Cybersecurity Consulting
What Is SOC Compliance? SOC 1 vs. SOC 2 vs. SOC 3
November 15, 2023
9 minute read

When you watch a movie that has won an Academy Award, you know that the film will be good quality since it has the approval of a reputable, outside source. System and Organization Controls (SOC) Compliance provides the same assurance when working with a business. You can feel safe knowing that the company provides quality services as it has earned a certification—whether SOC 1, SOC 2, or SOC 3— from an unaffiliated source.
In this blog, you will learn how working with a SOC-certified organization, like DOT Security, benefits your business and what exactly SOC compliance is. And if you’ve been staying up to date on our blog posts, you’ll notice that this is a different SOC than DOT Security’s Security Operations Center.
Sign up for our newsletter!
Working with a SOC-certified company ensures that you will be getting the best quality services, verified by an outside source. If you’re interested in collaborating with a cybersecurity service provider, get started with DOT Security today.
What Is SOC Compliance?
SOC compliance is a certification intended for companies that provide services to other organizations. It involves a service organization performing a third-party audit, confirming that the company being audited has certain controls in place.
To achieve SOC certification, the service provider must pass a series of tests performed by a reputable source, proving that the organization can provide the desired services to its customers. SOC compliance is conducted by a third-party auditor to ensure that the certification has been fairly earned, as the auditor is independent of the supplier-customer relationship and free of any conflicts of interest.

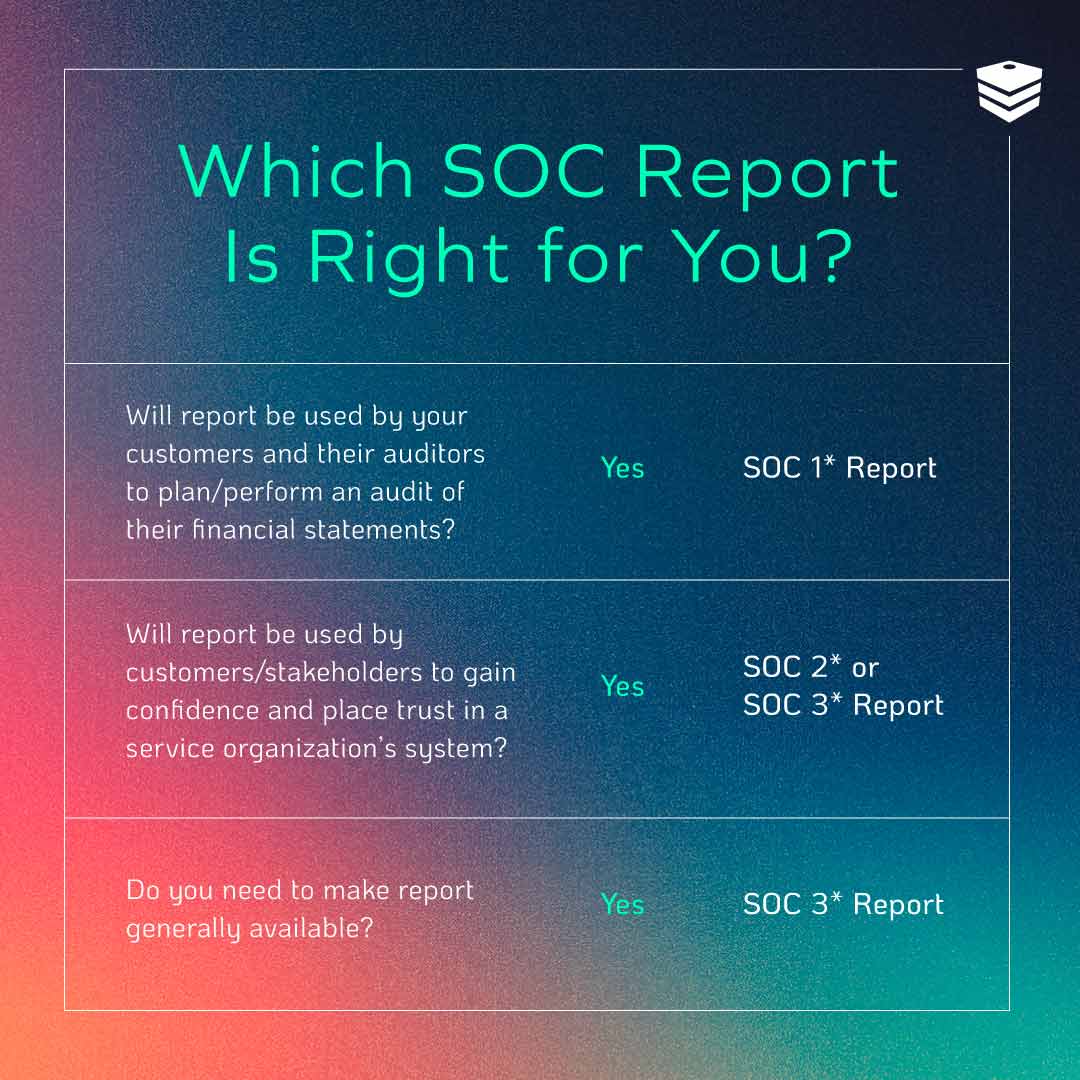
SOC compliance generally refers to three different reports:
- SOC 1
- SOC 2
- SOC 3
There can also be two types within any SOC report:
- Type 1
- Type 2
What Is SOC 1?
SOC 1 certification is required when the company’s services affect the customer’s financial reporting.
This report is designed to ensure that service organizations that control the financial reporting process for other companies meet the customers’ needs. For example, a company relying on a payroll provider for paysheet processing and management may want to see the provider’s SOC 1 reports as evidence of effectiveness.
Companies that should consider getting the SOC 1 audit:
- Collections organizations: Firms collecting debts on behalf of other organizations.
- Payment processors: Enterprises contracted to allocate the payroll for employees at other organizations.
- Software-as-a-Service MSPs: SaaS MSPs process financial statements.
- Benefits administrators: Administrators who manage and plan benefit programs, including health, dental, vision, 401(k), and retirement plans.
For a SOC 1 certification, the auditor must:
- Record control objectives: The auditor details the control objectives and the controls created to achieve the objectives.
- Perform testing procedures: The auditor performs the appropriate tests and records the results. The overall opinion of the auditor is recorded.
- Documentation of potential risk: Following the results from the testing, the auditor determines if there are any issues to address.
- Obtaining the report: The organization receives a SOC 1 report certification if all goes well.
What Is SOC 2?
While SOC 1 applies to companies that cover financial reporting, SOC 2 is more general and popular for companies that provide technology services to their customers. This report assesses the service provider’s controls for numerous Trust Services Criteria (TSCs), concentrating on security as a mandatory component.
The other TSCs the SOC 2 audit can cover are optional and include:
- Confidentiality
- Availability
- Processing integrity
- Privacy
A few of the TSCs overlap with the components of information security, which are practices that aim to protect sensitive data and information.
SOC 2 certification, which contains the auditor’s detailed opinion on a company’s internal controls’ design and operating effectiveness, is intended for an audience of client companies and their shareholders and can be reported to customers upon request.

