Cybersecurity Consulting
Notable Recent Data Breaches in 2022
December 01, 2022
7 Minutes

A number of companies famous domestically and abroad fell victim to recent data breaches in 2022. Malicious hackers are working to create new ways of gaining access into networks and steal data daily. Currently, 68 records are compromised per second, which means organizations must reinforce their defenses in order to stay secure.
Below, we’ll show you some of the most notable recent data breaches of 2022. Read to learn about these real-world examples of cyberattacks on companies big and small, so you know what they really look like and what to watch for.
Sign up for our newsletter!
Start by identifying which areas to focus on when preparing your defenses by reviewing our Cybersecurity Checklist: How Covered is Your Business?
US Federal Network Hacked
Hackers compromised a federal agency and deployed a cryptocurrency miner into its systems. The hackers were backed by the Iranian government, according to an advisory released by the FBI and CISA (Cybersecurity and Infrastructure Security Agency).
The hackers launched an advanced persistent threat (APT) attack. This type of attack involves malicious actors gaining access into an environment and staying in it for months or longer. Their purpose is escalating their privileges to gain access to increasingly sensitive data and to move laterally across the network.
The graphic below shows an attacker's journey when directing an APT attack:
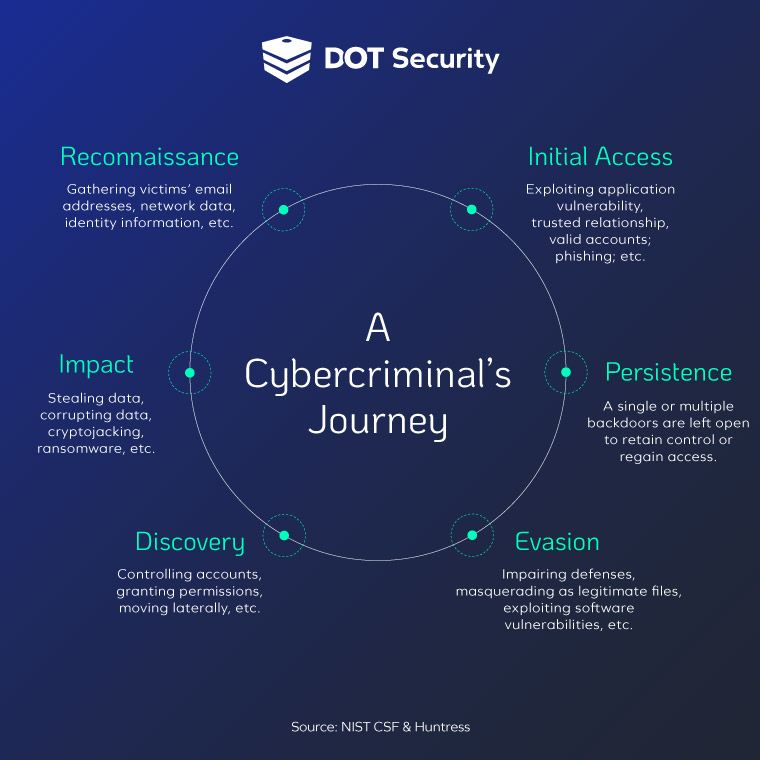
In this attack, which targeted a Federal Civilian Executive Branch (FCEB) organization, the cybercriminals went as far as to install crypto mining software. However, whether this was the main goal or they had other motives is still unclear.
Although the Iranian government has denied all involvement with the incident, the CISA reports that the attack may have begun in “February 2022, by likely Iranian government-sponsored APT actors.” CISA informed agencies of the vulnerability that caused this breach in December, which means the hackers were able to infiltrate the organization for months.
In order to mitigate these types of risks, the CISA published a number of recommendations, including:
- Using firewalls or web-application firewalls
- Using multi-factor authentication (MFA)
- Limiting access to domain controllers and systems used to make and manage accounts
- Resetting default usernames and passwords immediately after installation
- Monitoring for unexpected processes and executed commands
Advanced persistent threat (APT) attacks cannot be easily found by simple cybersecurity software such as anti-virus. This type of threat requires human hunters to monitor for unexpected activity in a network in order to find the bad actors hiding in it. Threat detection and response is an effective way to combat APT attacks.
