Cybersecurity Consulting
What Is the Cost of Downtime Due to a Breach?
July 22, 2025
8 minute read

While businesses champion causes, spur innovations, and change industries, at the end of the day, businesses aim to make money. But downtime due to a breach directly impacts the bottom line. Let’s look at how much downtime can actually cost a company hit by a cyberattack.
For instance, the massive AT&T outage that occurred in early 2024 cost the telecommunications company at least $375 million just in customer refunds and reimbursements. This doesn’t even take into account the money spent on recovering systems or bringing operations back online.
Sign up for our newsletter!
The initial costs of downtime include lost revenue, the expenses involved in bringing systems back online, and labor expenses. But the total cost of downtime also accounts for the long-term impact of a cyber incident. The long-term effects can include customer loss, damage to your brand reputation, and diminishing trust with your target consumer.
If you’re looking to put your strategy to the test, check out DOT Security’s Cybersecurity Checklist: How Covered Is Your Business? and find out if your current defenses are up to par with the current industry standards and best practices.
The Actual Costs of Breach-Related Downtime
These costs result from a business being unable to make sales, tend to customer service tickets, process orders, collect data, and handle other critical operational processes.
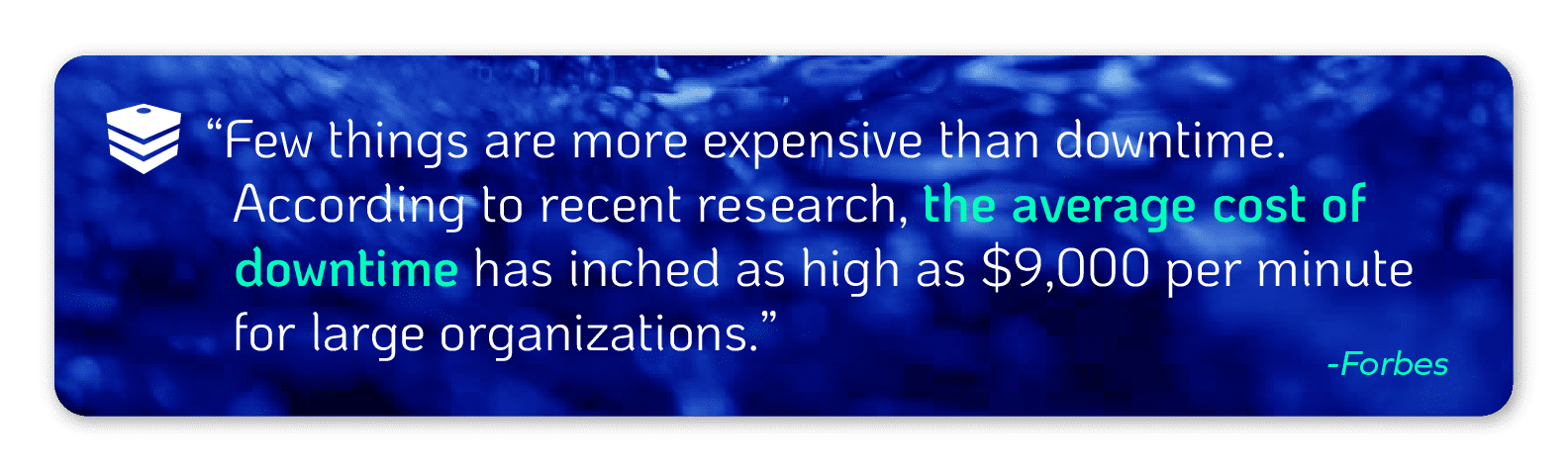
“The cost of a network, website or service being down or unavailable can be probative. The average cost of downtime across all industries has historically been about $5,600 per minute, but recent studies have shown this cost has grown to about $9,000 per minute.”
Additionally, there are many “hidden” costs of downtime due to a cybersecurity breach (as opposed to a natural disaster or other event) that can affect businesses across many industries, including:
- Increased cyber insurance premiums
- Drops in credit rating
- Reputational harm to your brand
Breaking Down the Cost of Downtime
The cost of downtime is calculated by discovering and adding up five key numbers:
- Lost revenue: The amount of money that would have been made without operational systems going offline.
- Lost productivity: The labor costs of your teams being unable to perform their work.
- Recovery costs: The amount of money it costs to restore your systems (labor, technology, and time).
- Cost of reputational harm: If you collect consumer data, then you’re being entrusted to protect this information from cybercriminals. When data is stolen or lost, it severely impacts that trust. The cost of this comes in the form of harm to your company’s reputation and the lost ability of the public to trust your brand.
- Customer Loss: In addition to the damage a breach can cause to the reputation of your brand, these breaches can also influence current and potential customers to choose a direct competitor.
These breach-related costs vary depending on the depth of the cyberattack and the resilience of the company in question. Companies with a more robust cybersecurity strategy in place prior to an incident occurring will likely have lower costs on average than those who lack these protections.
How to Estimate the Cost of Downtime
By taking averages based on your company’s size, you can roughly calculate the cost of downtime for your organization.
