Network Security Monitoring
What Are Threat Hunting Tools in Cybersecurity?
June 03, 2025
10 minute read

Creating a comprehensive cybersecurity strategy requires the right combination of processes, experts, and sophisticated technology. One type of technology is threat hunting. Threat hunting in cybersecurity involves the discovery, identification, and archiving of previously unknown or unmitigated cyberattacks.
Threat hunting is an important process in cybersecurity because cybercriminals are constantly churning out new cyberattack variants, launching brand new cyberattacks powered by sophisticated technology like artificial intelligence, and targeting new vulnerabilities.
Sign up for our newsletter!
By implementing a powerful threat hunting tool into your cybersecurity strategy, you significantly reduce your chances of being hit by a cyberattack.
Recognizing and avoiding threats is the bread and butter of threat hunting tools. However, employee training and awareness is also a crucial factor in identifying and preventing threats. Check out DOT Security’s 6 Things to Look Out for to Avoid Phishing Scams to learn about the telltale signs of a phishing scam.
Defining Threat Hunting
Threat hunting in cybersecurity is a proactive approach wherein cybersecurity experts use sophisticated tools to identify emerging threats that have yet to be seen or logged by automated solutions and often have no preexisting defense.
Unlike traditional methods that rely on automated systems to detect and respond to threats, threat hunting involves human analysts who use a combination of manual techniques, threat intelligence, and behavioral analysis to uncover malicious activities that might go unnoticed.
This process often includes examining unusual patterns, anomalies, and indicators of compromise (IOCs) within an organization's network and systems.
The goal of threat hunting is to discover advanced persistent threats (APTs), zero-day vulnerabilities, and sophisticated attacks that automated defenses might miss. By continuously seeking out hidden threats, threat hunters can enhance an organization's security posture, reduce dwell time (the duration a threat remains undetected), and prevent potential damage from undetected attacks.
This proactive stance not only helps in identifying current threats but also in improving overall security strategies and defenses.
How Threat Hunting Works
Threat hunting works through a systematic and proactive approach to identify and mitigate potential threats that have bypassed automated security defenses.
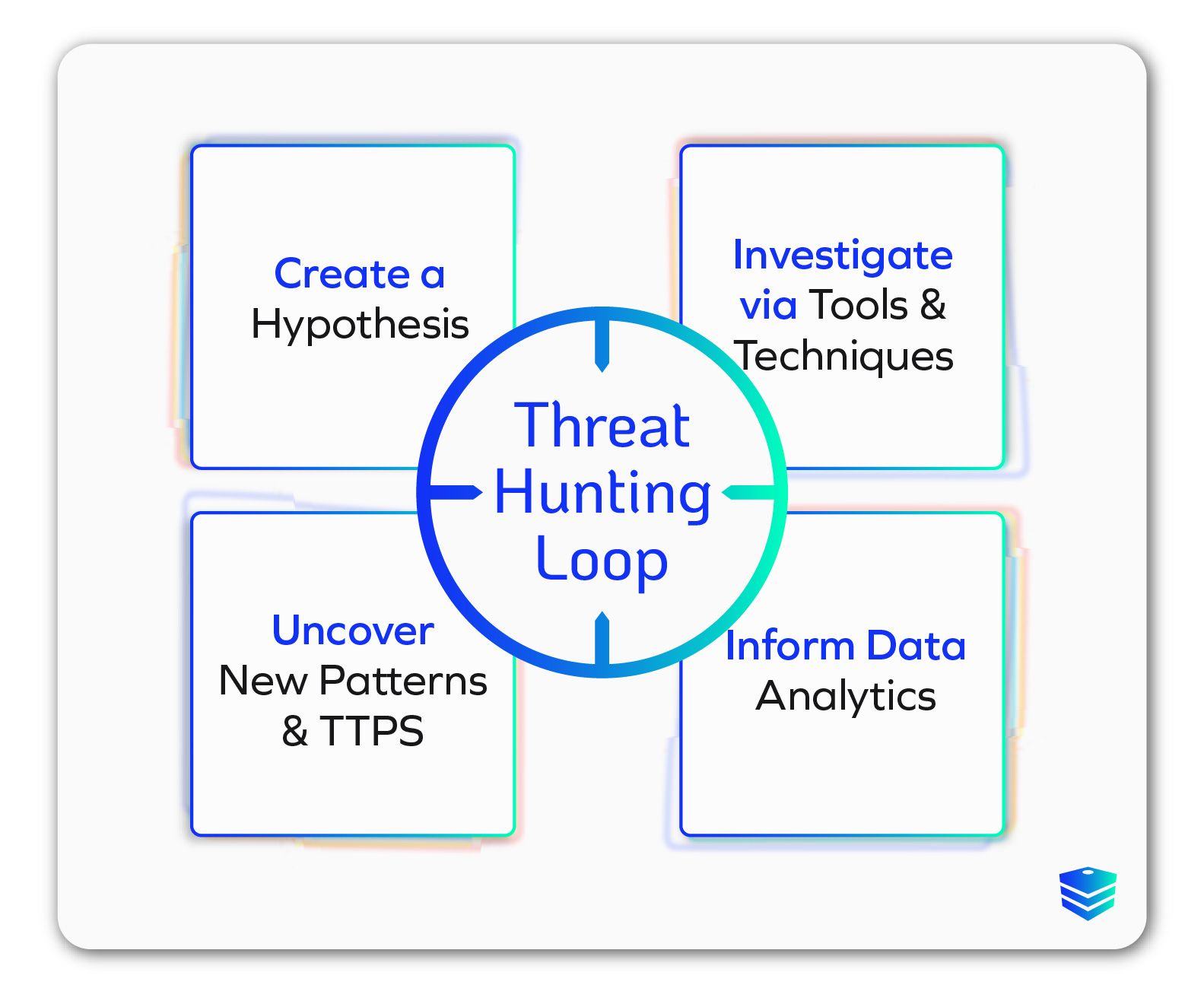
The process begins with hypothesis generation, where threat hunters—using their expertise and threat intelligence—formulate assumptions about possible threats based on the organization's environment and known attack vectors. These hypotheses guide the investigation and help to focus efforts on specific areas of interest.
Next, threat hunters collect and analyze data from various sources, such as network logs, endpoint telemetry, and threat intelligence feeds.
This data is scrutinized for IOCs and unusual patterns or behaviors that may suggest malicious activity. Advanced tools and techniques, including machine learning, behavioral analysis, and forensic analysis, help detect anomalies and patterns that signify potential threats.
Once a potential threat is identified, threat hunters validate their findings through detailed analysis and cross-referencing additional data sources. This involves dissecting the malicious activity to understand its nature, scope, and impact. Upon confirmation, threat hunters take steps to contain and eradicate the threat, often collaborating with incident response teams.
