Cybersecurity Consulting
How Hackers Make Money: Insights from Chris Bisnett, Huntress CTO
July 29, 2022
7 minutes

"They have excellent customer service. They would tell [each other] exactly what was wrong.” -Chris Bisnett on hackers
How hackers make money is a more organized and collaborative process than most people would assume. Since its modest inception, hacking has grown into a well-oiled machine targeting small and large businesses globally.
At our DOT Security SOC opening, Chris Bisnett, CTO of Huntress, — a security platform made by experts who monitor for advanced persistence threats — explained how hacking has expanded into the realm of organized crime.
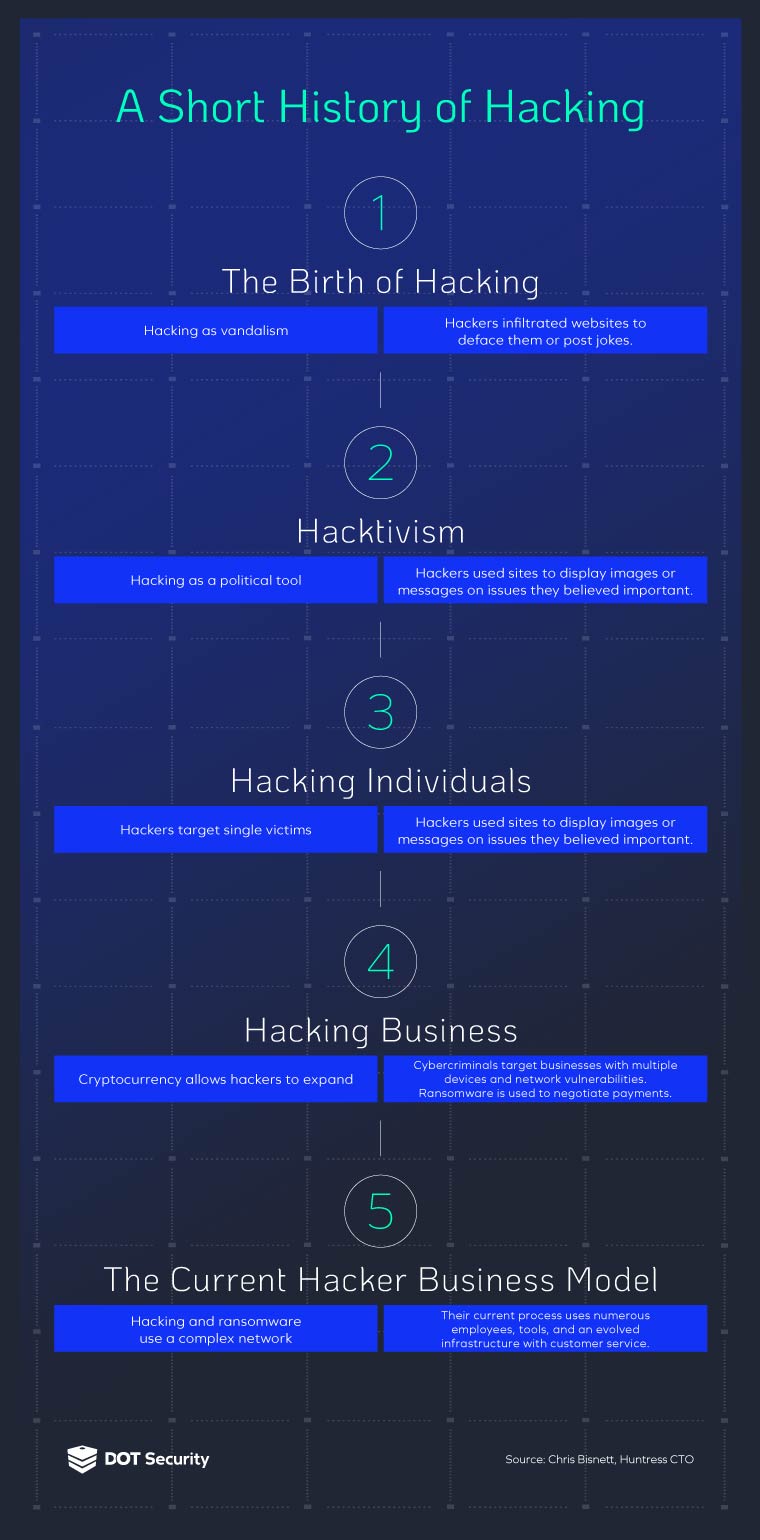
We bring you some of the best insights from his talk as well as the history of ransomware, information on how cybercriminals run their online network, and what steps businesses can take to protect themselves.
Sign up for our newsletter!
The Beginnings of Hacking
In the beginning of hacking, Chris Bisnett says, we had hacking as vandalism. Similar to graffiti on a shop front, hackers would deface websites, post jokes, and do tricks that were meant to annoy web masters and users, not to steal from them.
When Microsoft released Windows 98 in the late 90’s, it did not consider security as a factor. Since the number of internet users began to increase, and governments used Windows 98, issues arose, and exploitable vulnerabilities were found.
