Cybersecurity Consulting
What is Data Risk Management?
July 25, 2024
7 minute read
With more data being stored digitally than ever before, businesses must recognize the importance of protecting their data and establishing a strong data risk management strategy that keeps their information secure, their organization compliant, and operations smooth.
In broad terms, data risk management is the collection of procedures employed by organizations to minimize risk when accessing, storing, transferring, analyzing, and protecting sensitive data.
Sign up for our newsletter!
A data risk management strategy minimizes the risk of data being exposed to bad actors and helps make it easier for those within an organization to access that information. Businesses with strong data risk management protocols are more organized, more secure, and more productive, using data more effectively to inform decisions while also prioritizing security.
If you want to check on the cybersecurity posture of your organization, take a minute to review DOT Security’s Cybersecurity Checklist: How Covered is Your Business?
Why is Data Risk Management Important?
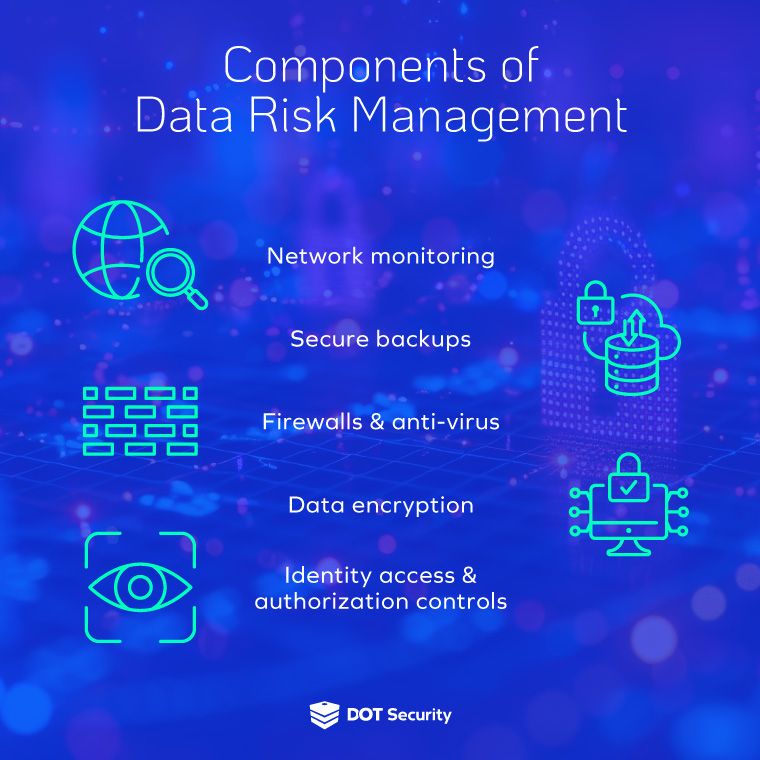
Ensuring the safety and accessibility of company data is a pillar of cybersecurity and is crucial for collaboration, business productivity, and more. By prioritizing data risk management tactics in your cybersecurity posture, you’ll be able to minimize risk associated with your data and sensitive company information.
Data risk mitigation is vital in today’s economy wherein data is extremely valuable and plays a role in almost every facet of operations. From planning, to execution, to analysis – data is crucial.
Keeping this in mind, here are just a few of the reasons that focusing on data risk management is so important for businesses today:
Businesses Have More Digital Information Than Ever
Modern businesses are storing more data than ever before in the cloud, which calls for improved cybersecurity and data risk management measures to assure that data is protected from breaches, backed up in case of corruption, and yet still easily accessible for the people who need it.
Over 60% of corporate data is stored in the cloud currently and it’s predicted that there will be over 100 zettabytes of data (or half the world's total data) stored on the cloud by 2025.
Cyberthreats are More Complex and More Frequent
A big part of data risk management is rooted in security tactics that prevent sensitive company data from being exposed, stolen, damaged, or corrupted.