The insights gained from threat hunting activities are then fed back into the security infrastructure, improving detection capabilities, refining security policies, and enhancing overall threat intelligence.
In essence, threat hunting is an ongoing, iterative process that leverages human expertise, advanced analytics, and a deep understanding of the threat landscape to proactively identify and neutralize security threats before they can cause significant harm.
Types of Threat Hunting
Before you can implement a threat hunting process into your cybersecurity strategy, it’s important to understand the different types of threat hunting that you can lean on. The three main types of threat hunting are structured threat hunting, unstructured threat hunting, and situational or entity-driven threat hunting.
Let’s review these in detail below.
Structured Threat Hunting
Structured threat hunting is a methodical and predefined approach to identifying potential threats based on specific hypotheses derived from known threat intelligence and attack patterns. This type of threat hunting relies heavily on frameworks like MITRE ATT&CK, which provide detailed descriptions of attacker tactics, techniques, and procedures (TTPs).
Threat hunters use these frameworks to systematically search for indicators of compromise and behaviors that match known adversary methodologies. By following these predefined steps, structured threat hunting ensures a comprehensive and consistent examination of the environment, facilitating the detection of sophisticated threats that align with established patterns.
The primary advantage of structured threat hunting is its ability to provide a clear, repeatable process that can be documented and refined over time. This structured approach helps organizations build a robust threat hunting capability, enabling them to continuously improve detection and response mechanisms.
Unstructured Threat Hunting
Unstructured threat hunting, in contrast, is a more flexible and exploratory approach that relies on the intuition and expertise of the threat hunter. Rather than following a predefined path, hunters use their knowledge, experience, and creativity to investigate anomalies, suspicious behaviors, and other unusual activities within the network.
This approach allows for a broader exploration of the environment, empowering hunters to uncover novel or emerging threats that may not fit into established patterns or frameworks. The unstructured method is particularly valuable for discovering zero-day exploits, advanced persistent threats, and other sophisticated attacks that evade traditional detection mechanisms.
By thinking like an attacker and exploring the network from various angles, threat hunters can identify vulnerabilities and threats that would otherwise remain hidden. While this approach can be more time-consuming and requires highly skilled personnel, it significantly enhances an organization's ability to detect and respond to evolving and unique threats.
Situational or Entity-Driven Threat Hunting
Situational threat hunting focuses on investigating threats in response to specific events, incidents, or changes in the threat landscape. This type of hunting is triggered by situational factors such as newly discovered vulnerabilities, alerts from security tools, changes in the organization's environment, or intelligence about emerging threats targeting similar industries or regions.
