Network Security Monitoring
What Is Attack Surface Management?
December 12, 2024
7 minute read

Think about your organization like it’s a castle. Then, imagine that the moat, drawbridge, castle walls, and other defenses are the layered cybersecurity strategy. To defend the castle, you need to be prepared for an attack from any angle. Attack surface management (ASM) is the guards monitoring the entire castle and keeping an eye on every possible point of attack.
By embracing attack surface management as part of your overarching cybersecurity strategy, you’re increasing the amount of visibility you have over your defenses, putting you in a better position to identify and mitigate threats.
Sign up for our newsletter!
There are five core components to attack surface management that work together so you have the best chance possible to halt, mitigate, or recover from cyberattack fallout.
The five core aspects of attack surface management include:
1. Discover
2. Map
3. Prioritize
4. Contextualize
5. Remediate
Every business faces a different level of cyber risk and should create security strategies that match their total risk factor. Get a DOT Security risk assessment scheduled today to gain a better understanding of your current cybersecurity posture and how it measures up.
What Is an Attack Surface?
Before exploring the five different components of attack surface management individually, it’s important to understand exactly what an attack surface is in the context of cybersecurity. Understanding the attack surface is crucial for identifying and assessing potential risks, vulnerabilities, and weak points that could be exploited by attackers.
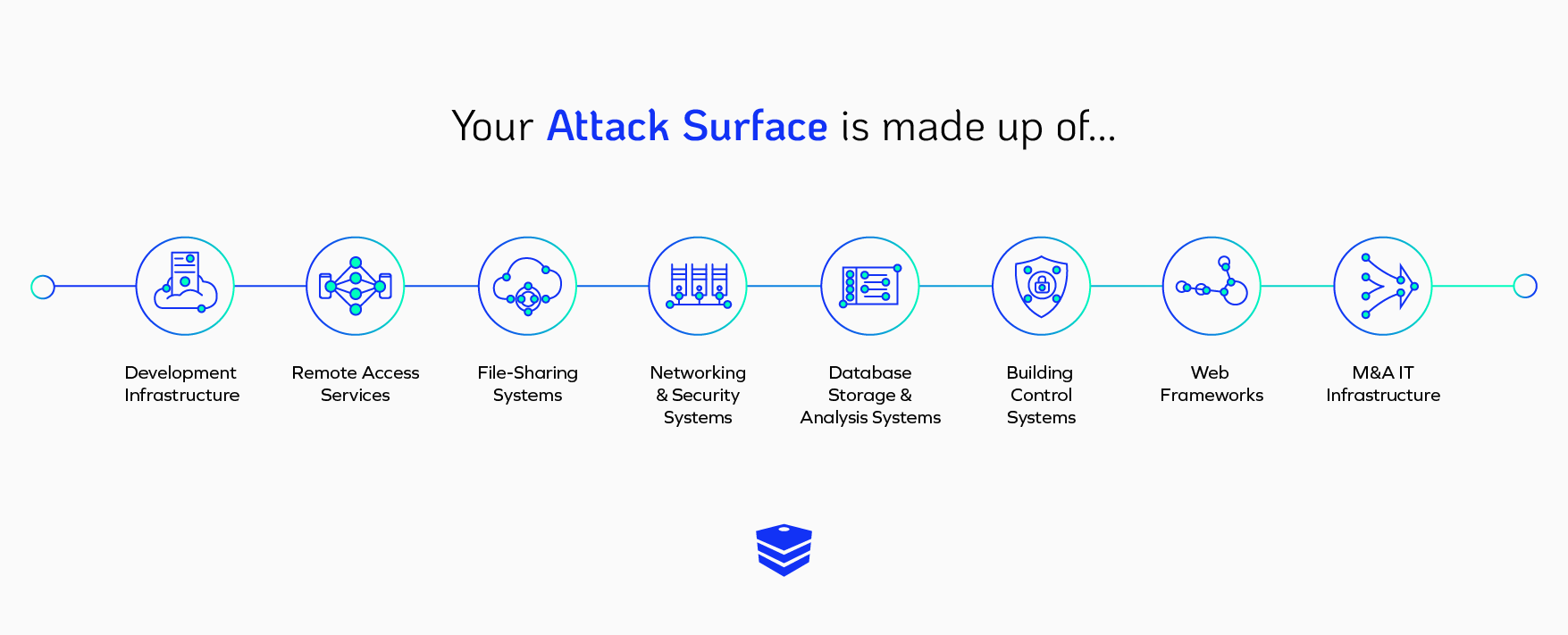
An attack surface encompasses each and every potential entry point and vulnerability within an organization’s digital and physical structure that could be targeted by malicious actors seeking unauthorized access.
This includes, but is not limited to, hardware components like servers and network devices, software applications, operating systems, web interfaces, databases, APIs, and even employee-managed elements such as user account credentials.
This shows how the modern attack surface grows and evolves alongside technology, system configurations, and organizational practices, so it’s vital to identify the scope and size of yours. As technology ecosystems expand and become more interconnected, the attack surface grows, creating more vulnerabilities that cyberattacks can exploit.
By minimizing the attack surface and addressing identified vulnerabilities, however, organizations can enhance their overall cybersecurity posture, reduce the likelihood of successful cyberattacks, and better protect their sensitive information and critical systems.
