Secure Data Protection
What Are the 3 Elements of Information Security?
October 10, 2024
7 minute read

Information security (InfoSec) is a set of practices that safeguard sensitive information, data centers, and cloud applications. Information security protocols block the unauthorized access, use, disclosure, disruption, or deletion of data.
There are three elements of information security, otherwise known as the CIA triad. They guide organizations on protecting important data through those three pillars of data security:
Sign up for our newsletter!!
- Confidentiality
- Integrity
- Availability
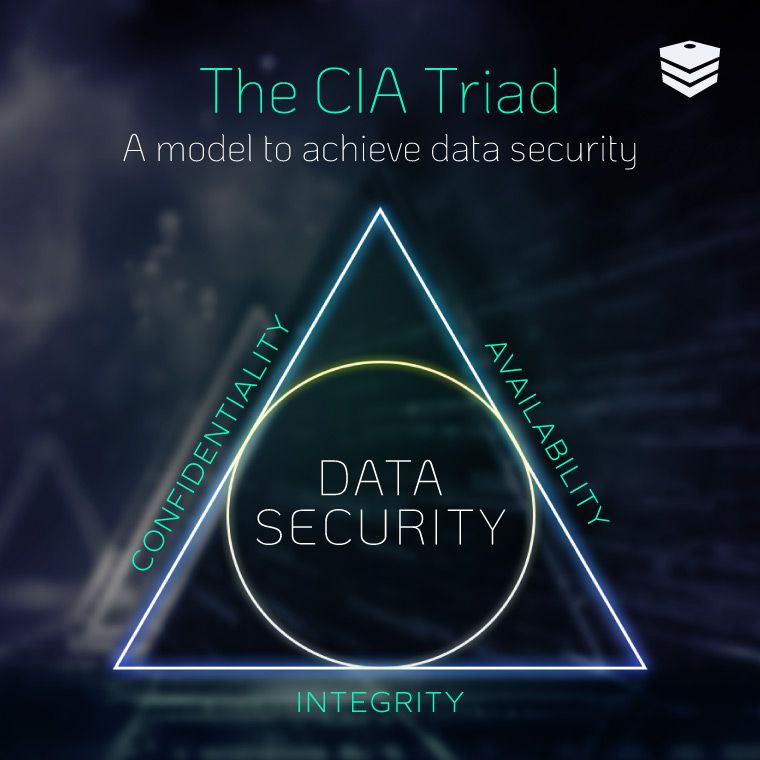
By focusing on keeping data confidential, and maintaining both its integrity and availability, you can rest assured that your organization is using high-quality data and that everyone who needs to access it, can.
To get an idea of how your current cybersecurity posture measures up to industry standards, check out DOT Security’s Cybersecurity Checklist: How Covered is Your Business?
The Three Components of the CIA Triad
At the core of robust information security lies the CIA triad—a foundational framework comprising confidentiality, integrity, and availability. These three pillars form the bedrock of your organization's defense, weaving together to create a tapestry of protection.
-
Confidentiality stands as the guardian of secrets, ensuring that sensitive information remains accessible only to those authorized to view it. It acts as the silent sentinel, shielding proprietary data, personal records, and classified materials from prying eyes.
-
Integrity serves as the steadfast protector of data accuracy and trustworthiness. It upholds the sanctity of information, safeguarding it from unauthorized alteration, corruption, or tampering. By maintaining the integrity of data, organizations can rely on their information, fostering trust and ensuring sound decision-making.
-
Availability acts as the resilient backbone, ensuring that information remains accessible to authorized users. It guards against disruptions, downtime, and denial-of-service attacks. By preserving availability, organizations can remain operational even in the face of an attack or other disaster.
Together, these three elements form a formidable defense. By embracing the principles of confidentiality, integrity, and availability, you bolster resilience and instill confidence in the face of evolving cybersecurity challenges.
Let’s take a deeper look into each of these pillars and how they work together to create strong information security protocols.
1. Confidentiality
Data confidentiality means that data should only be available to those with authorized access. In your organization, employees need easy access to the data and information that they require to do their job. Keeping data confidential, though, means that employees only have access to the data that’s they absolutely need.
Limiting how many people have access to different data sets improves your organization's ability to keep sensitive information confidential.
Data confidentiality is also a major consideration in identity and access management standards.
To achieve confidentiality, businesses can take advantage of data encryption technology and implement MFA (multi-factor authentication). Data encryption is the process of “scrambling” data to make it unreadable until it is delivered to the right person or user, at which point a decryption key is used.
MFA requires a user to validate their identity through multiple methods, such as using a code delivered to a device or a biometric like a fingerprint.

