Secure Data Protection
Data Security Solutions and Best Practices in Cloud Computing
March 22, 2022
8 minutes

With more businesses using the cloud to store, transfer, and access data, it’s become increasingly important to ensure that effective cybersecurity steps are being taken to protect it.
Cyberattacks are increasing each year and without implementing the right security solutions, businesses are leaving their data out in the open, ready for the taking.
Sign up for our newsletter!
Read on to learn more about data security in cloud computing, why it’s so important for modern businesses, and the data protection solutions that businesses can use to help.
Why is it Necessary to Secure Business Data?
Without proper cybersecurity procedures and technology in place, you risk exposing your customer information, financial information, and other critical business data to those with malicious intent. Not to mention you increase your risk of major data breaches that can be expensive, detrimental to customer trust, harmful to your company’s reputation, and put compliance at risk.
The cost of a data breach in 2019 was $3.92 million and it’s rising every year and can take a week or more to regain access to company data
Critical Data Security Challenges and Solutions for Cloud Computing
To mitigate the risks of a data breach and protect data, businesses need to understand the challenges ahead of them and identify the solutions that will help overcome them.
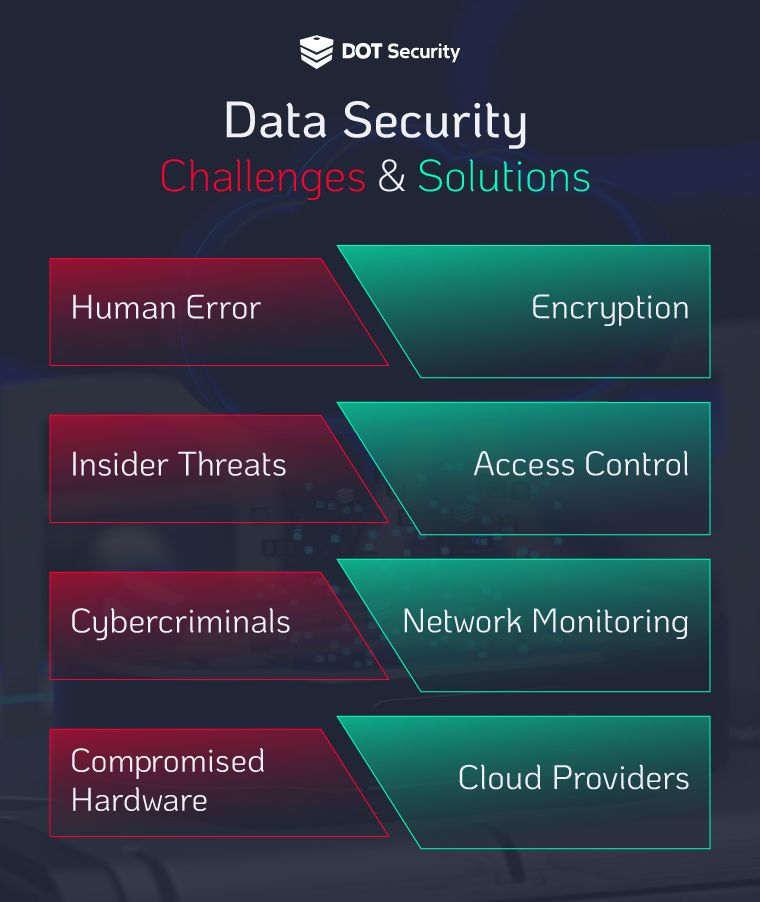
Challenges
Human Error: It’s a fact of life that humans make errors and sometimes simple errors can have big repercussions when it comes to data security. Human error comes in many forms, but most can be narrowed down to having a lack of knowledge or skill. This can lead to clicking bad links, losing credentials, not updating or securely storing login information, and many more actions that can expose a company to attack. Cybersecurity awareness training is one way to combat this to ensure your workforce is well trained in cybersecurity best practices.
Over 80% of data breaches are caused by negligence or mistakes
Insider Threats: An insider threat is a cybersecurity risk that involves an individual within an organization who has access to sensitive data. This can fall into the human error category with unintentional risks listed above. But it can also be intentional and malicious, involving espionage (hacking with a goal to steal data for a business advantage), revenge (disgruntled employees, for example), or for-profit with intent to sell the stolen data.
Cybercriminals: Obviously, cybercriminals pose a serious threat to businesses and their data as they attempt to penetrate your defenses to steal information. Their motives can be external like financial gain or recognition, or internal such as corporate espionage or revenge, as stated above.
Compromised Hardware: Faulty or compromised hardware can present huge security risks, especially because businesses use more of it than ever and in more places. Remote devices like laptops, smartphones, and tablets are connecting to company networks from unsecured Wi-Fi networks which can be easily hit by hackers without proper security.
Related: 5 Examples of Cyberattacks on Critical Infrastructure
Solutions
Encryption: To protect data in transit from the cloud, encryption is used to make the data unreadable to any unauthorized party who may get their hands on it. This is done by making the data appear random unless a cryptographic key is used to decipher it. These keys are handled and stored securely by authorized users.
Access Control: Implementing access management and controls is a way for businesses to control who has access to certain data. A typical cybersecurity principle is that of least privilege, meaning that users are authorized to access only what they require to do their jobs, limiting the scope of data they can get to.
Network Monitoring: Even with all the proper security procedures in place, businesses are still under threat of data breaches and other attacks that bad actors will use to infiltrate a system. Network monitoring gives you a watchdog that is constantly looking for threats, anomalies, and unusual behavior that could hint at a potential threat.
Cloud Providers: Part of the responsibility of data security falls on finding a cloud provider who has an effective cybersecurity system. Data centers that provide cloud storage remotely are divided into tiers based on cybersecurity stature, potential downtime, redundancies, and backup protection.
Cybersecurity Awareness Training: To lower the risk of human error, it’s important to keep your teams fully trained and updated on cybersecurity best practices. The better trained they are, the more likely they’ll be able to identify cyberthreats, report them, and save your business from harm.
How Businesses Can Stay Secure
Juggling new technology, new cyberthreats, and consistent updates and patches can be difficult, even for businesses with established IT or security teams. Partnering with a managed security services provider (MSSP) like DOT Security gives businesses access to the experts and tools necessary to always live on the cutting edge of cybersecurity and stay protected.
Related: Explaining the Evolutions of Cybersecurity Solutions and Threats (Infographic)
MSSPs like DOT Security have dedicated teams of specialists in every discipline of cybersecurity, including data security, to help monitor and manage security protocols. With this help, businesses can rest easier knowing that they’re doing everything they can to mitigate the risks associated with cloud computing and remote data storage.
If you want to learn more about secure cloud storage and what steps you can take to protect your organization’s data, explore our Insights Page for more helpful resources or contact an expert at DOT Security today.