Attack Surfaces are Expanding
The rapid expansion of attack surfaces in recent years can be attributed to the explosive growth of connected devices and the increasing complexity of IT ecosystems. The rise of the Internet of Things (IoT) has introduced billions of devices, from smart appliances to industrial sensors, all of which connect to networks but often lack robust security measures.
Similarly, the major shift to hybrid work environments has decentralized IT infrastructure, with employees accessing sensitive data from personal devices and unsecured networks. Each new device, cloud service, or remote connection adds potential entry points for cybercriminals, widening the attack surface significantly.
Compounding the issue is the accelerating pace of digital transformation. Organizations are adopting cloud computing, artificial intelligence, and microservices architectures to stay competitive, but these innovations come with their own security challenges.
Cloud environments, for example, can be misconfigured or poorly monitored, making them a lucrative target. Meanwhile, legacy systems often remain in use alongside cutting-edge technologies, creating gaps and vulnerabilities.
Together, these trends create a sprawling, ever-changing attack surface that needs just as sophisticated cybersecurity measures to combat.
How Attack Surface Management Works
Attack surface management works to increase the strength of your cybersecurity strategy by increasing your total visibility over your entire attack surface, both internally and externally. This includes entry points, existing vulnerabilities, and other attack avenues that cyberattacks target.
ASM begins with a discovery phase that combs through your full tech stack, top to bottom, in order to identify any assets that add to the overall attack surface. Once identified, these assets are then mapped out, giving you a detailed view of your exposure and risk levels.
By increasing the total visibility you have over your attack surface, you can create a stronger cybersecurity strategy with tailored defense tactics that meet the needs of your specific organization.
ASM provides you with more oversight so you can be more intentional in creating an effective and comprehensive cybersecurity strategy.
The following sections explore each phase of ASM in much more detail.
The 5 Main Functions of Attack Surface Management
Now that we’ve defined an attack surface and have a general idea of how ASM operates, let’s take a closer look at the five main functions included in the attack surface management arsenal.
1. Discover
The discovery phase in attack surface management involves a systematic and exhaustive process in which all assets contributing to the organization’s attack surface are identified. This accounts for internal assets like servers, databases, workstations, and external assets such as web applications and cloud resources.
Automated tools, network scans, and manual assessments are employed to create a comprehensive inventory. This step is crucial for uncovering potential blind spots in the security posture, ensuring that no asset is neglected or without visibility. The discovery phase lays the foundation for cybersecurity improvements by cataloging and defining the full attack surface and associated vulnerabilities.
2. Map
Once assets are discovered, the mapping phase details the layout of the network including system relationships, network connections, and hardware locations. This all helps you understand how different components interact, communicate, and share data.
Not only is this map helpful for your cybersecurity strategy, but it will also help you better understand the way data flows through your organization.
Visualization tools are often employed to illustrate the connections between servers, databases, applications, and users. All-in-all, this mapping aids in understanding the potential attack paths and also assists cybersecurity teams in predicting the potential impact of a security incident. A comprehensive network map enhances the organization's ability to respond effectively and rapidly to cybersecurity threats.
3. Contextualize
Contextualization is the process of integrating threat intelligence into the ASM framework. Threat intelligence provides real-time information on current and emerging cyberthreats, including tactics, techniques, and procedures employed by malicious actors.
By incorporating this intelligence into the decision-making process, security teams can contextualize vulnerabilities within the broader scope of the entire network. This dynamic awareness enables organizations to adapt their security measures in response to evolving threats, enhancing the agility and effectiveness of their security posture.
4. Prioritize
The prioritize function involves evaluating the criticality and risks associated with each asset identified across the attack surface. Cybersecurity teams use risk assessment methodologies that consider factors such as the asset's importance to the business, the sensitivity of the data it handles, and the potential impact of a security breach.
By assigning risk-level priorities, organizations can allocate resources more effectively. Prioritization ensures that cybersecurity tactics are focused on addressing the most critical vulnerabilities first, enhancing the resilience of the organization as a whole.
While prioritization helps you allocate time, expertise, and resources to those vulnerabilities that need them most, it’s also important to note that without proper network segmentation, a malicious actor may be able to infiltrate critical and sensitive systems through lateral movements after gaining access to a less secure entry point.
This further demonstrates how different cybersecurity tactics work together to provide you with a comprehensive defense strategy that gives your network the protection it needs.
5. Remediate
The remediate function is the proactive step of addressing vulnerabilities and risks identified within the attack surface. Once prioritized, security teams deploy remediation strategies, which may include applying software patches, updating configurations, or implementing additional security controls.
The goal is to reduce the attack surface's overall risk exposure and fortify the organization's defenses. Remediation is an ongoing process, reflecting the continuous cycle of identifying and addressing vulnerabilities in the ever-changing cybersecurity landscape.
Wrapping Up on Attack Surface Management
By folding attack surface management into your overarching cybersecurity strategy, you’ll have more visibility, and in turn, more control over the security of your entire network. Through discovery, mapping, contextualization, prioritization, and remediation, ASM practices work together to reduce risk and give you deeper insights into existing vulnerabilities that need addressing.
Attack surface management takes your security visibility far beyond the front gate and helps you establish a full 360-degree cybersecurity strategy.
Mitigating risk often begins with understanding risk. Learn about your organization’s position with DOT Security’s risk assessment designed to define and detail your overall risk factor so you can start working toward a more secure tomorrow, today.
