Endpoint Protection
SIM Swapping: How Hackers Beat Multi-Factor Authentication
February 29, 2024
8 minute read

Everybody who works in a security-aware organization, or who has taken steps to protect their private accounts, has been told that multi-factor authentication (MFA) is an important layer of security.
While MFA absolutely is important for security, SIM swapping attacks have put text message-based MFA in jeopardy by intercepting the authentication codes and exposing your accounts.
Sign up for our newsletter!
Learn more about how SIM swapping attacks work, how to protect yourself against them, and some additional ways to secure your accounts aside from short message service (SMS, also known as text) codes below.
Another important part of cybersecurity is making sure you’re covered from every possible angle. Download DOT Security’s checklist, How Covered is Your Business? to uncover your vulnerabilities and ensure you're protected from all kinds of attacks.
What Is a Sim Swapping Attack?
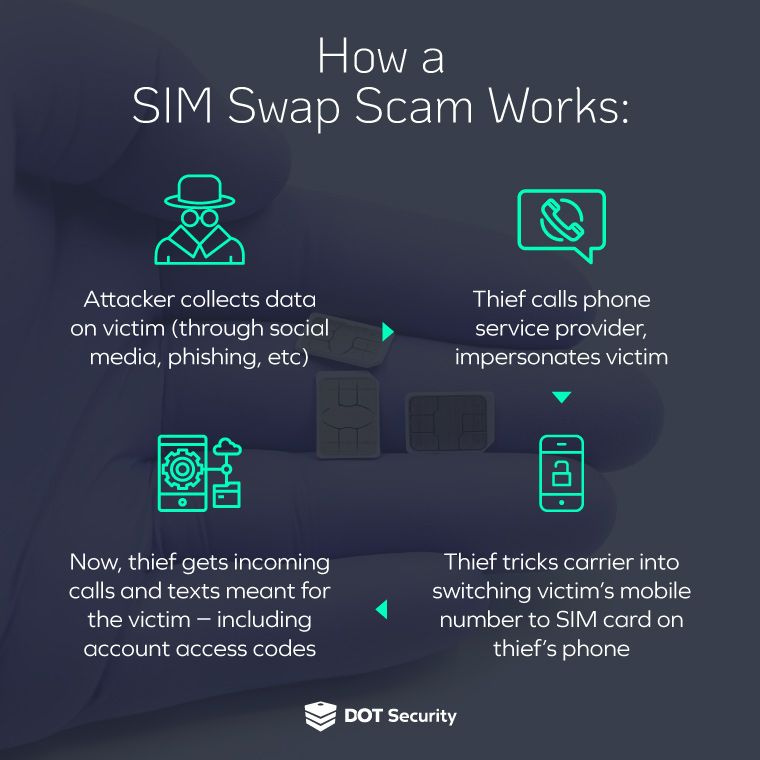
SIM swapping (also known as SIM jacking or SIM hijacking) is a type of cyberattack where an attacker transfers the victim’s phone number to a SIM card under the attacker’s control.
This is typically done in two ways:
- ”Convincing” the carrier to make the transfer. This involves the attacker using social engineering tactics (faking credentials and information) to trick customer service representatives.
- It can also be done by exploiting security vulnerabilities within the carrier’s system. After getting in, the attacker can then make the transfer themself.
Once the attacker has control of the victim's phone number, they can intercept incoming calls and messages, including those used for multi-factor authentication (MFA) or password recovery.
This means that the attacker can get access to accounts that were thought to be secure like email, social media, banking, crypto wallets, and any other accounts that might have sensitive or valuable information to steal.
How to Protect Against SIM Swapping
To protect against SIM swapping attacks, you should work on improving a few key areas of your cybersecurity:
-
Your Passwords— Having strong, unique passwords for all your accounts is a big first step toward stopping cyberattacks. Use a password management tool to keep track of passwords and generate stronger ones.
