Network Security Monitoring
How to Mitigate the Risks of a Zero-Day Vulnerability
October 25, 2022
6 Minutes

Contribute by Naveed Zahid, Associate Cybersecurity Analyst, DOT Security
In modern cybersecurity, businesses need to know how to mitigate a zero-day vulnerability to be able to stay secure against fast-moving circumstances.
Learn more about what a zero-day vulnerability is, how businesses can be prepared, and what can be done to stay secure.
Sign up for our newsletter!
What is a Zero-Day Vulnerability?
The term "zero-day" refers to freshly identified security flaws that can be exploited by hackers and other bad actors to attack systems/organizations. When a vendor or developer discovers a vulnerability on a zero-day, it means they have exactly zero days to patch it because they have just become aware of it.
This kind of attack takes place only when a hostile actor becomes aware of the gap before the appropriate parties have an opportunity to close it.
Types of Zero-Days
There are three types of zero days encountered by cybersecurity professionals:
- Zero-Day Vulnerability: A software vulnerability known as a zero-day vulnerability was found by attackers prior to the vendor being aware of it. Since there is no patch for zero-day vulnerabilities due to the suppliers' ignorance, attacks are more likely to succeed.
- Zero-Day Exploit: Hackers employ a zero-day exploit to target systems that have a previously unknown vulnerability.
- Zero-Day Attack: This is when a system is vulnerable, and a zero-day exploit is used to harm the system or steal data from it.

How Are Zero-Day Vulnerabilities Created?
Zero-Day Vulnerabilities are created when a system’s developer originally creates the system. Insecure Design (arise when security, QA, and/or development teams neglect to foresee and assess threats during the code design stage), security misconfiguration, vulnerable and outdated components, cryptographic failures, broken algorithms, broken access control, bugs, weak passwords, or programming errors by developers are just a few examples on how the vulnerability can be created.
How Do Hackers Discover Zero-Day Vulnerabilities?
How is it that hackers can discover these vulnerabilities? The most popular ways are vulnerability scanners and other tools created by the bad actors themselves. These tools check a target network for several known flaws and, during this process, can potentially find hundreds more.
As a result, attackers have an edge over system administrators because they only need to locate one way in, but the system professionals who created it must fix numerous vulnerable places. Attackers can also employ evasion strategies at both the application and network levels. Organizations that use intrusion detection systems should still be concerned, however, because there is no current detection in place looking for it. This means that the company might have to create that detection capability alone or with its cybersecurity partners.
Related Blog: What Do Cybersecurity Analysts Do?
Bad actors can use one of a few straightforward tools like traceroute, a computer network diagnostic tool, to obtain crucial network data such as the mapping of systems, routers, and firewalls. Along with what traceroute renders, they may also add sweeping capabilities using tools like Cheops, a network management tool.
To learn more about the types of services being utilized on the target machine, businesses can use port scanners to locate listening ports. The most effective method of defending against port scanners is to turn off superfluous services. Superfluous services are services that are not needed for a business to operate, so it will depend on each organization to determine them.
Who is at Risk?
At the end of the day, anyone utilizing an exploited system can be a zero-day exploit victim. Because exploit malware can infect operating systems, web browsers, programs, open-source components, hardware, and even IoT devices through normally safe web surfing habits, a zero-day vulnerability can pose major security concerns to everyone.
These dangers include using a website, responding to a phishing email, or watching an infected video.
The common targets for these attacks are:
- Companies with poor cybersecurity hygiene
- Companies that handle sensitive information such as personal identifiable information, credit card, banking information, and defense field
- Small and medium-sized businesses that have no to minimum cyber security
Finding Vulnerabilities in Your Software and Network
Every software company devotes a significant amount of effort and money to finding and resolving flaws in its products. Even though it might appear straightforward, finding, and fixing vulnerabilities is a difficult undertaking. Numerous scanning tools are required to find security flaws in networks and applications. These are comparable tools that hackers can utilize as well. To check each computer for security problems, those programs also make a list of all IT assets, including servers, PCs, virtual machines, operating systems, apps, and active ports. Companies release patches to address vulnerabilities as soon as they are discovered.
