Cybersecurity Consulting
What Is Managed Detection and Response?
May 13, 2025
7 minute read

When you’re driving your car, the dashboard is equipped with a variety of indicators that inform you of malfunctions as they occur. As they come up, you can address some of these issues yourself, while you’ll need a mechanic for others.
Managed detection and response (MDR) services are like having a mechanic on call 24/7 - providing threat detection, diagnosis, and neutralization in real-time.
Sign up for our newsletter!
In modern cybersecurity practices, managed detection and response is considered to be a crucial arm of a comprehensive and layered security strategy.
Get started with a strategic cybersecurity partner who can bolster your security strategies, minimize vulnerabilities, maintain industry compliance, and improve your overall resilience.
The Basics of Managed Detection and Response
Managed detection and response uses advanced tools and data analysis to monitor your network, devices, and user behaviors to identify unusual activities that could indicate a cyber threat.
Once something suspicious is identified, immediate action is taken. The issue will be investigated, analyzed, and, if found to be a valid threat, neutralized. This could involve isolating and removing unauthorized access, eliminating harmful malware, or patching security updates to remove vulnerabilities and prevent future attacks.
Think of MDR as your personal watchdogs. They're there to protect your business from cyber threats 24/7, giving you peace of mind knowing that your digital assets are in safe hands.

5 Key Components of MDR
There are several key components involved in managed detection and response. In the following sections we break down five crucial components of MDR cybersecurity services:
-
Continuous Monitoring
-
Threat Detection and Analysis
-
Incident Response
-
Vulnerability Management
-
Remediation
1. Continuous Monitoring
In the context of a bank, continuous monitoring would have a security team watching live footage streamed from security cameras. Similarly, in MDR, continuous monitoring involves the ongoing surveillance of your network, devices, and data streams.
This constant vigilance involves analyzing network traffic patterns, clocking user activity logs, and monitoring system configurations for irregularities.
By maintaining watch over your digital assets, continuous monitoring allows for the swift identification of anomalies, empowering organizations to take proactive measures to safeguard sensitive information and their critical infrastructure.
2. Threat Detection and Analysis
When anomalies are flagged through continuous monitoring, the process of threat detection and analysis comes into play. This involves a comprehensive examination of the detected threats to discern their nature, intent, and potential impact on the organization's security posture.
Sophisticated threat detection tools leverage algorithms and threat intelligence feeds to identify known malware signatures, unusual and suspicious behaviors, or indicators of compromise (IOCs) within the network. The subsequent analysis aims to determine the root cause of the threat, assess its severity, and ascertain the extent of its infiltration into the organization's systems.
Threat prioritization is also a part of the analysis stage. Once a threat is detected and analyzed, it will be prioritized and ranked by severity. The more critical the threat is, the higher priority it needs to be for your security team.
By conducting thorough threat analysis, organizations gain valuable insights into evolving cyber threats, enabling them to formulate strategies for mitigation and response.
3. Incident Response
Despite proactive measures, cybersecurity incidents can still occur, calling for a rapid and coordinated response to mitigate the impact. Incident response is the structured process of detecting, responding to, and managing security breaches and cyberattacks.
Once an incident is detected, it is important to promptly contain it to prevent further damage or unauthorized access. This may involve isolating affected systems, blocking malicious network traffic, or disabling compromised user accounts.
Following containment, incident responders conduct a thorough investigation to determine the root cause of the incident, assess its severity, and understand the extent of the breach. This involves gathering evidence, analyzing logs and vast data sets, and identifying the tactics, techniques, and procedures (TTPs) employed by the attackers.
The findings of the investigation inform subsequent remediation efforts and help organizations implement measures to prevent similar incidents in the future.
By promptly containing and neutralizing security breaches, incident response mitigates potential damages, enhances resilience, and safeguards the organization's reputation.
4. Vulnerability Management
A vulnerability is a flaw in software, systems, or configurations that can be targeted by cyberattacks and compromise an organization.
Vulnerability management is the process of identifying and patching any existing vulnerabilities across the network. This involves ongoing activities such as installing security updates in a timely manner, researching and preparing for new and sophisticated cyber threats, and creating additional security layers so if one vulnerability is exploited, compromise is limited.
By staying abreast of emerging threats and promptly addressing vulnerabilities, organizations can bolster their resilience against cyberattacks and minimize the likelihood of successful exploitation by malicious actors.
5. Remediation
In the remediation phase, cybersecurity experts isolate and neutralize threats. Once a security incident has been detected and analyzed, remediation involves taking specific actions to terminate the risk, prevent further damage, and restore normal operations.
The remediation process may vary depending on the nature and severity of the cybersecurity issue. It can include a range of actions such as patching software vulnerabilities, disabling compromised accounts or systems, removing malware, enhancing security configurations, and implementing security best practices to prevent similar incidents in the future.
Overall, remediation in MDR aims to minimize the impact of security incidents, protect sensitive data and assets, and strengthen the organization's overall cybersecurity posture.
The Benefits of Managed Detection and Response
Managed detection and response offers a host of benefits to organizations seeking to fortify their cybersecurity defenses.
Firstly, MDR provides proactive threat detection capabilities, using monitoring tools to identify security threats in real-time. This proactive approach enables organizations to mitigate risks before they escalate into significant breaches.
Additionally, MDR offers 24/7 network monitoring through analytic software that’s later reviewed by cybersecurity experts, ensuring that organizations are never unprotected. With MDR, organizations gain access to security analysis from experienced professionals who possess the skills and resources to investigate security incidents thoroughly and provide actionable insights for remediation.
