Cybersecurity Consulting
The Evolving Cybersecurity Landscape and Your Business
August 18, 2022
7 minutes

The last few years brought about irreversible changes in the cybersecurity landscape. These changes, including the rise of remote work and of hacking attempts, have affected businesses of all sizes.
Currently, companies of all sizes and varied industries face a challenge, how to protect themselves against cybercriminals even as threats change and evolve daily.
While hacking began as a fun way to vandalize websites, it has evolved into a full-blown business, mainly targeting organizations to steal sensitive data for financial gain. Bad actors use tricks such as phishing, social engineering, and other manipulative tactics to exploit vulnerabilities.
What can businesses do to proactively defend themselves and where should they seek protection?
The Ransomware Business is Booming
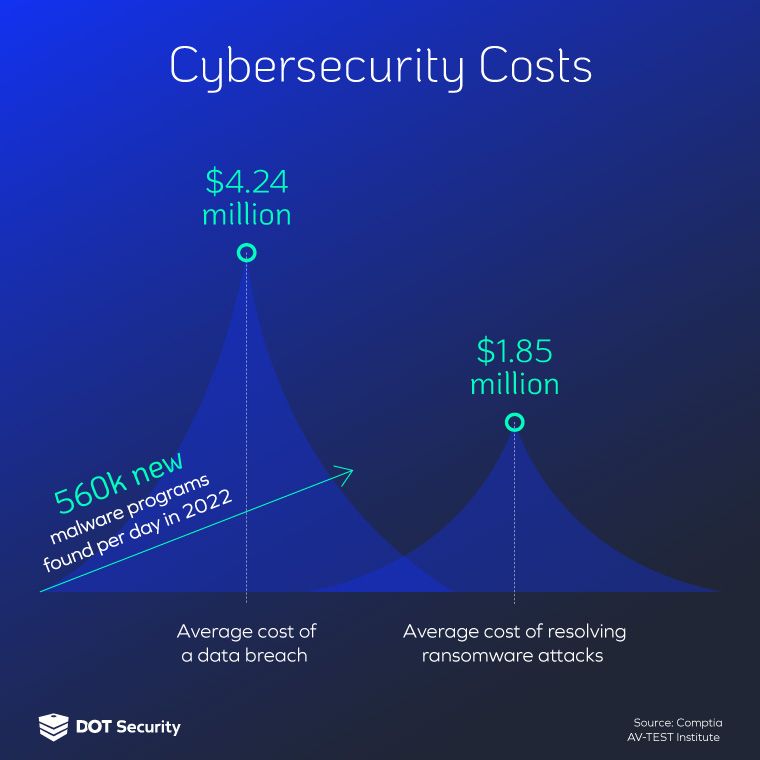
Since the rise of cryptocurrencies, hackers have become adept at making a profit from breaches. Therefore, the number of attempts and of members of their network have grown exponentially.
From 2004 to 2021, there have been a total of 17.2 billion records lost. Additionally, in 2022 alone, ransomware saw a growth of 13%, which is more than the last five years combined.
Since hackers have realized that ransoming businesses with multiple endpoints is more profitable than targeting individuals, ransoming has become a full-blown business with many people and technologies involved.
Cybercriminals use ransomware to encrypt a company’s data and demand payment in exchange for the return of that data. Since many organizations are unprepared for such an event without any data back-ups or recovery program many of these businesses choose to pay the ransom.
Yet one of the pathways for a hacker is often an employee mistake.
Related Blog: How Hackers Make Money: Insights from Chris Bisnett, Huntress CTO
The Ways Hackers Use to Breach Organizations
According to the 2022 Data Breach Investigations Report, cybercriminals use four prevalent actions to breach networks: hacking, malware, social, and error.
Hacking refers to any attempts by bad actors to intentionally breach a network and access data. Some of the most common ways hackers use to cause breaches include stolen credentials, exploiting network vulnerabilities, malicious websites, and denial-of-service attacks, in which they shut down devices or networks.
Malware is any harmful program or code that can alter an endpoint without users being aware. For example, a fake software upload, or backdoor malware, also known as trojans.
Social actions use social engineering such as manipulation or deception to incite users to take certain actions that will open a gateway for the hackers. This method includes email; phishing; spear phishing, which is phishing targeting a specific individual; and pretexting, which is manipulation in order to get private information.
Error encompasses any actions done incorrectly or left undone that leave vulnerabilities exposed. Errors include not changing default passwords, carelessness, misdelivery, or misconfiguration.
In 2008, the biggest cause of breaches was hacking. In 2022, it remains at the top.
Related Quiz: What Are My Chances of Being Hacked?
DOT Security and the Current Cybersecurity Landscape
As you can see, the cybersecurity landscape, its threats and risks are always evolving.
DOT Security understands that each organization has different issues to work through and different cybersecurity needs.
The DOT Security founders believe that cybersecurity should not only apply to enterprises or to individuals, but also to small and midsize businesses (SMBs).
SMBs have unique needs since they vary greatly in size and industry. Also, they often do not have the budget to have a complete in-house cybersecurity team. With the risk landscape changing so quickly, businesses should use cybersecurity consulting services to develop a security program.
Which is why DOT was born, to provide SMBs with a cybersecurity partner that delivers advanced tech and knowledge from experts.
Our process includes people, approach, and technology elements to form a customized cybersecurity program depending on your business needs.
DOT Security has trained, passionate experts. Our program involves a comprehensive audit with ongoing monitoring of your network. And our technology works to find the latest threats while ensuring your company complies with regulations.
Unlike other managed cybersecurity service providers, DOT Security has a full-time team of people constantly monitoring and learning about new threats in your environment.
We believe that businesses of all sizes should have access to cybersecurity in order to protect their data and continue to serve their customers uninterrupted. We partner with stakeholders to decide jointly on the best security program for each organization.
And we provide ongoing and cyclical maintenance, protection, and consultation.
Bottom Line
The global changes we encountered during the last few years had an unexpected outcome: the boom of the ransomware business. Cybercriminals are more organized and equipped than in the past to extort businesses for profit.
Hackers have become adept at using phishing and other social engineering methods to breach into organizations’ networks and in order to ransom valuable data.
DOT Security understands that all businesses need a cybersecurity solution and that each of their needs are unique and deserve a tailored cybersecurity program. That's why we partner with clients and assemble the best set of cybersecurity tools to safeguard their own organization.
Get your own tailored evaluation of your current environment, devices, and employee cybersecurity knowledge with a risk assessment from DOT Security today.
