Cybersecurity Consulting
What Do You Need to Build an In-House Cybersecurity Team?
October 19, 2022
9 minutes
A cybersecurity team is a must-have for businesses to protect themselves, their data, and their customers. But building one from scratch requires a lot of time, money, and expertise, and most people simply don’t know how to get started.
In this blog, we cover what’s necessary to start building an in-house cybersecurity team and some additional options that organizations have to stay secure.
Sign up for our newsletter!
The Resources, Expertise, and Technology Needed for an In-House Cybersecurity Team
From money to time to technology, a cybersecurity team needs resources to grow and become effective at protecting you against modern cyberthreats. Here’s a look at some key areas and what’s needed to build an in-house cybersecurity team.
Necessary Cybersecurity Resources
The first thing you need to establish is the amount of resources you’re willing to dedicate to building your cybersecurity program. This means financial investment (salaries, recruiting, technology, etc.), getting buy-in from the rest of your organization, establishing necessary infrastructure, and more.

Let’s break it down into those key areas and discuss what each means for an organization:
-
Financial Investment: This is oftentimes the most daunting aspect of building a full in-house cyber team. First off, it’s a major cost: for mid-sized businesses, the hardware cost can easily get near $50,000 for just the essentials. Next, you need to hire engineers, analysts, technicians, and other specialists to operate the technology and monitor your network for threats. Salaries, benefits, and recruiting costs (cybersecurity professionals are in very high demand). Combine salaries, benefits, recruiting costs, and retention costs and it becomes a large investment, not to mention the time investment needed in recruiting, also. All in all, it can cost businesses anywhere from multiple hundreds of thousands of dollars to nearly $1 million a yearto staff and maintain an effective cybersecurity team.
-
Time Investment: In addition to the financial investment needed, it will also take time to acquire hardware and software, recruit talent, and build the necessary facilities and infrastructure. Often, this can take months to years depending on how big of a team you’re building and how much you’ve already done to prepare. Additionally, consider the time commitment necessary to retain talent and find replacements when people leave.
-
Buy-In from Your Organization: Security can only work if everyone is ready to buy-in from the top to the bottom. Be sure you have the ability to build processes and procedures and ensure everyone will follow them. This may mean implementing training to help non-security staff become familiar with new procedures and to help them follow all guidelines and be aware of potential security risks.
What Expertise Should You Look For?
Next, you need to establish which kinds of expertise you’ll need to secure your business. There are a lot of highly specialized roles in cybersecurity and which ones you require depends heavily on your business, your industry, and your specific needs.
Here are some, but definitely not all, key roles that will be necessary for your in-house team:
-
Cybersecurity Engineer: An engineer helps implement security solutions and ensures everything can coexist seamlessly with your existing technology.
-
Cybersecurity Analyst: A security analyst monitors your network for threats, helps to identify them, and works to improve your network security over time.
-
Compliance Officer: If you need to become compliant with any government regulations, an expert compliance officer will know everything you must do and keep on top of any changes.
In addition to these members of your team, there are some major cybersecurity abilities your team needs to be able to do in order to build a strong security posture. To decide which ones to prioritize, you need to look internally at your business and ask key questions like:
-
Do you have a lot of connected devices?
-
How much of your workforce is remote or off-site?
-
What types of information do you frequently transfer, access, or collect?
-
Does your business require any form of compliance with government regulations?
The answers to these questions will vary, but they’ll help you decide which areas of cybersecurity to prioritize, especially if you’ve realized that you can’t allocate enough resources to cover every base. For example, if you work with the Department of Defense frequently (or hope to in the future), you should prioritize CMMC compliance and hire compliance officers to help you achieve and maintain it.
If you have a hybrid or fully remote team, endpoint protection might become a focus.