Adding your lost hourly revenue to your hourly expenses for labor, you can get a rough idea of how much downtime would cost per hour.
Keep in mind, though, that recovery costs and reputational harm cannot be accurately predicted due to being heavily reliant on the situation. Some breaches are easily fixed, some take more time, and some will have worse outcomes for customers resulting in greater backlash.
- Data Loss: Modern companies run on data, much of which is stored digitally via the cloud. Cybercriminals know this and will target your data centers to delete, steal, or block you from accessing yours. Can you go hours, days, or weeks without access to up-to-date data?
- Loss of Key Systems: Some cyberattacks will take down key systems, locking your teams out of the technology they need to do work, like email clients, word processors, or other software. This lost labor cost adds up quickly, especially if the attack is widespread. These attacks can completely take down systems, or block access them by altering credentials.
- Stolen Data: Consumer trust in businesses to protect their information is already low—only 21% of people trust brands to keep their data secure. So, when a customer entrusts it to you, it’s an important opportunity, and breaking that trust often makes it impossible to regain. Having strong cybersecurity in place displays your dedication to keeping information safe and secure.
How to Avoid Downtime with Cybersecurity
The best way to avoid costly downtime is to have cybersecurity systems in place to mitigate the risks. These systems range from preventative measures like next-gen antivirus, spam filters, and employee training, to reactive measures like backup and recovery tools.
Here’s a deeper look at each security measure and how they help prevent downtime:
- Backup and Recovery: When disaster strikes and key business systems are compromised, getting back up and running is the most important thing you can do. That’s why it’s critical to have a backup and disaster recovery plan to restart key systems, restore lost data, and get your business operating again.
- Training: The human element of your business is a very common target for cybercriminals with social engineering attacks like phishing and whale phishing. They hope to get people to click on malicious links, expose login credentials, or download dangerous attachments or files. Additionally, it’s important for your teams to understand what to do when an incident occurs.
- Next-Gen Antivirus: Using a combination of new technologies, next-gen antivirus is a necessary layer of a modern cybersecurity strategy that focuses on stopping malicious code from entering your network. It works by scanning everything coming in and seeking out abnormalities that may point toward cybercriminal activity like viruses.
- Network Monitoring: Monitoring your business network and security systems ensures everything is working as intended so that your business is successfully able to mitigate the risks of downtime in the event of an incident. Network security monitoring also helps identify threats quickly to minimize the damage they can do.
- Security Audit: With an expert-led security audit, a team of cybersecurity specialists will comb through your business processes, technology, network, and security strategy to determine where your weaknesses lie. The team of analysts, engineers, developers, and vCISOs will take that information and build a customized security strategy to secure your weak points.
The Benefit of a Layered Cybersecurity Strategy
Downtime from cyberattacks doesn’t just disrupt—it drains productivity, revenue, and trust. A layered cybersecurity strategy helps prevent that by building in multiple lines of defense that work together to keep systems online and threats contained.
Instead of relying on a single tool or barrier, this approach combines firewalls, endpoint protection, access controls, and real-time monitoring. Each layer is designed to catch what the others might miss. If malware gets through one checkpoint, another is ready to stop it before it spreads.
This redundancy is what keeps minor incidents from turning into major outages. It limits the blast radius of an attack, shortens recovery time, and helps teams stay focused on their work instead of scrambling to respond.
For organizations that can’t afford to go dark, even briefly, layered security is more than a best practice. Cybersecurity isn’t just about having a strong firewall or a clever password policy—it’s about building a resilient, multi-tiered defense that can adapt to evolving threats. That’s where a layered cybersecurity strategy comes in.
Using AI to Predict and Avoid Downtime
Whether it’s a manufacturing line grinding to a halt or a service outage that frustrates customers, unplanned downtime can damage both revenue and reputation. But with AI, businesses can shift from reactive to predictive.
In manufacturing and IT environments, predictive models are already helping teams schedule maintenance more strategically. Instead of relying on fixed service intervals or reacting to breakdowns, they’re using real-time insights to prioritize what needs attention—and when. That means fewer surprises, fewer emergency repairs, and less time spent offline.
The same approach is showing up in cybersecurity. AI systems trained on network behavior can detect unusual activity and isolate threats before they spread. It’s not just about stopping attacks—it’s about keeping systems stable and available, even under pressure.
Done right, AI doesn’t replace human judgment. It supports it. It gives teams better information, earlier in the process, so they can make smarter decisions and keep things running.
Final Thoughts on Downtime Costs
Downtime is costly. Not only do you have to deal with the actual costs of lost data and disrupted operations, but you also must use resources to get systems back online, restore data, isolate and neutralize the cause of the incident, and handle any public backlash and consumer disapproval that comes with being breached.
With a proactive and comprehensive cybersecurity systems in place that includes measures like network monitoring, next-gen antivirus, consistent security audits, awareness training, and backup and recovery plans—you can minimize the amount of downtime you experience in any given year, and substantially improve your ability to avoid, defend against, and respond to security threats that emerge.
If you want to know how complete your current strategy is, or where it can be improved, take a minute and look over DOT Security’s Cybersecurity Checklist: How Covered Is Your Business?
