Backup And Disaster Recovery
The Difference Between RPO and RTO in Cybersecurity
July 01, 2025
7 minute read

RPO and RTO play unique roles within backup and disaster recovery services, helping businesses measure the ideal amounts of time that they need to back up critical data and recover from incidents that cause outages.
RTO stands for recovery time objective and RPO stands for recovery point objective. Both are fundamental aspects of a proper disaster recovery plan, and we’ll go into more detail about what RPO and RTO actually mean below.
Sign up for our newsletter!
To learn more about how and where your organization can improve its cybersecurity, download and review DOT Security’s Cybersecurity Checklist: How Covered is Your Business?
Difference Between RPO and RTO
Recovery time objective (RTO) and recovery point objective (RPO) are two measurements of time within a company’s cybersecurity incident response. Both determine how prepared an organization is to identify, respond to, and recover from a security event. They also measure downtime and its impact on business operations.
Understanding the nuanced differences between RPO and RTO is integral to creating a disaster recovery plan that allows your organization to more quickly and smoothly recover from cyber incidents like a data loss or breach.
What Is RPO (Recovery Point Objective)?
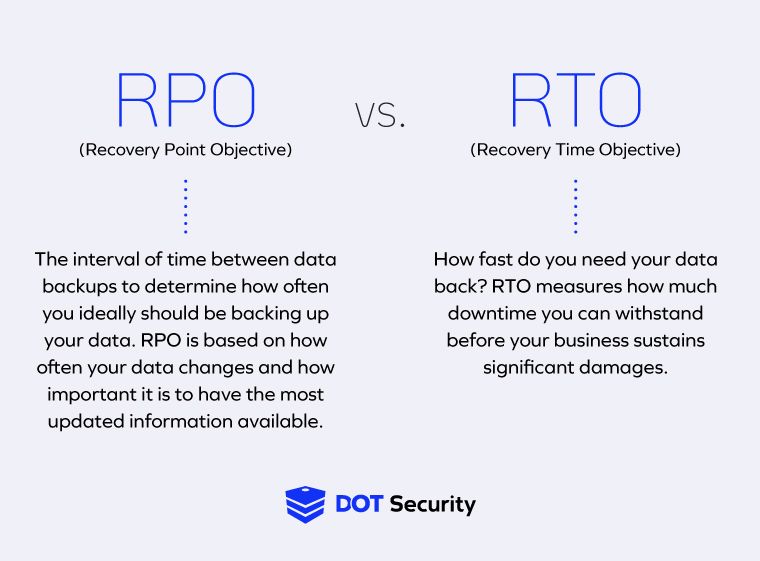
RPO is the amount of time that passes between a full data backup and the moment a system failure or data breach is recorded.
For example, if an organization with an RPO of 10 minutes experiences a breach 5 minutes after the last backup, 5 minutes of data will be lost, meaning they have an RPO of 5 minutes.
What Is the Meaning of RTO (Recovery Time Objective)?
RTO is the maximum amount of downtime an organization is able to withstand after a cyber incident occurs. Each business determines this for itself based on its needs. Downtime can cost thousands or millions of dollars, so it’s important to set a realistic RTO that gives your organization a chance to recover without suffering significant losses.
An RTO should be set based on the frequency of your backup schedule, the volume of data that needs to be backed up, the sensitivity of the data, and other factors that relate to the value of the data your organization collects, stores, and uses in daily operations.
Setting an RTO will help organizations gauge the severity of a data breach and should give them a good idea of how wide a window they have before damages from a breach become insurmountable.
The Difference Between RPO and RTO
Essentially, an RPO represents how frequently data gets backed up, and an RTO represents how long an organization has until it must recover after an incident. Ideally, your RPO is short and your RTO is long, meaning you backup data as often as possible and that you have some wiggle room to restore operations after an incident without suffering major losses.

What Are RPO and RTO in Cybersecurity?
In cybersecurity, RPO and RTO’s roles lie in recovering from and preparing for disaster. When attacking, cybercriminals will attempt to limit your access to important data either by stealing it outright or locking you out of your systems.
A disaster recovery plan (which contains your desired RPO and RTO) is how you limit that damage once you’ve quelled the threat. RTO and RPO are not cybersecurity controls themselves but are used to measure the efficacy of your security strategy.
