Identity And Access Management
What Is Privileged User Access Management? Why Do You Need It?
March 14, 2024
9 minute read

Privileged access management (PAM) is an arm of identity access management (IAM) that specifically focuses on securing and monitoring high-privilege accounts that go above and beyond the capabilities of standard users.
Privileged accounts typically have the authority to access and control critical systems, sensitive data, and administrative functions within an organization's IT infrastructure. Privileged accounts are often held by system administrators, IT personnel, and other trusted individuals who require elevated access rights to perform their duties effectively.
Sign up for our newsletter!
As such, privileged accounts are prime targets for cybercriminals seeking to exploit vulnerabilities and gain unauthorized access to valuable resources. Privileged access management solutions are designed to prevent accounts with elevated access from being compromised.
If you don’t currently have privileged access management in place, there may be glaring vulnerabilities in your systems that cyberattacks can slip right through. Visit DOT Security’s Identity and Access Management solutions page and lockdown your high-privilege accounts today.
What Is Privileged Access Management (PAM)
Privileged access management encompasses a suite of strategies, processes, and technologies designed to control and monitor privileged accounts and resources.
Through the implementation of robust access controls, multi-factor authentication mechanisms, and adherence to the principle of least privilege, PAM solutions establish fortified security measures around high-privilege assets, mitigating the risk of unauthorized users, insider threats, and other potential security breaches.
Privileged accounts often hold the keys to the kingdom, if you will, granting users broad access to critical systems, sensitive data, and administrative functions. Consequently, if high-privilege accounts are compromised, it poses a significant threat to an organization's security posture, potentially resulting in data breaches or theft, substantial downtime or operational disruption, and financial losses.
By implementing a comprehensive privileged access management framework, organizations can proactively address these risks, ensuring that only authorized personnel can access, modify, or work within privileged accounts.
How Does PAM Work?
The operational framework of PAM revolves around several key principles.
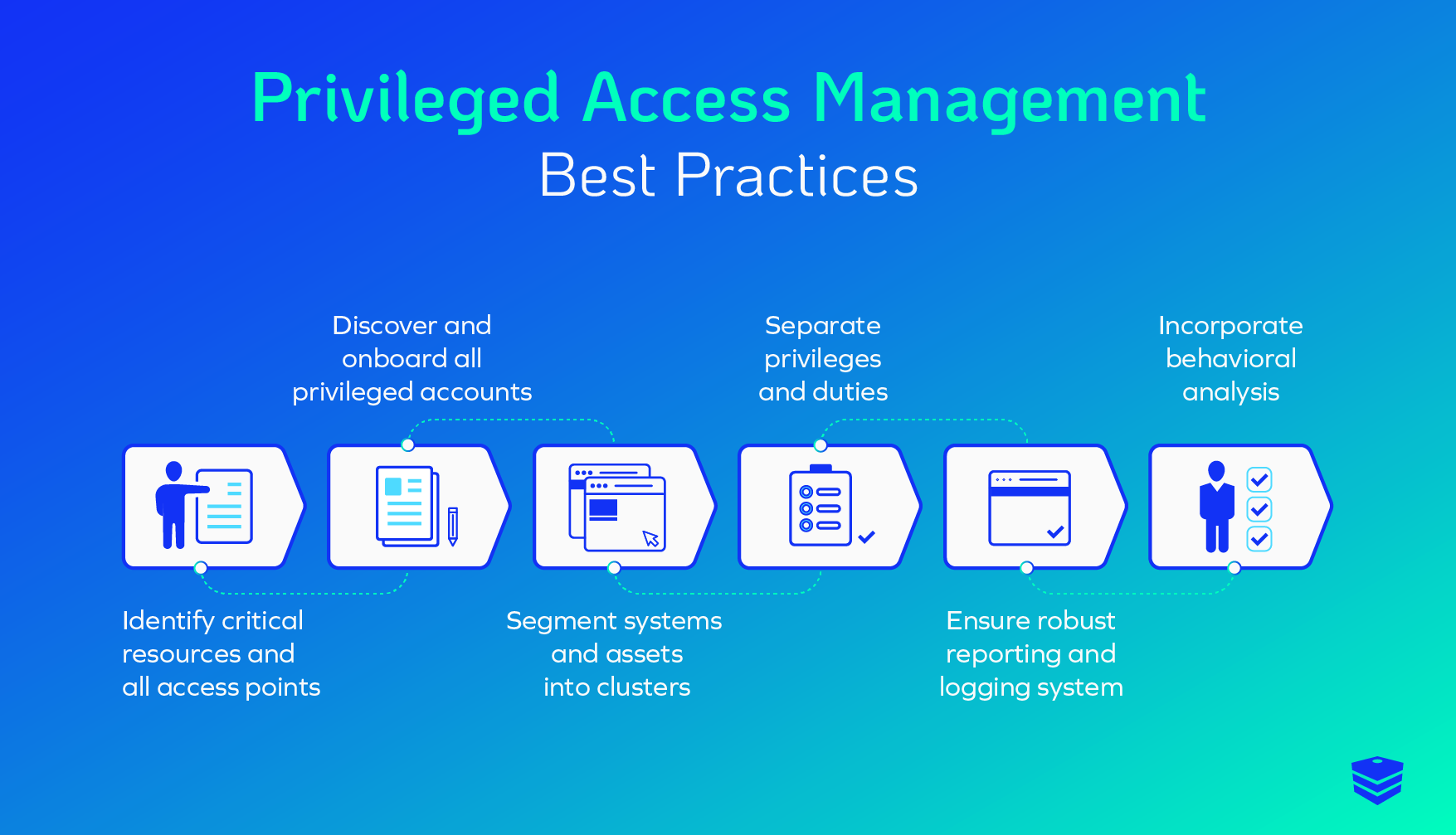
Firstly, PAM solutions authenticate users and validate access requests against pre-defined policies to ensure that only authorized individuals have access to the privileges associated with these accounts. This authentication process typically involves multi-factor authentication mechanisms, such as passwords, biometrics, or hardware tokens, adding an extra layer of security to the access control process.
