Secure Data Protection
Using Secure Development Practices when Building Software
September 11, 2025
7 minute read

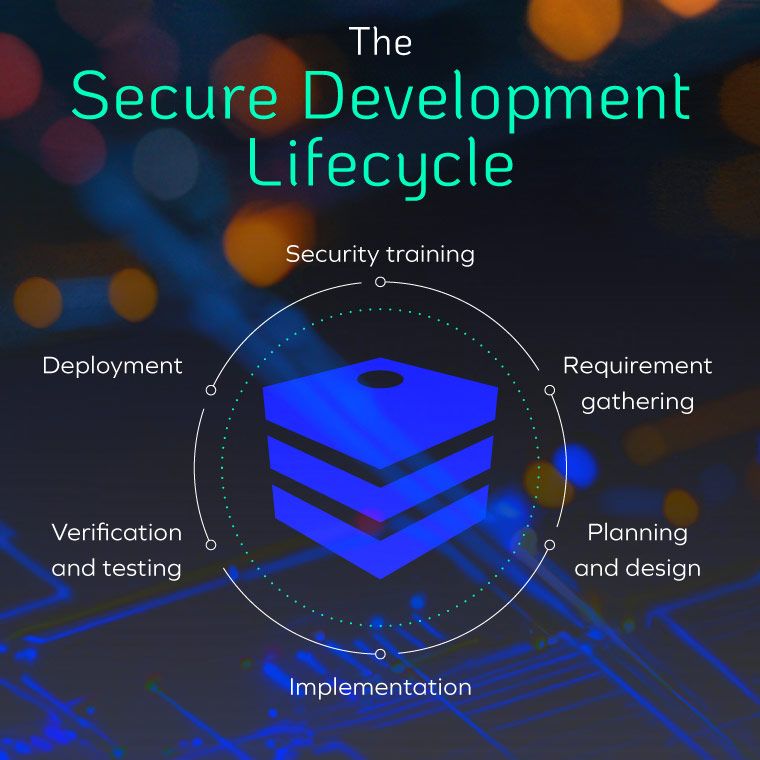
As organizations continue to onboard software to overcome everyday obstacles and optimize operations, development processes need to be pulled under the microscope. Secure development practices are becoming the gold standard as they integrate security considerations into every stage of the software development lifecycle.
Secure development is an approach to building software that prioritizes security measures throughout the entire application development process, instead of addressing security as a secondary thought post-development.
Sign up for our newsletter!
Join us below where we walk through the fundamentals of secure application development, the advantages that a security-first mindset brings to programming, and the benefits that result from building tech solutions with integrated security measures from inception to release.
If you’d like to learn more about industry best practices, the latest security tech, and the biggest headlines in the cybersecurity space, subscribe to the DOT Security blog.
The Fundamentals of Secure Application Development
Secure application development integrates security at every phase of the software development lifecycle to protect applications from vulnerabilities and threats. This comprehensive approach begins with the initial design and continues through development, testing, deployment, and maintenance.
By adopting secure development practices, organizations can mitigate risks, protect sensitive data, and ensure the integrity and reliability of their software products.
A core aspect of secure app development is threat modeling and risk assessment. This process identifies potential threats and vulnerabilities early in the development cycle, allowing developers to prioritize security and implement countermeasures. Understanding these threats leads to a security framework that prevents breaches and minimizes damage in case of an attack.
Secure coding practices reduce vulnerabilities that could be exploited by attackers. Developers must follow coding standards and guidelines that emphasize security, such as validating input to prevent injection attacks, managing memory securely to avoid buffer overflows, and using encryption to protect sensitive data.
Things like code reviews and static analysis tools can identify and rectify security flaws in the codebase, embedding security into the coding process.
Additionally, regular security testing and vulnerability management maintain application security. This includes static and dynamic analysis, penetration testing, and code reviews to identify and address security weaknesses. An effective vulnerability management program involves timely identification, assessment, and remediation of vulnerabilities.
It’s also incredibly important to continually improve security after a program is live. This means installing security patches in a timely manner and building additional defenses against new or evolving threats.
