Network Security Monitoring
12 Basic Types of Network Security Measures
May 16, 2024
6 minutes

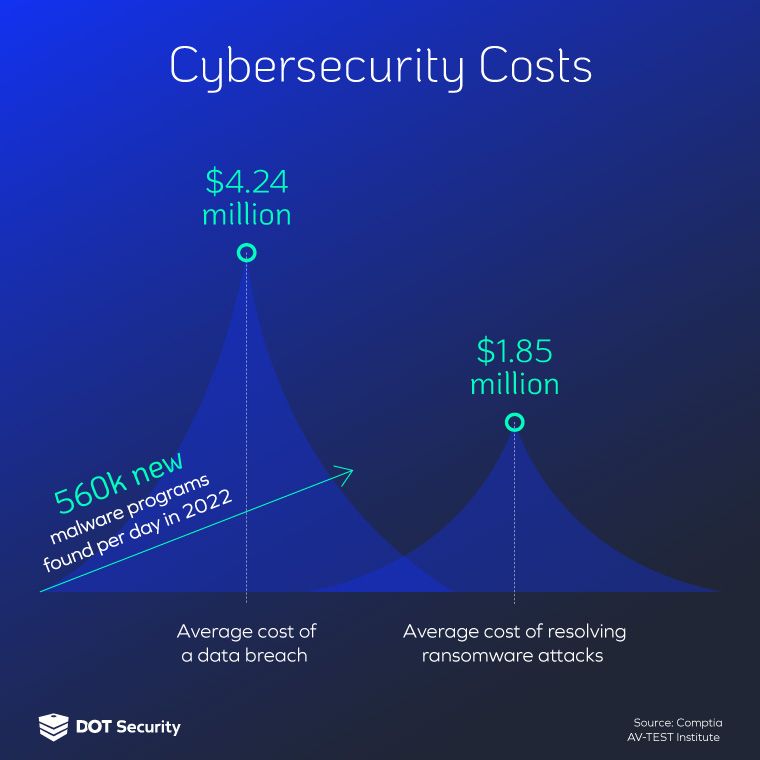
The costs of a data breach, including remediation, reach millions of dollars. In 2023 alone, cybercrime cost the world around $8 trillion. This would constitute as the world’s third largest economy and demonstrates just how important network security is today.
Network security measures bring together a series of technologies, protocols, and policies that work in concert to form a layered cybersecurity strategy. These layers create a foundation for comprehensive cybersecurity, meaning if one defense measure fails, another one is there to cover the gap.
Sign up for our newsletter!
Read through the following sections to learn about 12 foundational cybersecurity protocols.
Subscribe to the DOT Security blog to stay updated on everything cybersecurity, including the latest news stories, industry trends, and technological developments.
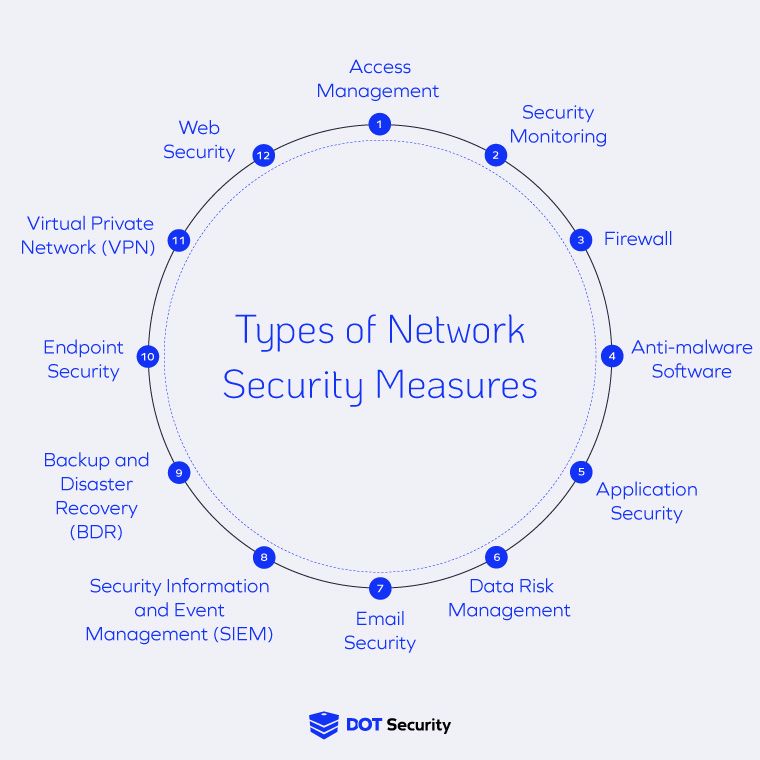
12 Basic Types of Network Security Measures
The cybersecurity space is swimming with advanced technologies. While no single solution will deliver comprehensive defenses, combining multiple controls will give you the best chance at preventing threats from blossoming in your systems.