-
Your Cybersecurity Awareness— A major way to avoid falling victim to a successful SIM swapping attack is to be aware of the signs. One aspect of these attacks is information gathering, so be aware of any unusual emails asking for info and avoid interacting with them. Additionally, watch for strange activity within your digital assets and accounts like odd transactions, posts, or communications.
-
Your Security Policies— For businesses, it’s worth establishing or updating the universal cybersecurity policies of your organization. Make sure people know how to properly manage their passwords, how to report a potential attack (who to call, what to say, when to report, etc.), and general safety guidelines to follow.
-
How You Use MFA— Because SMS-based MFA can be exploited using SIM swapping attacks, it’s advised that you or your organization use other MFA techniques like biometrics (fingerprints, face scans, etc.) or third-party security applications like authenticator apps from Microsoft or Google. Using devices, like USB authenticators, is also an option.
-
Device Protection— Protecting your endpoints (devices connected to your network) and adding a layer of security to them stops attacks from reaching other critical parts of your network.
Know the Signs of a SIM Swapping Attack
If you do become the victim of a SIM swapping attack, it can be difficult to know because the signs tend to be subtle. Here’s what to look out for:
-
Strange Service Notifications— If you get notifications from your carrier that a swap has been requested or that there’s been a change to your service, call them immediately to get the details.
-
Interrupted Phone Service— If your phone abruptly loses service—rendering it unable to make or receive calls or texts, or lacking data service when expected—it's possible that the SIM card has been deactivated and potentially swapped.
-
Unusual Social Media Activity— Noticing strange posts popping up on your own socials? It could be that a SIM swapping attacker has taken over your accounts.
-
Account Lockouts— If you suddenly lose access to many of your important accounts, it might suggest a SIM swap attack.
-
Suspicious Transactions— Scammers executing SIM swaps may discreetly conduct transactions using the financial accounts linked to a phone number. Unusual transactions appearing on bank or credit card statements could indicate potential SIM swapping activity.
What to Do if You Fall Victim to a SIM Swap
If you believe you’ve fallen victim to a SIM swapping attack, the first thing you should do is call your provider and attempt to end the attacker’s access to your phone number. Your carrier probably can’t help you catch the actual person(s) responsible, but at least you can end their ability to intercept your communications.
Next, do the same thing but with your financial accounts (and any other important accounts that you want to protect) to let them know about the attack and to potentially freeze accounts if needed.
Other than taking control of your most important accounts and dealing with your carrier, you need to change the passwords in your accounts and disable MFA to keep the attacker from locking you out of any other accounts. Consider also re-establishing MFA with a non-SMS option once you regain control of your number.
Key Takeaways on SIM Swapping Attacks
- SIM swapping bypasses multi-factor authentication, posing a grave cybersecurity threat.
- Attackers exploit carrier system flaws or social engineering to hijack phone numbers.
- Protect against SIM swapping with strong passwords and heightened cybersecurity awareness.
- Implement alternative MFA methods like biometrics or authenticator apps.
- Monitor for signs of an attack: strange service notifications, interrupted phone service, unusual social media activity, account lockouts, and suspicious transactions.
- In case of an attack, immediately contact carriers and financial institutions, change passwords, and reconfigure MFA settings to mitigate damage swiftly.
Wrapping Up on SIM Swapping
SIM swapping jeopardizes multi-factor authentication by using social engineering to exploit phone number vulnerabilities. Preventing these kinds of attacks hinges on organization-wide security policies that help people create and manage robust passwords, increase their security awareness, and use alternative MFA methods.
Detecting signs like service disruptions and suspicious activity is crucial. Swift action, including contacting carriers and financial institutions, is imperative, if victimized, to mitigate damage promptly.
Like with SIM swapping, cybercriminals have so many angles to take when attacking people and businesses that it’s hard to ensure they’re all covered. Download and use DOT Security’s checklist, How Covered is Your Business? to identify your vulnerabilities and protect your business from all kinds of threats.