Because cybersecurity threats are becoming so much more sophisticated and commonplace amongst businesses, it’s vital that organizations stay current when it comes to addressing their cybersecurity needs. Staying on top of cybersecurity is especially crucial when you consider how fast cyberthreats are advancing.
Recovering from a cyberattack without a data risk management strategy is expensive — costing an average of $170,000 to resolve a breach without accounting for downtime – but that’s not the only risk involved. An organization’s reputation can also suffer amidst a severe data breach or cyberattack.
The cost of downtime for a small business is anywhere between $137-$427/minute whereas this figure can reach $5,600-$9,000/minute for larger organizations.
Common Data Risk for Businesses
Data risk management is really all about risk mitigation and responsible data use. This means setting up protocols and operational processes that put data security first.
This means setting up responsible processes for the collection, storage, and access of sensitive data. Let’s explore some of the common risks associated with data that organizations need to consider.
1. Human Error and Lack of Employee Training
Phishing and other cyberthreats that stem from human error or employee manipulation are the most common forms of cybercrime, especially against businesses.
The strongest defense against this is a well-educated workforce who is aware of the common cyberthreats and scams and who know what red flags to look for so they can avoid falling victim to scams and/or exposing sensitive information.
Human error and employee manipulation is the most common cause of data breach amongst businesses, as human beings remain one of the weakest links in an overall cybersecurity posture. Deploying cybersecurity trainings on a regular basis helps instill a culture of security and a security-first mindset amongst employees which can help your organization avoid the vast majority of cyberattacks.
2. Lack of Device Protection
Mobile devices are pervasive in modern business environments, but unfortunately, so is the lack of protections afforded to them.
Endpoints such as smartphones, laptops, printers, IoT devices, and even smart appliances like refrigerators can be network enabled. And, in turn, every device on a network needs to be protected. This is a major discussion in operational technology right now, as cybersecurity professionals work to create segmented networks that don’t hinder integrated tech-based solutions.
Devices that remain unsecured pose a threat to the network, as they expand the attack surface of the organization and act as a potential entry point for bad actors to enter the network, move laterally, and exploit its vulnerabilities.
3. Lack of Policies and Standards
The majority of companies today have to abide by one compliance regulation or another, which typically call for the implementation of security standards and protocols that ensure data risk management and other data security practices are adopted.
Preparing for the future of industry regulations is vital for organizations who want to future-proof their operations, as more and more industries look to standardize data-management-practices for security purposes.
Organizations that don’t meet industry regulations regarding data security are not only more prone to effective cyberattacks, but they also open themselves up to legal action, fines, and other disciplinary action according to the established regulations.
Key data risks like the three listed above pose significant threats to organizations all over the United States, and should be mitigated with some sense of urgency.
Data Risk Management Best Practices
When instilling a security-first mindset that prioritizes data risk management, you don't want to spend excess time or resources reinventing the wheel. There are already established best practices for data risk management that you can look to for guidance.
Some of those best practices include:
1. Educate Workforce
Easy and secure data access is important for business growth as it allows an entire company to have the ability to utilize data when they need it.
Part of this is making sure that everyone in the company knows how to securely access, handle, and share that data without putting it at risk or leaving it exposed by educating them on:
- Creating and frequently changing their passwords or passphrases
- Using a multi-factor authentication (MFA) protocol
- Common indicators of phishing scams and other social engineering tactics
- Steps to safely use unsecured networks if necessary—particularly if employees are operating outside typical working environments
This is especially important for businesses who have a fully or partly remote team where workers could be accessing data from anywhere, including unsecured networks like home Wi-Fi setups and networks based in public places.
A best practice to follow for cybersecurity awareness amongst employees is to include a cybersecurity training as a part of the on-boarding process. Then, that initial training can be followed up with additional modules on a regular schedule.