“[At this point], patching and thinking about security is not really a thing yet.” Chris Bisnett
The Internet Expands
With the rise of the internet, companies raced to leave their footprint online. With many business and government websites emerging, hackers had a field day exploiting vulnerabilities, Bisnett explains.
Companies and overnment agencies did not have cybersecurity teams at this period.
“Microsoft, at this point, hasn’t even considered the security development lifecycle.” Chris Bisnett
The Birth of Hacktivism
Most of the hacks in this period were done for fame or activism, Bisnett notes. Hacktivism, which involves hacking a device or network for political reasons, did not seek money as an end result.
With hacktivism, hackers attempt to give attention to an issue they believe is important. They often displayed images or messages on websites of organizations they opposed.
No Financial Gain
Since banks can track any movement of funds and reverse transactions deemed fraudulent, hackers had problems monetizing their initiatives. To retrieve funds from banks, individuals need identification, so cybercriminals could not extricate money without stating anonymous.
Finding customers is difficult when your goods are stolen. It is unwise to have items you bought with stolen funds shipped to your residence. For hackers, these issues meant that all their hard labor was rarely monetized.
Until the creation of bitcoin.
Cryptocurrency Payments
The creation of cryptocurrencies solved many problems for hackers. It changed how hackers make money, evolving it into feasible transactions.
They could now access funds that could not be reversed by a bank. Sending and receiving bitcoin can be done nearly anonymously. It’s relatively easy to exchange for goods or fiat currency.
Soon, ransomware expands to a full-blown business.
The Rise of Ransomware
With a means of earning income, ransomware as a business begins. In short, ransomware is a malicious software used to steal valuable data and to encrypt it so it’s unreadable to users.
To get the data back, victims need a key. Hackers keep the key from the victim and demand payment to get the encryption key.
At this point in time, many individuals and businesses did not have back-ups for their data, so they were easy targets for cybercriminals.
Related Blog: What Is the Optimal Data Backup Frequency?
Ealy Ransomware
At its outset, a handful of attacks would be successful. Some people fell for phishing and other scams. For businesses, ransomware was more of an annoyance.
Individuals, however, had a big problem since their personal and financial information was stolen. Yet hackers still did not make large profits because people mostly were not used to paying with cryptocurrency.
Businesses became a more profitable target.
Related Blog: How to Prevent Advanced Persistent Threats with Specialized Detection
The Next Level
Instead of ransoming individuals, hackers realized that targeting businesses with numerous devices would give them an advantage. Ransomware expanded even as businesses reacted by implementing better and more backups.
“[Hackers] then realized they can combine ransom with extortion.” Chris Bisnett
They would encrypt and steal files. If businesses refused to pay, cybercriminals threatened to release their data or report them to compliance regulators.
Here, small departments appear to handle the terms and negotiate between companies and hackers.
Specialization of Labor: How Hackers Make Money Presently
Eventually, cybercriminals scaled their businesses. They assigned roles and implemented hierarchies. They began to sell to other criminals, and the business bloomed, changing how hackers make money currently.
Some of the products and services bad actors created and sold online include:
- Ransomware as a service: Ransomware software made for sale
- Phishing Environment Rentals: E-mail and other environments created for hacking
- Selling victim credentials: Pay-per-user credentials for sale
- Sale of remote access tools (RAT): Allows bad actors to use devices remotely
To maintain this business infrastructure, hackers had to develop efficient methods of communication and customer service.
“They have excellent customer service. They would tell [each other] exactly what was wrong.” Chris Bisnett
Bisnett recommends adopting a hacker’s way of thinking.
Defending Yourself and Your Business
Bisnett recognizes that attempting to defend against all these threats is a serious and complicated task for an individual business to undertake.
Defending an organization takes many variables, including:
- Continuously moving software
- New vulnerabilities discovered daily
- Attackers constantly looking for victims
A basic security program demands asset inventory, regular updates, preventative security solutions, threat monitoring, and employee cybersecurity training.
Think Like a Hacker
Chris Bisnett advises organizations to follow the hacker philosophy and outsource any task that demands more work than can be efficiently done.
“What you can do, is think just like a hacker.” Chris Bisnett
He recommends businesses to ask the questions: How can we outsource security? Where can we find an expert who knows security? Who can we ask for help so we can focus on our business?
“That’s where we see a lot of ppl turning to places like DOT Security.” Chris Bisnett
Related Blog: Reactive and Proactive Cybersecurity Measures You Can Implement Today
Bottom Line
With humble beginnings, hacking has evolved from a juvenile vandalism act to a mature and organized business.
Bad actors have become adept at targeting companies, finding their vulnerabilities, and using these to steal data and negotiate for a ransom.
Hackers formed teams, support groups, and a complex online enterprise to attack companies. Organizations need many layers and experts to defend themselves. Since defending and proactively securing a business from cybercriminals takes a whole team of people, Bisnett advises to consider partnering with a cybersecurity provider such as DOT Security.
Cybercrime targeting businesses rises daily. When an organization is not secure, vulnerabilities abound that could lead to attacks, downtime, and loss of reputation. Ensure your company network is secure by reviewing our Cybersecurity Checklist: How Covered is Your Business?
