Endpoint Protection
What is Advanced Endpoint Protection (AEP)?
February 24, 2022
3 minutes

Operations in The Works, a books and crafts store chain in the UK, stopped in five of its stores when hackers gained access to its computer systems. This ransomware attack caused issues with card registers, stopped supply deliveries, and delayed online orders. This highlights the need for advanced network protection (AEP) to prevent attacks.
The last year alone saw a 50% increase in cyberattack attempts targeting company networks per week. While anti-malware software can stop some threats, newer or more persistent threats may go undetected. AEP comes in with sophisticated solutions that proactively monitor networks.
Sign up for our newsletter!
Advanced Endpoint Protection (AEP) Defined
Traditional endpoint security looks to protect endpoints — user devices such as computers, mobile phones, tablets, printers, and other portable devices — by detecting and filtering known threats. It encompasses software such as antivirus programs, firewalls, and VPNs.
However, as cyberattacks become more refined and hundreds of thousands of malware are created daily, traditional endpoint security is not enough to protect organizations’ networks.
Advanced endpoint protection, or endpoint security, accounts for different types of threats and their complexity. It uses technology to prevent new and advanced attacks from affecting a network. Advanced endpoint protection technologies include machine learning, real-time threat intelligence, endpoint threat detection, and next-gen antivirus.
Related Blog: What is a Firewall and How Does it Help Network Security?
Why Should You Implement Advanced Endpoint Protection?
AEP greatly decreases the chances of successful malware attacks. Real-time monitoring, local and remote device coverage, and data analysis to detect and eliminate persistent threats protects your network at all levels.
AEP tools actively monitor devices in real-time, respond to threats, and identify possible threats. It is a dynamic solution managing endpoints to protect the safety of your network.
How Do AEP Technologies Work?
Let’s take a more in-depth look at how each of these technologies work.
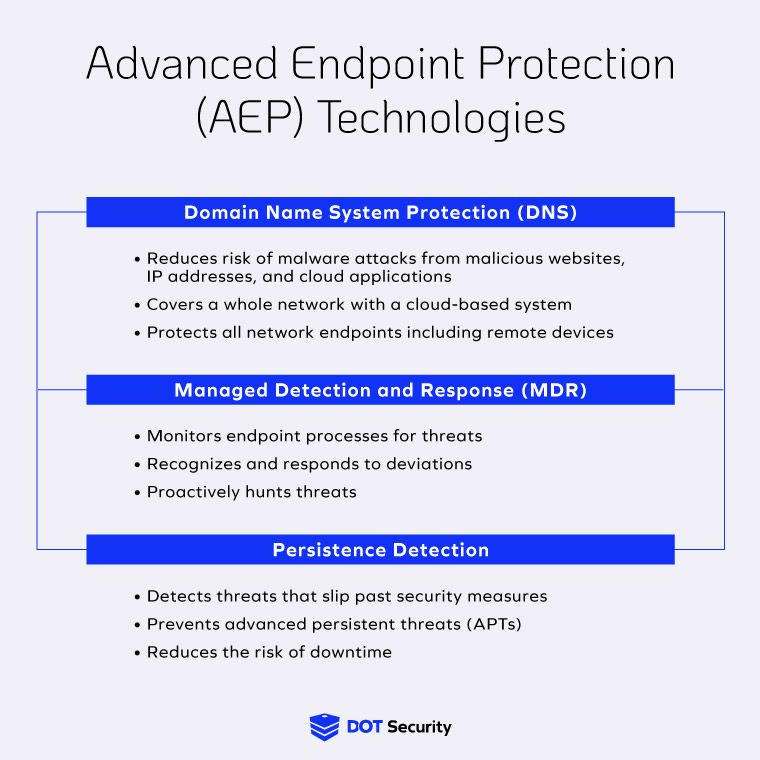
Domain Name System Protection (DNS)
When a device or endpoint on your network attempts to reach an outside source, such as a website or a cloud-based storage system, an inquiry is sent. DNS protection is a protocol through which these inquiries are filtered to block access to malicious websites, IP addresses, and cloud systems associated with malware.
We can visualize DNS protection as a call operator filtering calls to make sure the destinations you are trying to reach are not malicious. Safe calls will get connected and harmful ones will be filtered out.
As mentioned above DNS can extend to filter device traffic to all network endpoints, including remote work devices such as employee cellphones or laptops. This ensures network safety regardless of the location of the devices connected to the network.
Managed Detection and Response (MDR)
As the name suggests, managed detection and response tools proactively monitor processes to find any suspicious activity or possible threats.
One of these tools is next-gen antivirus (NGAV). NGAV is a technology combining machine learning and AI to identify and eliminate threats. With next-gen antivirus, algorithms sift through endpoint activity and user-behavior to determine what is usual activity and learn to detect threats.
Traditional antivirus software is updated by developers whenever a new threat has been registered. NGAV works to find threats before users take a hit.
Another MDR technology is endpoint detection and response (EDR). This is an extra layer of safety that makes use of data -analytics. With EDR, endpoint activities are recorded continuously. This collected data is then analyzed to discover potential security incidents.
EDR tools not only detect these incidents, but they also respond by hunting threats and containing attacks to reduce downtime.
Related Blog: What is Next-Gen Antivirus?
Persistence Detection
Advanced persistent threats (APTs) are prolonged and targeted attacks in which bad actors gains access to a network and wait for an opportune time to attack. To gain access, cyber criminals use tools like spear-phishing, which is phishing targeting a specific individual.
This is a newer hacking model, with many employees still not aware of how it works. Therefore, having a preventative tool in place can secure your network in case of unexpected breaches. Persistence detection technologies monitor network systems and devices to hunt for intruders that have cleared other layers of security.
This solution uses advanced technology to collect information and activity associated with persistent mechanisms that evade other cybersecurity technologies.
When an attacker is discovered, preventative measures are implemented, such as running protective software, adjusting user privileges, and blocking user activities if necessary.
Related Blog: 12 Basic Types of Network Security Measures
Bottom Line
Traditional endpoint protection does not provide enough security with the current rise and complexity of cyber-attacks targeting companies.
Advanced endpoint protection (AEP) actively fills security gaps by filtering traffic and malicious sites, learning from behaviors and recognizing deviations, and preventing ongoing threats.
AEP technologies include domain name system protection (DNS), managed detection and response (MDR), and persistence detection. These tools work as sentries to protect all network devices and connections.
Ensuring your organization’s network is safe is a continuous, evolving task, so make sure you have the right technologies working for you.
To add another security tool to your belt on top of AEP, this Infographic: Avoiding Phishing Scams: 6 Things to Look Out For! shows you how to identify these scams.