2. Invest in Cybersecurity
Data security is a large part of data risk management because of its role in preventing breaches and protecting the network from bad actors, malware, spam, phishing attacks, and more.
The simple fact of modern cybersecurity is that it is a far more complex field today than in previous years and it effects almost every organization.
In short, cybercriminals are targeting SMBs with more frequency because the volumes of data even the smallest companies use today make them viable targets for cybercriminals. SMBs are often the most vulnerable, often lacking any substantial protocols or solutions, which makes them more vulnerable.
In-house cybersecurity can be prohibitively expensive, so investing in a cybersecurity team or partner can pay off greatly by helping businesses stay compliant with regulations, prevent attacks, and aid in recovery and remediation if an attack should occur.
3. Utilize the Cloud for Storage and Backups
Cloud technology is already extremely popular among modern businesses, and Cloud solutions are only going to become more powerful, more pointed, and more purposeful. Organizations, too, are going to need to take the next step into the era of the Cloud and be clever about the way they optimize Cloud solutions.
However, storing data on the Cloud doesn’t automatically make you secure. Having back-up protocols powered by Cloud technology in your organization will help your company restore operations in case of a data-disaster or cyber emergency. The more frequent your data is backed-up on the Cloud, the less devastating a data-breach or downtime will be.
Modern cloud storage solutions—usually hosted in Tier III and IV data centers—provide secure and scalable options for organizations, and this technology will continue to improve. However, it’s crucial that organizations deploy supplemental security strategies that address cloud-based vulnerabilities.
4. Ensure Compliance with Current Regulations
Staying compliant with the most up-to-date regulations can feel like a constantly moving target as regulations change, more standards are created, and more laws are established every year.
Relevant regulations and industry standards change based on a company’s location, customer location, industry, and products or services manufactured and sold. Failing to meet compliance with the appropriate regulations can result in large fines, loss of business, subpar data protections, and more.
Cybersecurity professionals recommend conducting regular compliance audits on a yearly basis to ensure that the current setup is appropriate when accounting for any changes to standard IT infrastructure or data regulations.
An estimated 61% of organizations have experienced a compliance-related violation like the stealing of sensitive data in contravention of privacy laws.
5. Implement Access Controls
Managing data means managing who can access that data.
Businesses can control the who, when, and how of data access by implementing identity management protocols that monitor data usage across the company, network enabled devices, and personnel access to different data segments.
Proper data risk management operates under the assumption that access to sensitive data should be restricted to only those employees who absolutely need it. By segmenting data and restricting access to those who need it the most, businesses can avoid simple cybersecurity threats.
Furthermore, segmenting your network and implementing proper identity and access management protocols will mitigate the damage imposed by a successful cyberattack, if one should penetrate your network. In turn, the attack surface of the company’s security posture is decreased dramatically, which is partially why identity and access management controls are so crucial in data risk management.
Insider data breaches are predicted to account for one-third of all cybersecurity incidents, with many SMBs having weak access controls and authentication protocols.
6. Establish a Disaster and Recovery Plan
A disaster and recovery plan is a crucial component in data risk management, providing a structured approach to respond to and recover from data breaches, system failures, natural disasters, or other catastrophic events. The plan outlines specific procedures and actions to minimize data loss, maintain business continuity, and ensure the swift restoration of critical systems and data.
Key elements include data backup strategies, clearly defined recovery objectives (such as Recovery Time Objectives and Recovery Point Objectives), and detailed roles and responsibilities for the response team. By proactively preparing for potential disasters, organizations can significantly reduce downtime, mitigate financial losses, and maintain customer trust.
7. Implement Network Monitoring and Threat Identification
Network monitoring and threat identification play a pivotal role in data risk management by providing continuous oversight of an organization’s digital infrastructure. Network monitoring involves the real-time tracking of network activity to detect anomalies, performance issues, and potential security threats.