The following 12 network security measures are designed to work in concert and substantially improve your cybersecurity.
- Access Management
- Security Monitoring
- Firewalls
- Anti-Malware Software
- Application Security
- Data Risk Management
- Email Security
- Security Information and Event Management (SIEM)
- Backup and Disaster Recovery (BDR)
- Endpoint Security
- Virtual Private Network (VPN)
- Web Security
Let’s look at how each of these network security measures works to safeguard a network infrastructure:
1. Access Management
Access management, also known as access control, is the verification and authentication of users before granting them access to data stored on a network. By having closed environments and limited access, users can only access the information they need for their job.
This makes it much more difficult for a threat actor to infiltrate a network, even if they compromise a legitimate user's account, because they won’t be able to freely bounce around without additional effort.
One of the primary objectives of identity and access management is to prevent unauthorized users from gaining access to sensitive information. Making use of the principle of least privilege, access management is essential for risk mitigation and significantly improves network defenses.
2. Security Monitoring
Security monitoring plays a pivotal role in detecting and responding to potential breaches. This proactive approach involves a team of cybersecurity experts continuously monitoring the network, including software usage, online behavior, endpoints, and system logs.
By diligently scrutinizing network traffic and user activities, security monitoring identifies indicators of compromise or suspicious behavior. This detection enables organizations to intervene promptly, reducing the impact of breaches and minimizing potential damages.
By maintaining constant vigilance and leveraging advanced detection capabilities, security monitoring helps organizations stay one step ahead of cyber adversaries.
3. Firewalls
Firewalls regulate the flow of data between a network and the internet, acting as a barrier to keep data private. These perimeter defense mechanisms inspect incoming and outgoing network traffic, applying predefined rules to block potential threats.
Firewalls are customizable, giving them granular control over network traffic and mitigating the risks associated with unauthorized access. They ensure that only legitimate users and services can interact with the network.
In essence, firewalls play a critical role in fortifying network security by providing a robust barrier against external threats and unauthorized access.
4. Anti-Malware Software
Anti-malware and next-gen antivirus software is one of the better-known network security measures. This software keeps environments secure by monitoring, scanning for, and removing malware.
This software employs a range of detection techniques, including signature-based scanning, heuristic analysis, and behavioral monitoring. Together, they identify and neutralize various types of malware, including viruses, worms, Trojans, ransomware, and spyware.
Malware may destroy or steal sensitive data, or lie dormant to later create backdoor access for hackers. In 2023 there were over 1.2 billion malicious programs and potentially unwanted applications (PUA) in existence.
By deploying next-generation antivirus solutions equipped with advanced threat detection capabilities and proactive threat hunting capabilities, organizations can enhance their resilience against evolving cyber threats and minimize the risk of malware-induced security incidents.
5. Application Security
Application security encompasses a multifaceted approach to protecting software applications from potential security vulnerabilities through processes like automatic updates that install security patches and scanning tools that look for indications of malicious software.
Additionally, application security ensures that apps are kept up-to-date with the latest security patches and updates. By promptly addressing known vulnerabilities, organizations can avoid zero-day exploits and other attacks that exploit issues in the code of an application itself.
6. Data Risk Management
According to the Cost of Data Breach Report 2023 by IBM and Ponemon, it takes an average of 277 days to identify and isolate a data breach.
As the volume and complexity of data generated by businesses continues to increase, effective data risk management becomes imperative to safeguarding sensitive information and ensuring regulatory compliance.