RPO in Cybersecurity
The recovery point objective is the amount of time that can elapse before critical data must be recovered to resume normal operations. In terms of cybersecurity, RPO protects your team’s ability to resume business and mitigates the risks of losing the most important data that keeps your business running smoothly. It works by defining the necessary interval that data is backed up so that, when you lose access to data, there’s a backup dataset waiting.
It’s necessary to identify your business’ ideal recovery point objective as part of a cybersecurity system because it gives your recovery team the information it needs to build a strategy that fits your organization’s specific needs.
RTO in Cybersecurity
It’s a similar situation for RTO. The main role of your recovery time objective is determining the maximum amount of downtime a system can handle before disaster occurs. In cybersecurity, RTO gives your cybersecurity team an acceptable goal for speed of system and operational recovery.
Identifying your RTO is a necessary part of a cybersecurity strategy because it helps your security team ensure the critical aspects of your business technology are operational within a reasonable timeline.
RPO and RTO in Disaster Recovery
Within a disaster recovery strategy, RPO and RTO determine how long your organization will experience downtime after an incident and how much data could be lost. Part of establishing an effective recovery plan is determining the ideal RPO and RTO for your organization.
The average cost of downtime is $5,600 per minute, or $336,000 per hour. But, due to there being so many variables, downtime can cost some businesses up to $540,000 per hour.
How to Calculate an RPO or RTO
The “best” RPO or RTO depends on a few factors, like how critical the data is to business operations and how frequently that data must be updated. For industries where information moves quickly, like retail, where transactions happen frequently, you may need more backups. In slower industries, you might be able to afford slightly more time.
To dig deeper and learn more about what RPO or RTO would be ideal for your organization, ask questions like:
- How often does your data change?
- What are you losing with each minute of downtime?
- What does each minute of downtime cost in terms of money, productivity, services, etc.?
- Can business still operate with these systems down?
- How does downtime impact your customers?
Another variable to consider is your maximum tolerable period of disruption (MTPD), which is the amount of time your services can be down before it's unacceptable to your business. That can mean your employees can no longer do business or that your customers will become frustrated. Basically, how long can you go before business is affected to the point of losing clients?
How Often Should You Back Up Your Data?
Backups should be performed frequently and automatically, and stored in a way that protects them from being compromised along with the primary data. However, there’s no single backup frequency that is one size fits all.
If the data an organization handles is less critical to business operations, a longer RPO and RTO may be suitable.
When data collection is necessary and you must work with the most up-to-date information, it’s worth it to invest more in data security and backups. For businesses where real-time data is crucial—such as financial institutions, healthcare providers, and e-commerce platforms—short RPOs and long RTOs are vital.
These organizations should consider investing in advanced backup technologies, such as continuous data protection (CDP), which ensures that every change is saved almost instantly, and disaster recovery as a service (DRaaS), which provides robust, cloud-based recovery solutions to minimize downtime and data loss.
Additionally, modern backup solutions often integrate automation and monitoring to ensure that backups are performed correctly and data integrity is maintained.
How Is AI Influencing RPO and RTO in Recovery Plans?
AI is transforming recovery planning by shifting from reactive to proactive strategies. Instead of relying on fixed backup schedules, AI triggers backups based on system behavior, reducing RPO by aligning data capture with actual risk.
On the RTO side, AI accelerates recovery by identifying which systems to restore first based on business impact and usage patterns. Many organizations also use AI to simulate outages and continuously refine recovery playbooks, keeping RTO targets relevant as environments evolve.
AI strengthens early warning capabilities by detecting anomalies that signal potential failures or ransomware activity. With these insights, teams can launch containment or backup processes before damage spreads, minimizing both data loss and downtime.
In modern, automated environments, AI-driven orchestration tools launch failovers and recovery workflows without waiting on human input. This shift enables faster, smarter recovery that keeps pace with the demands of hybrid and cloud-native infrastructures.
Wrapping Up on RPO and RTO
RPO and RTO both help businesses measure and understand the risks associated with backup and recovery from cybersecurity incidents and answer key questions like: how much data can you afford to lose and how long can your business withstand downtime before incurring losses?
Understanding the role of RPO and RTO in cybersecurity and disaster recovery responses will help your organization establish data security standards that are aligned with the nature of your business and keep your operations running smoothly.
Learn more about all the cybersecurity systems, controls, and procedures your business needs to stay secure by downloading the DOT Security Cybersecurity Checklist: How Covered is Your Business?
