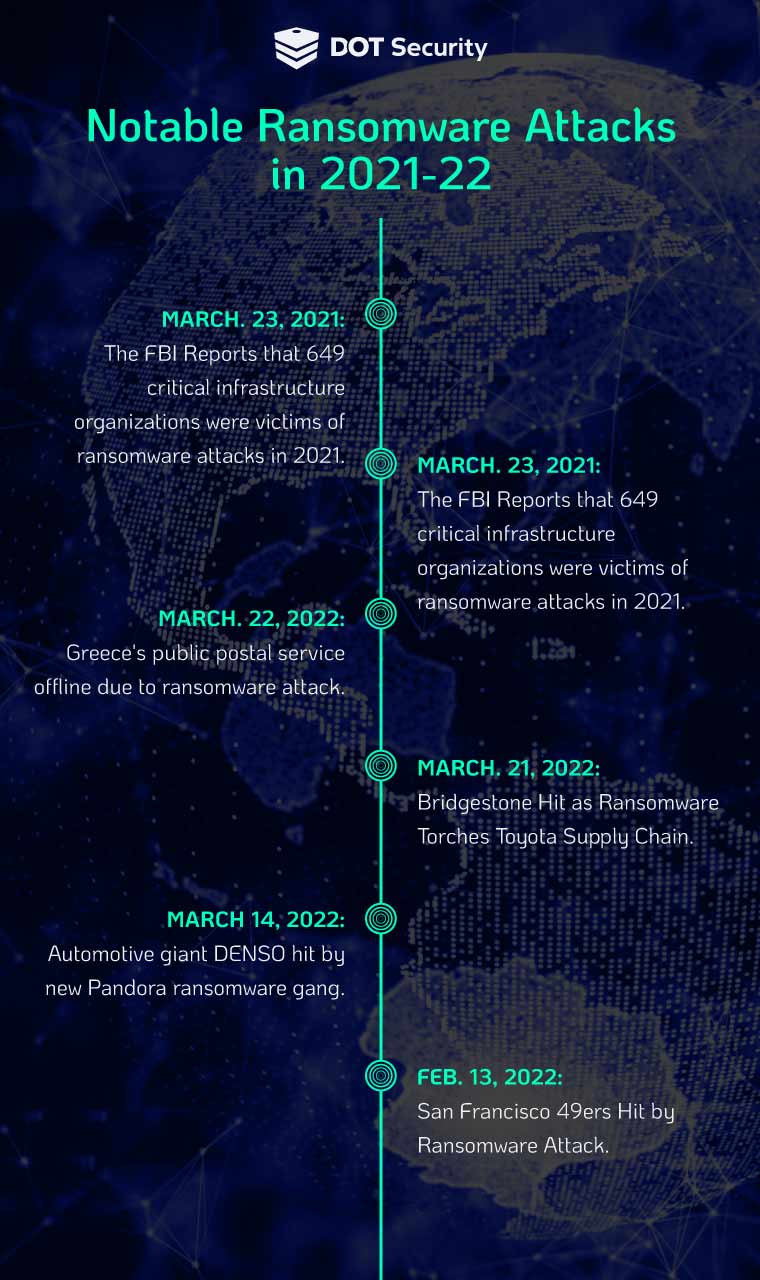
If you feel like you’ve been seeing a lot of news about ransomware lately, that’s because you have. Ransomware attacks are becoming increasingly common with organizations of all sizes being targeted.
As ransomware attacks continue to get more prevalent, it becomes increasingly important for organizations to be aware and prepared. This article will aim to update the reader on the troubling rise in ransomware attacks and discuss actionable steps to fight against this threat.
Sign up for our newsletter!
What is Ransomware?
Ransomware is malicious software that prevents users from accessing data or systems and demands a ransom payment to regain access. Organizations that fall victim to these attacks are put into a compromised position.
Recovering from a Ransomware Attack
The implications of encrypted data can vary from temporary inconvenience to a life-or-death situation for an ill-prepared hospital with locked patients’ electronic medical records.
Unfortunately, recent data suggest that less than half of the hostages that pay a ransom receive full access to their data.
15% of organizations affected by ransomware get reinfected after resolution.
Other research suggests the numbers to be even worse. The State of Ransomware Report 2022 by Sophos notes that hostages that pay the ransom:
- Organizations who pay a ransom get an average 61% of their data back
- 4% of organizations get full restoration of their information
- 11% of companies payed ransoms of $1 million or more
How Ransomware Attacks Affect Businesses
The financial consequence of ransomware attacks can be staggering. The State of Ransomware Report 2022 also finds that the cost of an attack increased about four times compared to 2020.
The average ransomware payment in 2021 was $812,360, but this is only part of the cost to remediate an attack. Additionally, it is reported that 86% of breached organizations lost business opportunities and revenue.
While these numbers include outliers that paid exorbitant ransoms, there is little doubt that the cost of a ransomware attack is rapidly growing and is unlikely to decrease as attackers continue their campaigns to increase sophistication and cash in on a massive payday.
Ransomware Protection: How Businesses Can Protect Themselves
Protection against ransomware attacks hinges on two ideas; preventing infection of data and systems and remediation.
The FBI’s Internet Crime Complain Center (IC3) notes that there are 3 main techniques used to infect victims with ransomware:
- Phishing campaigns
- Remote Desktop Protocol
- Software vulnerabilities
Protecting against phishing campaigns focuses on educating end-users on how to spot suspicious emails that may contain malicious links and attachments.
The people in an organization continue to be the biggest target of malicious actors, and the value of developing quality education and training cannot be overstated.
Related: The Importance of Cybersecurity Awareness, Training, and Education
Preventing Ransomware Attacks with Authorization Tools
It is helpful to expand the Remote Desktop Protocol (RDP) vector to any attack that involves unauthorized access via remote connection protocols including VPN connections, Citrix servers, or cloud-based file-sharing services like Google Drive or Microsoft’s OneDrive.
This includes using breached credentials or brute force attacks to remotely access an organization’s data and upload ransomware.
To protect against these attacks, organizations should focus on the authentication and authorization of users:
- Enforce the use of strong passwords
- Take advantage of multi-factor authentication for all connections and logins
- Use the most secure authentication procedures like client-side certificates for VPN connections
- Monitor periodic monitoring of public password database breaches on websites like dehahsed.com and haveibeenpwned.com
- Utilize geo-IP filtering to block communication to and from foreign-based connections
To protect against software vulnerabilities, organizations should take advantage of vulnerability management solutions that constantly monitor computers and servers for unpatched systems.
Organizations and agencies that rely on out-of-date software and operating systems need to take extra care and implement compensating controls like air-gapping vulnerable systems.
Ransomware Recovery
However, if your organization is victimized by a ransomware attack, timely remediation becomes the focus. Organizations and individuals can avoid many of the negative repercussions of a ransomware attack if they have proper backups in place. The following are some steps to take to make sure backups are available for remediation:
- Perform regular backups to stay up to date in the case of needing to perform restoration
- Maintain isolated, off-site backups to decrease the likelihood of infection by ransomware
- Create plans and test backup and recovery of data to ensure a streamlined process
- Take advantage of a monitored persistence/threat hunting solution
In Conclusion
Protecting yourself against ransomware attacks can be a daunting task with many considerations. It is important to determine the most likely attack vectors against the organization and implement protections and compensating controls.
Providing education and training to end-users remains one of the most important ways to protect your organization as they are the most common target.
Finally, having best-of-breed layered security tools being professionally implemented and monitored is a great way to remove the burden of staying safe. Learn more about the cybersecurity solutions that can help keep your business secure.