2. Integrity
Data integrity means information should be intact, complete, and accurate.
To ensure data integrity, businesses can maintain and optimize their IT infrastructure, back up their data, and create a data loss prevention plan that protects them in case of a severe data breach.
Data integrity is crucial for employees who use insights drawn from that data in their day-to-day decision making. In turn, data integrity is critical for organizations who are looking to remain efficient, measure things like productivity, and want to develop a competitive edge.
If your data is corrupt, modified without authorization, or otherwise inaccurate you’ll have no real way of knowing if what your business is doing is working.
3. Availability
The last of the three CIA components of information security is data availability. Data availability means that a network, system, and necessary devices are ready to use as intended by authorized personnel.
Essentially, data availability refers to your employees' ability to access the data they need at any given moment without delay. There are several factors that can hinder access to data, even for authorized users – especially in the era of cloud technology wherein so much data is hosted off-site.
Cyberattacks, data leaks, and even neglected IT tech stacks can lead to delays in accessing data, or worse, non-operational downtime.
By prioritizing information security as a core aspect of your cybersecurity strategy, you can drastically improve the employee experience and the overall security of your network.
The Difference Between Information Security and Cybersecurity
Information security and cybersecurity are closely related but distinct fields. InfoSec focuses on protecting data in all its forms, whether it's digital, physical, or even spoken. Its goal is to safeguard all data, regardless of form, and ensure it’s only accessible to authorized users while remaining accurate and reliable.
This can include both physical protections, like securing file cabinets, and digital security measures like managing access controls, or enforcing data privacy policies.
Cybersecurity, on the other hand, specifically deals with protecting data and systems in the digital realm. It aims to defend from cyberattacks, such as hacking, malware, and phishing, focusing primarily on networks, computers, and the internet.
While InfoSec covers broader information types and protection methods, cybersecurity zeroes in on safeguarding electronic data and digital infrastructures.
Why Is Information Security Important?
Information security is important for businesses as its fundamental purpose is protecting the most sensitive data that they house.
Organizations should include employee cybersecurity awareness as a part of their information security initiatives and overarching cybersecurity strategy. Having your employees understand the goals of new technology and security protocols will help them follow these procedures that protect data and build a security-first mindset.
“Sometimes people do unsafe things to get around a security control designed to protect the data from exposure. While some controls may make it harder for people to get their jobs done, it is important to pair these controls with education to at least let people know the 'why' behind the process.” – Data Breach Investigations Report, Verizon
It’s crucial for modern businesses to understand the role of information security, its components, and what standards should be in place to position themselves for effective data security.

Rising Attacks, Volume of Data, and New Work Environments
It would be remiss not to call attention to some key factors that are quickly shifting the cybersecurity environment for organizations to understand why InfoSec is such an important consideration today.
Firstly, data breaches are a common occurrence in companies today, and not just for large enterprises, but for SMBs, too. The price of losing information to a data breach is an increasing burden for organizations.
Not only are cybercrimes costing organizations more money every year, but they’re also increasing in frequency as more businesses collect and store mass amounts of consumer data on a regular basis. As organizations increase their digital capabilities, so do cybercriminals.
Equipped with sophisticated technology, cybercriminals are on the lookout for unprepared prey, regardless of size. Investing in a comprehensive cybersecurity strategy that includes information security can help organizations avoid nasty cyberthreats.
Another consideration to take into account about information security is the new approach to work environment and culture. More employees than ever before are working off-site, which can add complexity to the cybersecurity protocols necessary.
In short, the digital era has made information security a necessity for any and all organizations that want to stay modern, protected, and competitive in the current market. Looking to the CIA triad for guidance, organizations can position themselves to be as secure as possible in an era where cyberthreats are only getting worse.
Wrapping Up on Information Security and the CIA Triad
The three components of information security are confidentiality, integrity, and availability.
By putting a strategy in place that accounts for all three of these—which is principally done through access controls, authentication and verification, and data segmentation—businesses can keep their data as protected as possible.
All of this in turn is part of a larger overarching cybersecurity strategy, in which information security plays a major role.
Cybersecurity is an ever-evolving industry and your solutions need to grow with you. Get an idea of where your current cybersecurity posture is compared to industry standards with DOT Security’s Cybersecurity Checklist: How Covered is Your Business?