This allows IT teams to identify and address issues before they escalate into major problems, thereby reducing the risk of data breaches, downtime, and loss of sensitive information. Advanced network monitoring tools can analyze traffic patterns, detect unusual activities, and generate alerts for suspicious behaviors, enabling swift and targeted responses to potential threats.
Threat identification, on the other hand, involves recognizing and analyzing potential security threats to determine their nature and origin. This process includes using tools such as intrusion detection systems (IDS), intrusion prevention systems (IPS), and threat intelligence platforms to identify malicious activities like unauthorized access attempts, malware infections, and phishing attacks.
By continuously assessing the network for vulnerabilities and emerging threats, organizations can develop and implement effective countermeasures, such as patching security holes, updating firewall rules, and enhancing access controls.
Together, network monitoring and threat identification create a robust defense mechanism, allowing organizations to maintain the integrity, confidentiality, and availability of their data.
How Can Businesses Build a Data Risk Management Plan?
A holistic data risk management strategy is full of many moving parts, complicated processes, and lots of room for human error.
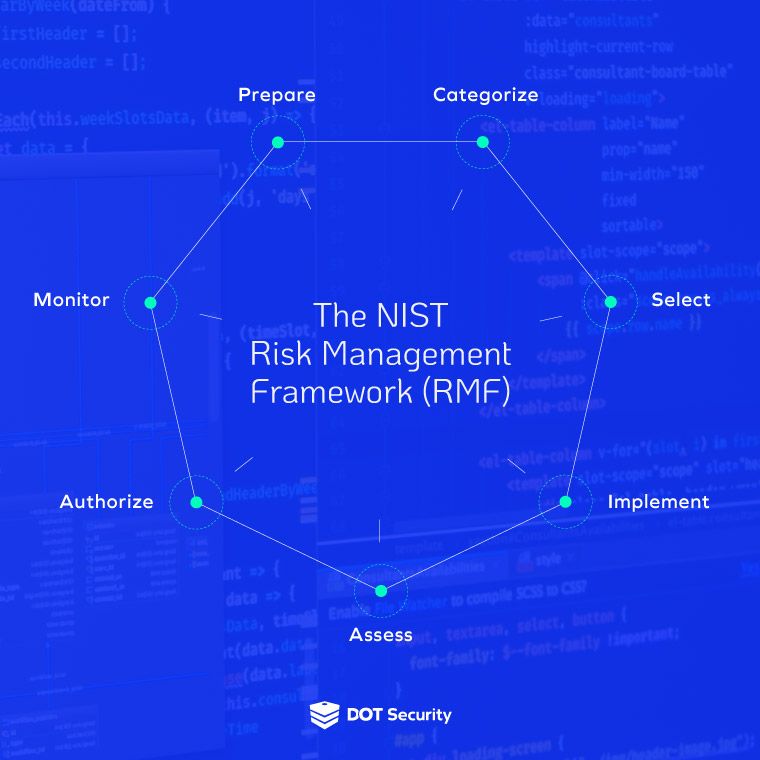
Businesses can build their own data risk management plan by following best practices related to established protocols (like the NIST framework), and by establishing strong procedures for data access and usage, or they can establish a strategic partnership and rely on a dedicated team of experts who can walk them through the development and implementation of a powerful and comprehensive data risk management strategy rooted in cybersecurity best practices.
Wrapping Up on Data Risk Management
Having a strong data risk management plan means a company is doing everything it can to protect its most valuable data during all phases of its life from collection to storage to day-to-day use. Businesses with these plans are prepared for anything and are ready with recovery protocols to minimize downtime and the costs associated with data breaches.
By investing in your organization’s cybersecurity posture, like backup & disaster recovery services, you're showing staff, clients, and stakeholders of all levels that you’re dedicated to keeping their sensitive data secure in every situation.
Data risk management is just one component of a comprehensive cybersecurity strategy. To gauge how your current cybersecurity posture holds up, take a minute to review DOT Security’s Cybersecurity Checklist: How Covered is Your Business?