The SOC 2 audit process can involve:
- Reviewing the audit scope: The auditor analyzes the audit scope, which is the amount of time and documents involved in an audit.
- Developing a project plan: The auditor determines how the process will be conducted for a particular organization.
- Testing controls for design or operating effectiveness: The organization’s internal controls are tested to ensure that they can meet the needs of the customers.
- Documenting results: Results are recorded by the auditor.
- Delivering the client report: As long as the organization meets the requirements, the auditor will issue a SOC 2 report to the company.
What Is SOC 3?
Similar to a SOC 2 certification, a SOC 3 report provides the same information but at a different level.
The biggest difference between the two certifications is that SOC 3 is intended for the general public, while SOC 2 is primarily for client companies and their shareholders. You may see SOC 3 certification on a company website to inform the public.
The SOC 3 report process may include:
- Preparation phase: During this phase, the auditor will request information about the company’s security policies, operations, and procedures.
- Evaluation of each area under review: The auditor will develop tests to examine aspects of the organization’s security measures, like system configuration and encryption practices.
- Initial meeting: A meeting between the auditor and the organization is held, where the auditor can ask additional questions.
- Performing tests: Tests can include interviews with personnel, reviewing security-related records and documents, analyzing system configurations, and observing where data is stored.
- Feedback: If the auditor finds any weaknesses after conducting the tests, they let the organization know. Then, the organization has the chance to correct those issues.
- Conclusion of tests and corrective actions: After the organization fixes any issues found, the auditor finishes up testing.
- Receiving the report: The auditor will issue a SOC 3 report outlining the findings and including any additional recommendations.
SOC Type 1 vs. Type 2
There are two types of SOC reports: Type 1 and Type 2.
To receive a Type 1 compliance certification, the auditor must provide a snapshot of the company’s status by testing one control to confirm that the company’s design and description are correct. This version of compliance certification is achieved quicker than Type 2.
Unlike Type 1, which focuses on a brief moment, a Type 2 certification tests the company’s compliance controls over a set period and looks at the organization’s ability to maintain compliance. As long as the company remains compliant over the evaluation period, a Type 2 compliance report is achieved.
How Companies Prepare for an Audit
Preparing for a SOC audit can put your organization in a better position for a successful evaluation. One company that has accomplished this is DOT Security, achieving a SOC 2 Type 1 certification!

Here are ways in which DOT Security prepared for their SOC 2 audit:
- Updated administrative policies and standard operating procedures: Since SOC 2 and 3 focus on security controls, having up-to-date security policies are critical. Policies should likely outline the standard processes for topics such as system access, disaster recovery, incident response, security roles and training, and risk assessment and analysis. Policies, which should be reviewed on a periodic basis and updated as procedures change, can be shared with the auditor as proof of your security program and will help your team answer security questions quickly during the audit.
- Ensured technical security controls are in place: Security controls should be implemented to match your company’s policies. Policies may cover access control, encryption, backup, audit logging, firewall and networking, and vulnerability scanning.
- Collected evidence: Gather relevant documentation prior to the audit to make the process easier for everyone involved. Documentation may include previous risk assessment and audit documentation, cloud and infrastructure related agreements, administrative security policies, third party and vendor contracts, and technical security control documentation.
Signing Off on SOC 1 vs SOC 2 vs SOC 3 and Type 1 vs Type 2
There are three different SOC reports with two types for each report. SOC 1 hones in on financial reporting, while SOC 2—intended for client companies—and SOC 3— used for the general public—primarily test for security, among other criteria. Type 1 and Type 2 mainly differ by the timeline of which the report is conducted by the auditor.
Now that you know the importance of compliance certifications, you can see why they are important to look out for when seeking out a service provider! If you’re interested in hiring one for cybersecurity needs, check out DOT Security today.