By fostering a culture of data security awareness and accountability among employees, organizations can mitigate the risk of data breaches and regulatory penalties stemming from non-compliance with data protection regulations.
One of the primary objectives of data risk management is to proactively identify and assess potential threats and vulnerabilities that could compromise the confidentiality, integrity, or availability of sensitive data assets. This is often accomplished through a risk assessment.
7. Email Security
Email security encompasses a suite of technologies, policies, and best protocols designed to protect organizations from email-based threats, such as phishing attacks.
The primary objective of email security is to keep inboxes secure through spam filtering and malware scanning. These are tools that block suspicious emails from getting to your inbox in the first place and help you identify malicious or phony links.
Phishing, a social engineering technique used by cybercriminals, is one of the most popular email attacks in which threat actors pose as trusted figures in order to receive sensitive data. It’s also important to note that there are a wide variety of phishing attacks such as volume phishing, whale phishing, and even vishing (voice phishing) and smishing (SMS phishing).
2023 saw the largest number of phishing emails in history, totaling 1.76 billion.
Phishing tactics have improved as attacks increase with the rise of remote work and lack of proper training. Monitoring suspicious emails as well as training employees and implementing multi-factor authentication (MFA) to improve your cybersecurity posture can help mitigate the risks created by email scams.
8. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) refers to a comprehensive approach to cybersecurity that combines real-time monitoring, advanced analytics, and centralized log management to detect, investigate, and respond to incidents.
By leveraging advanced correlation algorithms and threat intelligence feeds, SIEM solutions correlate disparate security events and prioritize alerts based on their severity and potential impact on the organization.
By maintaining comprehensive audit trails and documenting security incidents, organizations enhance their ability to respond to regulatory inquiries and investigations.
9. Backup and Disaster Recovery (BDR)
Backup and disaster recovery (BDR) ensures business continuity in the event of data loss, system outages, or catastrophic events. BDR solutions encompass data backup, replication, and recovery capabilities, allowing organizations to create redundant copies of their data and infrastructure resources to minimize the impact of potential disruptions on their operations.
By implementing robust backup and recovery strategies, organizations can feel confident in their ability to act with resilience in the event of a cyber incident, a natural disaster, or any other event that causes downtime.
10. Endpoint Security
Endpoint security is protecting individual devices, such as computers, mobile devices, and Internet of Things (IoT) devices, from a myriad of cyber threats.
One of the primary challenges in endpoint security is the diverse range of threats targeting these devices. To counter these threats, organizations deploy advanced solutions equipped with antivirus, anti-malware, and intrusion detection capabilities. These solutions monitor and analyze endpoint activities in real-time, identifying and neutralizing threats before they can cause harm to the network infrastructure.
11. Virtual Private Network (VPN)
A virtual private network (VPN) is a critical tool for ensuring secure communication over the internet, particularly in remote work environments.
VPNs encrypt data transmissions between a user's device and a remote server, protecting sensitive information from interception or surveillance by malicious actors. This encryption ensures the confidentiality and integrity of data, even when transmitted over unsecured or public networks.
In essence, VPNs provide a secure and private means of accessing the internet and corporate networks, enabling organizations to maintain business continuity and productivity no matter where their employees log in.
12. Web Security
One of the primary challenges in web security lies in defending against web-based threats, such as malicious websites, drive-by downloads, and cross-site scripting (XSS) attacks.
To mitigate these risks, organizations deploy web security solutions, such as web application firewalls (WAFs) and content filtering systems, to detect and block malicious web traffic and prevent unauthorized access to sensitive information.
Web security also works to block access to sites that may contain malware. These tools work in concert to keep both users and devices safe as they browse the vast ocean of the internet.
Wrapping Up on Basic Network Security Measures
By implementing the protocols outlined above, modern organizations can build a layered cybersecurity strategy that offers them comprehensive protection against sophisticated threats. More than any single solution can deliver by itself, the strongest strategies make use of several tools, procedures, and technologies to defend your entire company.
The harder you make it for a threat actor to infiltrate and compromise your network, the more likely it is that they’ll pivot to an easier, less prepared target.
Subscribe to the DOT Security blog for updates on the latest cybersecurity headlines, industry trends, and other developments you don’t want to miss!