Testing Security Measures Along the Way
Testing integrated security measures throughout the development process is crucial in ensuring their functionality. By conducting security testing at each stage of development, developers can identify and address vulnerabilities early, preventing them from becoming embedded in the final product.
This proactive approach mitigates risks and reduces the likelihood of security breaches, which can lead to significant financial, legal, and reputational damage. Continuous security testing, including static code analysis, dynamic testing, and penetration testing, ensures that security measures are effective and greatly reduces the chance of new vulnerabilities.
Furthermore, integrating security testing throughout the development process bolsters the overall quality and reliability of the software.
Developing with a Security First Mindset
Developing software with a security-first mindset offers significant advantages, starting with the prevention of data breaches and cyberattacks. Prioritizing security from the outset allows developers to identify and mitigate potential vulnerabilities early, reducing the risk of costly data breaches that can result in financial losses, legal consequences, and reputational damage.
Secure coding practices and thorough security testing lead to robust applications that are less likely to experience failures or downtime due to security issues. This approach creates a stable user experience and equips the software to handle evolving security challenges with new-aged technology like AI and machine learning.
Adopting a security-first approach can also lead to long-term cost savings. Addressing security issues during development is more cost-effective than post-deployment fixes and emergency patches. Secure development practices streamline compliance with industry regulations, avoiding penalties and reducing compliance costs.
Additionally, fostering a culture of security awareness within the development team and organization as a whole greatly improves security preparedness and demonstrates a strong commitment to protecting user data and privacy.
The Benefits of Integrated Security in Software Development
Integrated security in software development brings numerous advantages, beginning with the facilitation of a smoother development process. By incorporating security measures from the start, developers can create a more predictable and manageable workflow, identifying and mitigating potential issues before they escalate.
This preemptive strategy reduces the need for more work later on in the development cycle, allowing teams to work with tighter timelines. Moreover, making security an integral part of the development process encourages a collaborative environment where security experts, developers, and other stakeholders work together to achieve the common goal of building secure and reliable software.
Another significant benefit stems from establishing user confidence and trust. When security is built into the core of the software, it signals to users that their data and privacy are prioritized and protected. This assurance can be a critical differentiator in competitive markets, where consumers are increasingly concerned about data security.
All-in-all, this additional consumer trust results in higher user satisfaction and loyalty. Plus, these security measures reduce expected downtime, which only further adds to user perception of reliability, ultimately leading to sustained business success and a stronger market position.
The Role of Secure Development in the Era of Vibe Coding
"Vibe coding", a term gaining traction among developers who prioritize flow, intuition, and rapid iteration, has reshaped how teams approach software creation. It celebrates creativity and speed, often favoring minimal process over rigid structure.
As this style becomes more prevalent, integrating security early and seamlessly is more important than ever.
Secure development isn’t just a checklist, it’s a mindset. In the vibe coding era, where spontaneity and experimentation thrive, secure practices can empower innovation by:
- Embedding guardrails that allow developers to move fast without breaking things.
- Automating security checks within CI/CD pipelines to catch vulnerabilities before they ship.
- Using lightweight threat modeling to anticipate risks without bogging down creativity.
- Encouraging secure defaults in frameworks and libraries to reduce friction.
Security needs to be frictionless, intuitive, and aligned with the developer experience. That means tools should integrate naturally into existing workflows, and security education should be practical, not prescriptive.
When developers are equipped with the right resources and autonomy, secure coding becomes a natural extension of their craft, not a separate concern.
As organizations embrace vibe coding, the challenge is to build environments where speed and safety coexist. That starts with culture, continues with tooling, and succeeds when developers feel empowered—not policed—by secure development practices.
Final Thoughts on Secure Development Best Practices
By prioritizing security measures throughout the entire development process, the software and applications your organization relies on will be put in a better position to avoid and mitigate cyber threats. Additionally, applications with integrated security measures provide a better user experience, better performance, and more privacy.
Adopting software that is built from the ground up with a security-first mindset adds another component to your overall network security strategy, effectively strengthening your layered cybersecurity strategy.
If you’re looking for a way to stay on top of everything in the cybersecurity space, subscribe to the DOT Security blog for everything from coverage on major monthly headlines to detailed walkthroughs of the latest philosophies guiding the industry.