The goal is to quickly assess and mitigate any potential risks associated with these specific scenarios.
This targeted approach allows organizations to rapidly respond to immediate threats and minimize potential damage. Situational threat hunting leverages real-time intelligence and contextual information to prioritize and guide hunting activities, ensuring that resources are focused on the most relevant and pressing threats.
By adapting to the current threat environment, this method helps organizations maintain a dynamic and responsive security posture, strengthening their ability to protect critical assets and infrastructure in an ever-evolving industry.
Choosing the Right Threat Hunting Tool for Your Business
Once you have an idea of how you want to conduct your threat hunting, you’ll then need to choose the actual tools that you’re going to implement.
Managed Detection and Response
Managed detection and response (MDR) is a comprehensive cybersecurity service that combines advanced threat detection technology with human expertise to provide continuous monitoring, threat hunting, and incident response.
MDR services are typically outsourced to specialized security providers like an MSSP who use a combination of automated tools and skilled analysts to identify and respond to threats in real time. The importance of choosing the right MDR service lies in its ability to offer expert-level protection without the need for extensive in-house resources.
For businesses lacking a robust internal security team, MDR provides an effective way to enhance their security posture and ensure rapid response to threats.
Selecting the right MDR provider involves evaluating your technology stack, response capabilities, and the expertise of your analysts. A good fit will align with your business's specific security needs, offering tailored services that address your unique threat landscape and compliance requirements.
Security Information and Event Management
Security information and event management (SIEM) systems aggregate and analyze log data from various sources within an organization’s IT environment to detect suspicious activities and potential security incidents. SIEM tools provide a centralized platform for monitoring, correlating events, and generating alerts based on predefined rules and advanced analytics.
The importance of choosing the right SIEM tool lies in its ability to handle large volumes of data efficiently, provide actionable insights, and integrate seamlessly with existing security infrastructure.
When selecting a SIEM solution, businesses should consider factors such as scalability, ease of integration, and the quality of threat intelligence it offers. A well-chosen SIEM tool will enhance the organization's ability to detect and respond to threats quickly, minimize false positives, and provide comprehensive visibility into the security environment.
This is particularly crucial for large enterprises with complex networks and numerous data sources.
Security Analytics
Security analytics involve using data analysis techniques and advanced algorithms to detect, predict, and respond to security threats. Security analytics tools leverage big data and machine learning to identify patterns and anomalies that indicate malicious activity.
The importance of choosing the right security analytics tool lies in its ability to provide deep insights into potential threats, enabling proactive threat hunting and informed decision-making.
When evaluating security analytics tools, businesses should focus on the tool's ability to process and analyze large datasets in real time, its machine learning capabilities, and the quality of its threat intelligence.
The right tool will significantly improve the organization's ability to detect subtle and sophisticated threats that traditional methods might miss, providing a more robust and proactive security posture. Additionally, it should integrate well with existing security systems and provide intuitive visualizations and reporting to aid in threat analysis and response.
How AI Is Changing Threat Hunting
Artificial intelligence is fundamentally reshaping threat hunting by accelerating detection, enhancing accuracy, and uncovering patterns that would be impossible for human analysts to identify alone. Traditional threat hunting often relies on rule-based systems and manual investigation, which can be slow and reactive. AI, by contrast, enables proactive and adaptive threat detection.
Machine learning algorithms can sift through vast volumes of network data in real time, flagging anomalies and behaviors that deviate from established baselines. This helps threat hunters prioritize high-risk alerts and focus their investigations on the most credible threats.
Perhaps, most importantly, AI improves over time. As models ingest new data and learn from analyst feedback, they become more effective at distinguishing between benign activity and actual threats, reducing false positives and increasing efficiency. This allows security teams to cover more ground with fewer resources while staying ahead of increasingly sophisticated adversaries.
By automating the heavy lifting and amplifying human expertise, AI is turning threat hunting from a reactive task into a strategic advantage.
Final Thoughts on Threat Hunting in Cybersecurity
If your cybersecurity team has no way of recognizing threats as they enter the network, there’s no way for them to defend against those attacks. This is what makes threat hunting such an important part of a comprehensive and layered security strategy.
By actively finding, identifying, and building defenses against new and emerging threats, you can greatly improve the security of your network while also helping to further the collective fight against cybercrime.
While technology amplifies our capabilities within cybersecurity, the human stays at the centerfold of the picture. To help your staff remain secure and avoid falling victim to a phishing scam, review DOT Security’s 6 Things to Look Out for to Avoid Phishing Scams.