MDR services also enable rapid incident response, minimizing the impact of breaches and reducing potential downtime. By leveraging scalable solutions and advanced technologies, MDR services can adapt to the evolving needs of organizations, providing flexibility and agility in addressing cybersecurity challenges.
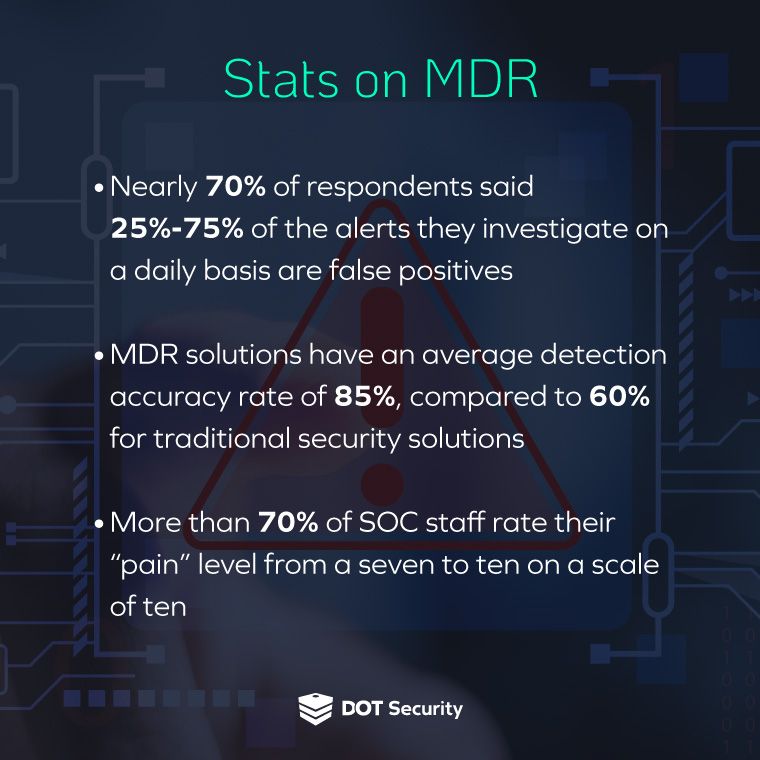
Furthermore, outsourcing security monitoring and incident response to managed security service providers (MSSPs) can be more cost-effective than maintaining an in-house cybersecurity operation, as it eliminates the need for substantial investments in both staff and infrastructure.
Overall, managed detection and response services empower organizations to enhance their cybersecurity, proactively defend against cyber threats, and focus on core business functions with confidence.
Implementing MDR
Implementing managed detection and response is less about buying a product and more about building a smart, responsive partnership. Organizations typically begin by evaluating their current security posture—understanding where gaps exist in threat detection, incident response, and continuous monitoring.
This self-assessment helps pinpoint why MDR is needed and sets clear expectations for the service. It's essential at this stage to get buy-in from both IT leadership and business stakeholders, as MDR affects not only technical operations but also compliance, risk, and business continuity.
Next, organizations research and vet MDR providers based on several key factors: 24/7 coverage, threat intelligence capabilities, detection methodologies (like behavioral analytics and machine learning), and response workflows. A strong MDR partner doesn't just alert you to problems—they help contain and remediate threats in real-time.
It's important to clarify who owns what during an incident and how fast action can be taken. Transparent SLAs, incident escalation paths, and integration with existing tools like SIEMs or EDR platforms are critical discussion points during this phase.
Once a provider is chosen, the onboarding process begins. This often involves deploying lightweight sensors or agents, integrating log sources, and customizing detection rules to align with your organization’s environment. Over time, the MDR service fine-tunes its threat detection to become more accurate and context-aware.
Continuous collaboration through regular threat reports, post-incident reviews, and tuning sessions ensures the MDR solution evolves alongside your organization’s threat landscape. In short, MDR isn’t a “set it and forget it” solution—it’s a living, breathing partnership that matures with your security needs.
MDR vs EDR vs MSSP
The security landscape is filled with acronyms that often sound interchangeable—but MDR, EDR, and MSSP serve distinct roles. Understanding their differences is key to building the right defense strategy.
- Endpoint Detection and Response (EDR) focuses specifically on endpoints: laptops, servers, and other devices. It collects telemetry, monitors for suspicious behavior, and enables security teams to investigate and respond to threats on those devices. While powerful, EDR is largely a tool that still requires skilled in-house analysts to interpret alerts and take action.
- Managed Security Service Providers take things further by offering outsourced monitoring of security devices like firewalls, SIEMs, and intrusion detection systems. They provide alerting and reporting, but often fall short on rapid response and deep incident investigation.
- Managed Detection and Response blends the best of both worlds. It delivers the advanced capabilities of EDR with the service orientation of an MSSP—but with a stronger emphasis on proactive threat hunting, real-time detection, and hands-on response. MDR providers not only alert you to threats but also help contain and remediate them, often within minutes. It’s this fusion of technology and expertise that makes MDR a compelling choice.
Wrapping Up on MDR
Managed detection and response is an integral aspect of cybersecurity that elevates system and network monitoring to the next level. With a powerful MDR process in place, your organization can take a more proactive stance on defense with precise and immediate threat response that neutralizes vulnerabilities across your network to keep your data safe.
Part of what makes MDR such a powerful cybersecurity tool is the combination of analytics, AI and machine learning, and the expertise of the professionals executing the managed detection and response tactics.
If you’re looking to enhance your cybersecurity with the help of experts and state-of-the-art technology, get started with DOT Security today.
