Cybersecurity Consulting
7 Steps in a Data Breach Response Plan
March 07, 2023
5 Minutes

Data breaches are not an uncommon sight in the news these days; businesses large and small have frequently experienced them in recent years. Therefore, all organizations should develop a data breach response plan as a risk management initiative.
Having a response plan means that were a breach to happen, you will be ready to effectively deal with it without wasting time or resources. Read on to find what steps make up this type of plan.
Sign up for our newsletter!
If you’d first like to learn how DOT Security can help you find and patch network vulnerabilities, head over to our Risk Assessment page.
1. Secure Your Network
Just like you would work to put out an emergency fire before planning any repairs or creating a contingency plan, your business should work to contain the damage caused by a breach.
To do this, inform your cybersecurity team or IT experts as soon as possible so they can take the necessary steps to minimize damage.
Your data breach response team should take care of the following before moving on to the next step:
- Isolating devices or systems that were infected or accessed by external threat actors, so the damage won’t escalate to your whole network
- Removing access to any compromised accounts. Additionally, asking employees to change their passwords and enforcing the use of MFA (multi-factor authentication)
- Going offline until the source of the breach is detected can also help you avoid further damage and stop data theft
2. Identify and Remediate the Source of the Breach
Do you know what type of cyberattack affected your systems? Whether it was ransomware, compromised credentials, or other, identifying the type and source of a breach will help you adjust your security strategy to prevent breaches in the future.
If your business takes advantage of technologies such as IDS or IPS systems, your breach response team can use the data logs these solutions collect to trace the breach to its origins.
Here are some of the solutions that can help businesses detect and identify threats and breaches:
-
IDS (Intrusion Detection System): This tool monitors your network and finds abnormal data patterns to detect threats
-
IPS (Intrusion Prevention System): A tool that detects and blocks a threat and can be customized with selected security policies
-
Persistence Detection: A team of human threat hunters that can identify persistent network intruders a software tool might have let through
Consider implementing a UTM (unified threat management) system—which includes an IDS and IPS solution—as part of your cybersecurity program to minimize the chance of future cyberattacks.
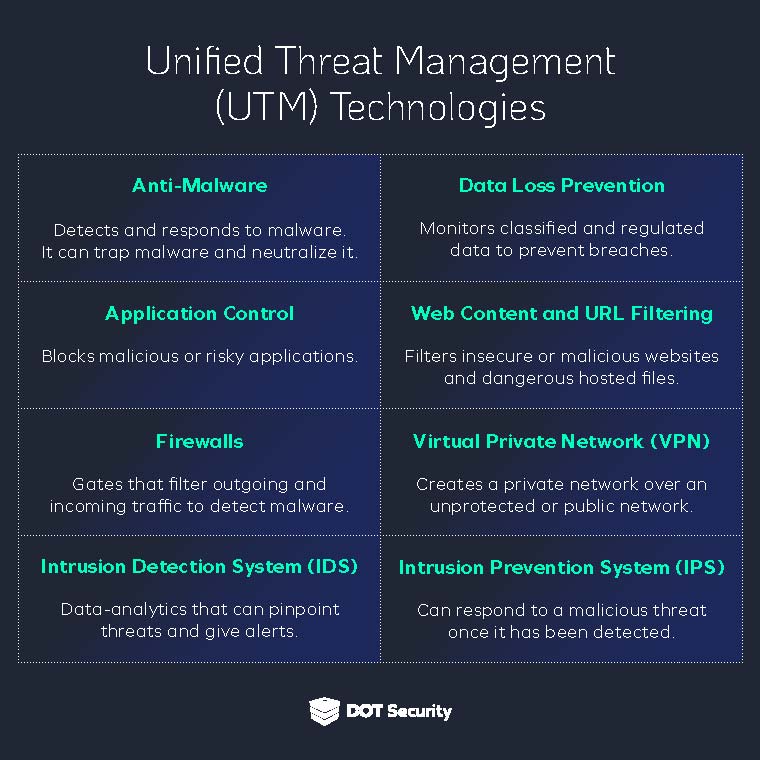
Once the threat is detected, your cybersecurity team can remediate the threat by killing it or identifying and removing an intruder if one is in your systems.
3. Test Your Fixes
Now that you’ve identified and stopped the breach, your IT or cybersecurity experts will need to test the fixes. Your data breach response plan should include a test step to check the affected systems as well as the entire network.
To do this, you can enlist the help of penetration testers. They are security professionals who make up a cybersecurity red team. "Pen testers” can take a deep dive into your entire network and detect vulnerabilities that need to be patched.

Even if your organization has not experienced a breach, penetration testing can help you discover any weaknesses in your network so they can be fixed before a bad actor finds them.
4. Inform Stakeholders and Customers of the Data Breach
For many businesses, this can be a hard step to take since it may lead to brand damage.
However, customer privacy laws require companies to disclose data breaches to affected customers when their personal identifiable information (PII) is involved.
Laws vary depending on the state, but since exposed personal information may lead to identity theft, businesses must let the affected parties know to prevent further brand identity damage. This also gives your customers a chance to take any precautionary measures such as cancelling credit cards.
Consider reaching out to compliance experts to get guidance on how best to safeguard customer data in accordance with federal and state laws.
5. Manage Reputational Damage
Technology giant Samsung dealt with blows to their image when hackers exposed 190 GB of sensitive data back in 2022. Their customers expressed concerns and lack of trust in Samsung after the breach.
A thorough data breach response plan should include a step to address any customer questions, complaints, and even monetary loss caused by the cyberattack.
When a data breach becomes public, customers and employees often look to company leaders and expect them to deal with the damages. In fact, one third of organizations saw a change in leadership after a cyberattack.
Executives and those in leadership positions should consider implementing cybersecurity employee training and adopt marketing initiatives to show their audience that they are proactively working to reduce the likelihood of future attacks.
6. Update Your Cybersecurity Strategy
Your business has dealt with a data breach as best it could. To avoid future breaches, companies should take advantage of a layered cybersecurity program if you don’t already have one.
Such a program would shield each layer of the network from its local devices to its cloud solutions. Additionally, employee training would ensure that your workforce is aware of the danger of cyber threats and uses cybersecurity best practices to minimize them.
7. Partner with a Cybersecurity Provider
A cybersecurity partner can assist in minimizing the damage of a data breach as well as offer guidance on how to best use technology and protocols to avoid threats in the future.
Businesses should look for a cybersecurity partner that offers the technology to deter threats and the expertise to guide its implementation. Security professionals will also work alongside business leadership to ensure your plan aligns with and facilitates business goals.
Bottom Line
A data breach response plan should include steps to contain the damage of the breach as well as initiatives to prevent similar attacks in the future.
Whether your business has suffered a data breach or is proactively preparing to minimize the chances of one, ensure your plan is guided by cybersecurity experts so that all layers of your network can be protected.
Taking charge of your business cybersecurity will help you prevent breaches. Get an expert’s evaluation of your current cyber environment, your organization’s devices, and your employee cybersecurity knowledge with our tailored Risk Assessment.