Sometimes, software users or cybersecurity researchers can spot software flaws and report them to the relevant software developer. For example, Google will reward and acknowledge those who alert them to security problems in their products. These awards, which are frequently referred to as "bug bounties," can be worth tens of thousands of dollars. Those people who do this are known as white hat hackers and compared to those who have black hat hackers who will use these flaws to their advantage.
The main risk for businesses involving zero-day exploits is who discovers them and what the discoverer does with the information.
What Can You Do to Protect Yourself Against a Zero-day Vulnerability?
To start, it’s important to stay informed. For example, at DOT Security, our experts subscribe to multiple threat intelligence sources and have relationships within the information security community that we use to obtain zero-day information. Once a zero-day vulnerability is discovered, our teams will work collaboratively to find a solution that enables our clients to detect the threat and block it until a patch for the vulnerability is made available.
A Zero-day vulnerability has a range of effects, with cost being the biggest drawback. Millions of dollars can occasionally be spent on data loss and recovery, not to mention the harm done to trust and the reputation of an organization. Enterprises face a variety of issues because of fraud, access authorization, and bot attacks, which are also significant participants. Productivity frequently suffers as a result, and data recovery and security efforts take up unneeded time and resources.
Having the appropriate security technology or a cybersecurity partner who can accomplish this for them, specifically a web application firewall (WAF) and many other security technologies that help safeguard organizations, is one of the primary ways for any business to stop a Zero-day attack in its tracks from many unknown threats.
Protecting Against Increasing Zero-Day Dangers
According to Mandiant, zero-day vulnerabilities have increased year over year and the trends show that it’ll only continue to go up. Anyone can be a target if they are a user of a system that has a zero-day vulnerability in it.
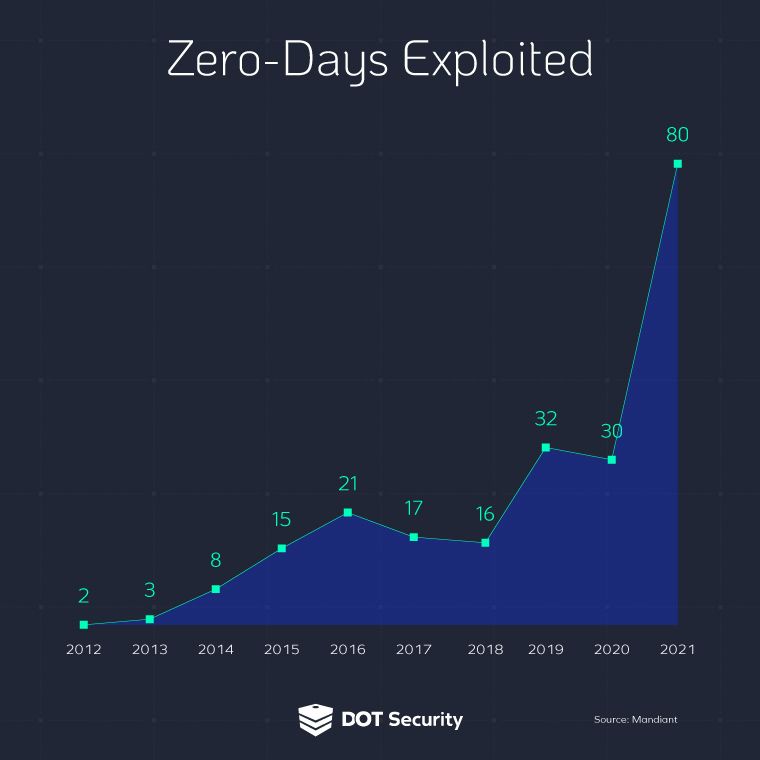
Zero-day vulnerabilities and attacks are complex contemporary dangers that can harm any firm, business, or organization. They can frequently strike all forms of critical infrastructure, cripple businesses, and become a costly fix.
But, with proper awareness, a team of experts, and a plan moving forward, businesses can mitigate the risks of zero-day vulnerabilities to continue staying secure despite what cybercriminals can throw at them.
Wondering how protected your business is from zero-day attacks and other forms of cyberattacks? Use this checklist to help determine your preparedness against modern threats.