Related Blog: How to Prevent Advanced Persistent Threats with Specialized Detection
Hospitals Report Stolen Patient Information
Cybercriminals used a remote customer support program to gain entry into New York Presbyterian Hospital’s staff computers. The hackers downloaded a number of files which included protected health information (PHI) belonging to their patients, according to TechTarget.
Healthcare entities must notify patients whenever protected health information is disclosed or breached accidentally or by design, according to HIPAA’s Breach Notification Rule. In November of 2022, patients were informed that some of the leaked data included “names, insurance authorizations, addresses, medical records, and exam results.”
Related Blog: What are the Consequences of a HIPAA Violation?
In another healthcare breach, Gateway Ambulatory Surgery Center in North Carolina fell victim to a phishing attack. The bad actors were able to use a phishing email to access employee email accounts during the spring of 2022. Per HIPAA’s rules, the Surgery Center had to notify more than 18 thousand patients.
The attackers were able to obtain patients’ medical history, health benefit enrollment information, patient account numbers,” and more. For some of the affected, their Social Security numbers and driver’s license numbers were also exposed. Besides notifying patients, HIPAA requires breached organizations to pay fines whenever PHI is disclosed.
The graphic below explains the HIPAA violation tiers and their respective fines:

Could hospitals avoid such cyber threats? Some of the organizations implemented security technologies after the event, but often, prevention is the best way to deter malicious actors from deploying such attacks.
When it comes to phishing emails, the best way to spot and stop them is employee training. Employees are often targeted with emails containing malicious links or files, with more than 80% of organizations reporting phishing attempts. Preparing them to quickly identify this type of attack and have a plan of response could have helped this type of data breach.
Related Infographic: Avoiding Phishing Scams: 6 Things to Look Out For!
U-Haul Sued Due to Data Breach
U-Haul, the shipping and storage company, discovered a data breach to their systems in August of 2022. Hackers were able to access their customer contracts and exfiltrate customers’ personally identifiable information (PII) including names and driver’s license information.
The attackers used two compromised passwords to access the company’s network. In this case, 2.2 million individuals were affected. In October, the Milberg law firm reported filing a lawsuit against U-Haul, claiming that the company “failed to secure the personal data of its customers.”
The effects of a data breach can go beyond harming a company financially. In this case, the breach resulted in loss of customer trust and perhaps the loss of future contracts as well as stolen identity cases.
Employees Hack Meta
Meta reports firing at least a dozen workers in November after an investigation showed the employees hacked into users’ personal Facebook and Instagram accounts. The employees received thousands in payment as bribery to hack into the accounts.
The workers used ‘Oops,’ an internal tool developed by Facebook, meant to aid users in recovering their forgotten passwords. This tool is not available to the public, which is why intermediaries were needed in order to hack the accounts.
Many users took to online platforms to denounce Meta and express their concerns at their lack of privacy. “I’m shocked, shocked, to find that humans are the weakest link in a security system,” a user of the forum Slashdot said.
Hackers Seize Samsung Customer Data
In September 2022, Samsung informed their customers that a successful data beach exposed their information. The tech company assured its customers that Social Security numbers or credit card numbers were not exposed in this breach.
However, information such as their “name, contact and demographic information, date of birth, and product registration information,” could have been affected. The breach took place in July, yet Samsung updated customers about the fix and stolen data in September.
Samsung had already suffered an attack in March 2022, when hacking group Lapsus$ leaked about 190GB of sensitive data. The group, which stole Galaxy source code and “code related to highly sensitive features like biometric authentication and on-device encryption,” shared the exfiltrated data online via torrent.
The fact that this data was easily made available to the public means Samsung will have to deal with financial and proprietary losses as well as reduced customer trust. Customers are already voicing their concerns and lack of trust for the company. One user online complained, “I trusted them as their privacy policy states, ‘We maintain safeguards designed to protect personal information we obtain through the services.’”
Leaders of small and mid-size companies will notice that it took the tech giant about a month to deal with this cybersecurity incident. Therefore, it is imperative that businesses with less resources and money implement a cybersecurity program to prevent attacks. Preparation is the best defense to mitigate cyber risk.
Bottom Line
Prevention is the best weapon against cyberattacks. When you have the right tools in place, the strategy that fits your needs, and your employees know how to use this tech correctly, the likelihood of a cyber incident affecting your organization is greatly reduced.
How is your company staying secure and building defenses to avoid data breaches? Download our free Cybersecurity Checklist: How Covered is Your Business? to begin strengthening your security standing.