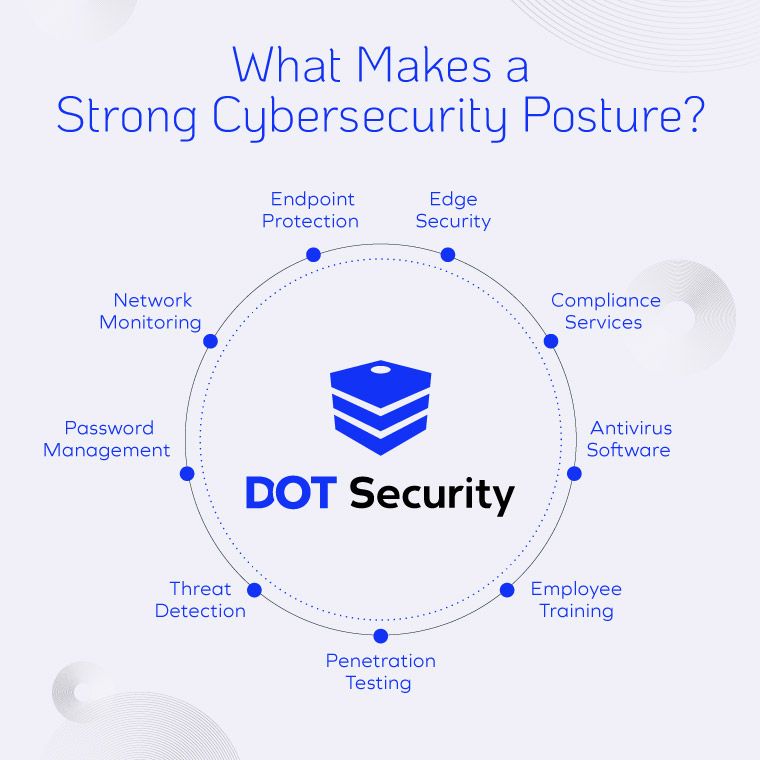
Ideally, you should build a security program that effectively implements every layer of a strong cybersecurity posture. Without them all, you’re leaving your business vulnerable in different ways which can be hard to keep track of and leave holes wide open for cybercriminals to take advantage of.
Get the Right Technology
Your security team needs the right tools to get the job done. This means acquiring the technologies necessary to see their vision become reality when it comes to building your security strategy. You'll need to invest in things like next-gen antivirus software and firewalls for proactive security, tools to secure devices, software to use organization-wide like password managers and multi-factor authentication, and more.
Related: Reactive and Proactive Cybersecurity Measures You Can Implement Now
These all come with an obvious financial cost, but it also takes time and expertise to pick out the right options for you and to train people on how to effectively use them.
Outsourcing Options for a Cybersecurity Team
For businesses with small or non-existent IT or security teams, starting from scratch can seem like a large mountain to climb. Even businesses that have an established IT department must make many additional investments of both time and money to build a cybersecurity team worth its salt.
Luckily, options beyond building everything from the ground up exist for businesses of all sizes. Outsourcing your cybersecurity needs can be a cost and time-effective option that gives you faster access to the expertise, technology, and experience you need to stay secure in a world of modern, evolving cyberthreats.
Related: 5 Qualities of a Reliable Cybersecurity Company
A managed security services provider (MSSP) will have fully built out teams of engineers, analysts, vCISOs, developers, penetration testers, compliance officers, and many other specialists, along with all the top-of-the-line equipment, technology, tools, and facilities necessary.
Partnering with an MSSP, oftentimes, gets you more for less. You don’t have to worry about recruiting talent only for them to leave, managing teams around vacations and sick days, or replacing outdated technology. All of this is handled by our team.
What to Look for in an MSSP
When partnering with an MSSP, it’s important that you make sure they have everything you need and the most up-to-date technology available. Here’s a quick rundown of things to note when searching:
-
Do they have a security operations center (SOC)?
-
Is there a dedicated compliance team?
-
What certifications do they have?
-
What is their process? (For example, DOT Security starts with an assessment of your current security landscape)
-
Do they have the specialists you need for security success?
Related: MSSP Security Operations Center Explained
In Conclusion
Building a cybersecurity team from scratch is a mighty endeavor that costs a lot of time, money, and other resources to get off the ground. Many businesses simply don’t have what’s needed to get it done and risk becoming vulnerable to cyberattacks simply due to the immense task of building a security posture.
If you think partnering with an MSSP is the right move or want to learn more about what that kind of partnership looks like, check out the blog, MSP Partners: What to Expect, to explore the benefits of managed cybersecurity services.