In addition to authentication, PAM solutions employ granular access controls to enforce the principle of least privilege, limiting users' access rights to only those resources essential for their roles and responsibilities. By restricting access to sensitive systems and data on a need-to-know basis, organizations can minimize the potential impact of security breaches and insider threats.
Furthermore, PAM solutions facilitate the continuous monitoring of privileged account activities, generating audit trails, log books, and system alerts for suspicious behavior in real-time. This proactive approach enables security teams to detect and respond to potential security incidents promptly, thereby reducing the dwell time of attackers within the network.
How Does Privileged User Access Management Differ From Identity Access Management?
While both privileged access management and identity access management share the overarching goal of protecting the network against unauthorized user access, PAM is just one aspect of identity access management and specifically targets the unique challenges posed by high-privilege accounts, employing specialized techniques and controls to mitigate risk.
IAM, on the other hand, primarily focuses on managing user identities and their associated access rights across the entire organizational landscape, encompassing both standard and privileged accounts and a wider range of solutions and security mechanisms.
One of the key distinctions between PAM and IAM lies in their scope and level of control.
For instance, IAM solutions typically manage access at the user level, assigning permissions based on roles, groups, or organizational hierarchies. While this approach is effective for standard user accounts, it may fall short when dealing with privileged accounts, which often require more stringent access controls and monitoring.
PAM solutions, on the other hand, offer in-depth control over privileged access, allowing organizations to enforce strict policies and audit requirements tailored to high-privilege accounts.
Does PAM Work With Zero-Trust?
The concept of zero trust, which embodies the principle of "never trust, always verify," aligns closely with the objectives of privileged access management.
PAM seamlessly integrates within zero-trust architectures, providing granular control and continuous verification of privileged access requests regardless of the user's location or network context. By adopting a zero-trust approach alongside PAM capabilities, organizations can bolster their defenses against insider threats, external attacks, and compliance breaches, fostering a more resilient cybersecurity posture.
Zero-trust architectures operate on the premise that no entity, whether inside or outside the network perimeter, should be trusted inherently. Instead, access requests are subject to rigorous verification and validation, regardless of the user's credentials or privileges.
PAM solutions play a pivotal role in this balancing act by enforcing least privilege access controls, monitoring privileged account activities, and facilitating real-time threat detection and response. By integrating PAM into their zero-trust strategies, organizations can establish a comprehensive security framework that safeguards critical assets from unauthorized access and malicious activity.
How Privileged Access Management Improves Cybersecurity
The adoption of privileged access management represents a pivotal step towards enhancing cybersecurity resilience and mitigating modern threats.
By proactively managing and securing privileged accounts, organizations can effectively thwart unauthorized access attempts, minimize the risk of data breaches, and uphold regulatory compliance requirements. Moreover, the comprehensive monitoring and audit capabilities inherent to PAM solutions enable organizations to maintain security against new, sophisticated threats.
In addition to fortifying access controls, PAM solutions contribute to operational efficiency by streamlining user provisioning and de-provisioning processes. By centralizing privileged account management and automating routine tasks, organizations can reduce administrative overhead, minimize the risk of human error, and ensure consistent adherence to cybersecurity policies.
All-in-all PAM solutions provide valuable insights into user behavior and access patterns, enabling organizations to identify and address potential security gaps proactively. By leveraging these insights, organizations can fine-tune their security posture, strengthen their defenses, and adapt to evolving cybersecurity threats effectively.
Wrapping Up on Privileged User Access Management
When it comes to cybersecurity, you want to prioritize defense measures around the most critical and sensitive assets first. Since user accounts with elevated capabilities are prime targets for cybercriminals, it goes to reason that these accounts need additional security around them.
Privileged access management solutions allow your security professionals more visibility into privileged account activities, helps prevent insider threats, and protects highly sensitive accounts against compromise.
If a privileged account becomes compromised, it can be detrimental to the entire organization. If you’re looking to bolster security around privileged accounts, visit DOT Security’s Identity Access Management solutions page to get started.
